(19/04/23) Blog 109 – Get prepared, Spandex Tempest is out to get you!
Yesterday (18/04/23) Microsoft announced that they had a new taxonomy for naming threat actors they track.
According to the announcement, the new taxonomy is intended “to bring better clarity to customers and other security researchers already confronted with an overwhelming amount of threat intelligence data”.
Whilst on the surface, this does seem like a very good idea, and when you start to read into the reasoning behind their work, it does all sound quite a good idea.
Five key groups
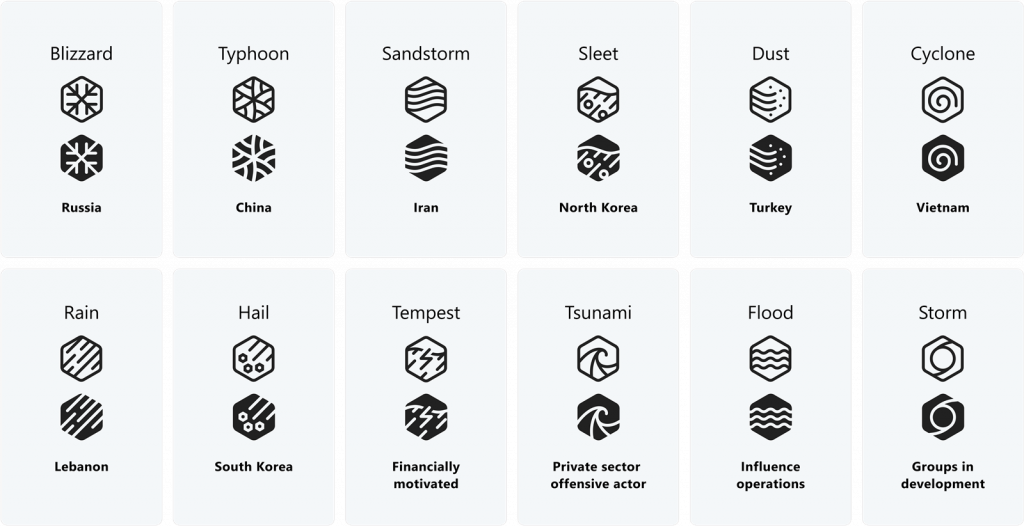
In the new taxonomy, Microsoft have defined five key groupings for the threat actors, based on the types of activity the threat actors demonstrate:
- Nation-state actors: cyber operators acting on behalf of or directed by a nation/state-aligned program, irrespective of whether for espionage, financial gain, or retribution. Microsoft has observed that most nation state actors continue to focus operations and attacks on government agencies, intergovernmental organizations, non-governmental organizations, and think tanks for traditional espionage or surveillance objectives.
- Financially motivated actors: cyber campaigns/groups directed by a criminal organization/person with motivations of financial gain and haven’t been associated with high confidence to a known non-nation state or commercial entity. This category includes ransomware operators, business email compromise, phishing, and other groups with purely financial or extortion motivations.
- Private sector offensive actors (PSOAs): cyber activity led by commercial actors that are known/legitimate legal entities, that create and sell cyberweapons to customers who then select targets and operate the cyberweapons. These tools threaten many global human rights efforts, as they have been observed targeting and surveilling dissidents, human rights defenders, journalists, civil society advocates, and other private citizens.
- Influence operations: information campaigns communicated online or offline in a manipulative fashion to shift perceptions, behaviors, or decisions by target audiences to further a group or a nation’s interests and objectives.
- Groups in development: a temporary designation given to an unknown, emerging, or developing threat activity that allows Microsoft to track it as a discrete set of information until we can reach high confidence about the origin or identity of the actor behind the operation. Once criteria are met, a group in development is converted to a named actor or merged into existing names.
Further to the groupings of the threat actors, Microsoft have generated new headline titles for threat actors from specific countries.
In the past, the Industry have typically used titles such as Bear to describe a group from Russia, and Panda for those from China – which sort of make sense.
Microsoft have decided to use the theme of weather-related items for their new titles:
Board room giggles
Whilst all this sounds great on paper, its when you now see what Microsoft have ended up calling some of the Threat groups under this new taxonomy.
I really cannot believe anyone had a straight face round the board-room table when deriving some of these names…
- “Aqua Blizzard”
- “Pink Sandstorm”
- “Gingham Typhoon”
- “Denim Tsunami”
- “Tomato Tempest”
- “Periwinkle Tempest”
- “Marigold Sandstorm”
And my favourite – the title of this post – Spandex Tempest!
Really?
I had a go at getting the new Bing Image generator AI to draw some of the new Threats…



For some reason Bing decided that “Spandex Tempest” was in breach of its guidelines, so I tried to use Midjourney to draw the same, but I’m all out of credits on there.
Eventually I turned to hotpot.ai which drew this (which is actually pretty good) – Looks like a Marvel character!













