(14/04/23) Blog 104 – We all hate a Queue Jumper right?
Microsoft have just released their monthly set of security updates, and included among the 97 security fixes is one which is classed as a critical vulnerability which if exploited can allow an attacker to perform an RCE (Remote Code Execution).
Dubbed “QueueJumper”, CVE-2023-21554 affects the Microsoft Message Queuing (MSMQ) technology which enables applications running at different times to communicate across networks and systems that may be temporarily offline.
Applications send/receive messages to & from queues – a queue is a logical container managed by MSQM to temporarily hold data coming from, or going to a specific application. By using queues, a developer can free up an applications resources rather than have it wait for a response from the destination application.
The following illustration shows several applications sending messages to a queue and several other applications reading the messages in the queue. (Directly accessing the directory service is not required; messages can be sent to the queue and read from the queue without accessing the directory service.)
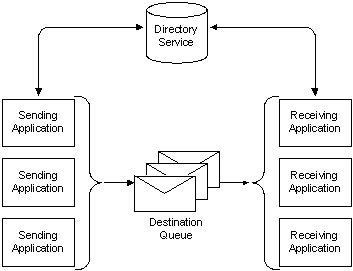
When MSQM is enabled on a Windows device, TCP port 1801 will be listening on the host.
The CVE-2023-21554 vulnerability allows an attacker to potentially execute code remotely and without authorization by sending just 1 packet to TCP port 1801.
MSQM is legacy though right?
The most recent Microsoft documents which discuss the service were updated in 2016, and many people consider MSQM a “forgotten” or “legacy” service, MSMQ is still available on ALL Windows operating systems.
Although now provided as an optional Windows component, users can easily enable the service via the Control Panel or via PowerShell command “Install-WindowsFeature MSMQ-Services”.
However, when following the official setup wizard for Microsoft Exchange Server, the setup app enables the MSMQ service in the background if the user selects the option to “Automatically install Windows Server roles and features that are required to install Exchange” – which is the option recommended by Microsoft.
Large pool of vulnerable devices
Check Point Research, who discovered the flaw, scanned the Internet and identified ~360,000 IP addresses with port 1801 open with the MSQM service listening .
Protecting systems
It is recommend that all Windows administrators check their systems to see if the MSMQ service is installed and if it is needed.
For those which do require MSMQ services, it is highly recommend users install Microsoft’s official patch as soon as possible.
In the interim, block any inbound connections for 1801/tcp from untrusted sources with Firewall rules.












