(10/04/23) Blog 100 – Can you steal a car? – Yes you CANbus
Today, I’m having some work done on my car – nothing major, just a repair to a windscreen chip I picked up whilst out driving the other day. But having this work done, made me think about a post I saw the other day about a novel way of stealing modern vehicles.
If you’ve been following my posts so far this year, you may remember I made a post back in January about how thieves can steal a modern car by accessing the CANBus without needing any keys.
In that post I mentioned that there is a physical way to stop this sort of attack, which is to purchase a CANbus port lock (AKA OBD-II port protector).

Well, as is always the case – when the world of security comes up with a new control to prevent criminals from carrying out their trade, the criminals come up with a way of defeating said control.
The article which lead to me making this post was one which showed how the simple removal of a headlight from a Toyota Rav4 can lead to it being stolen in a matter of minutes.
In the article, Dr. Ken Tindell, CTO of Canis Automotive Labs writes about the investigative work he did to solve the puzzle of why his friends car was seemingly the victim of some random vandalism over a period of a few months before actually being stolen.
In a twitter post, Dr Tindell’s friend Ian Tabor posted about the mindless vandalism he discovered one day when he went to his car:
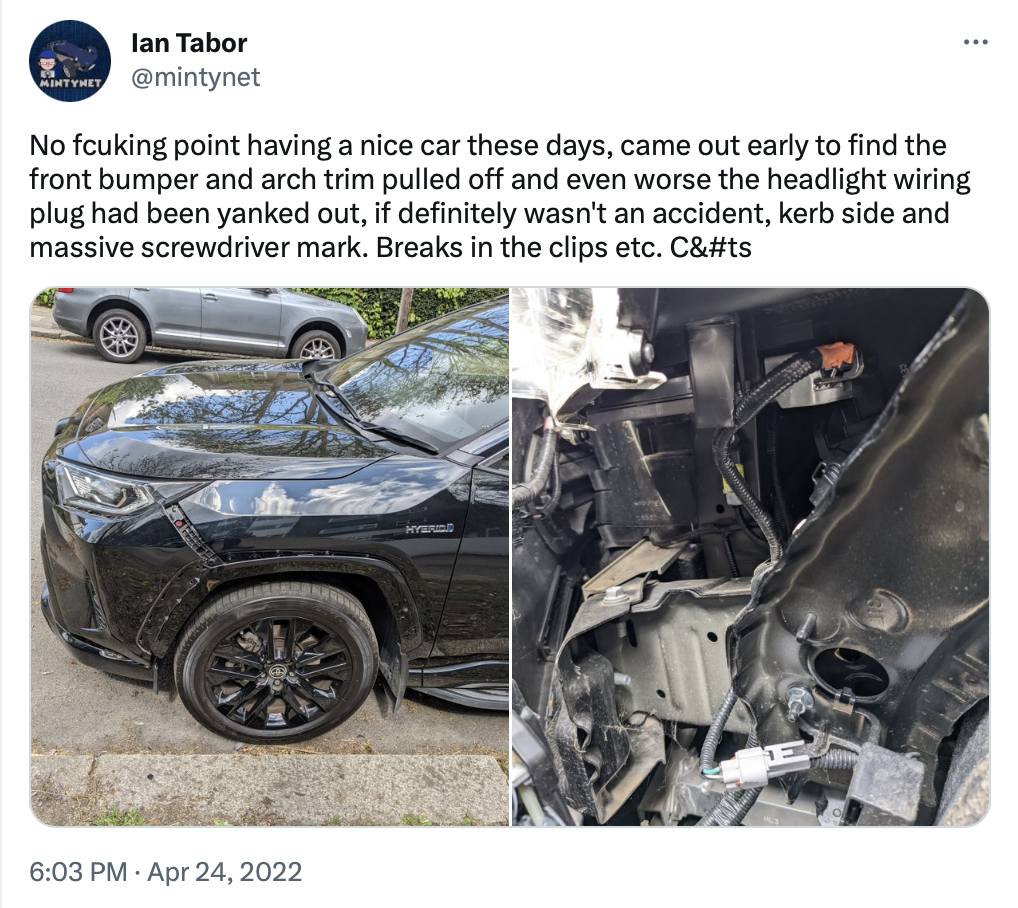
After the 1st incident, the car owner had it repaired, only to find a similar attack just three months later:
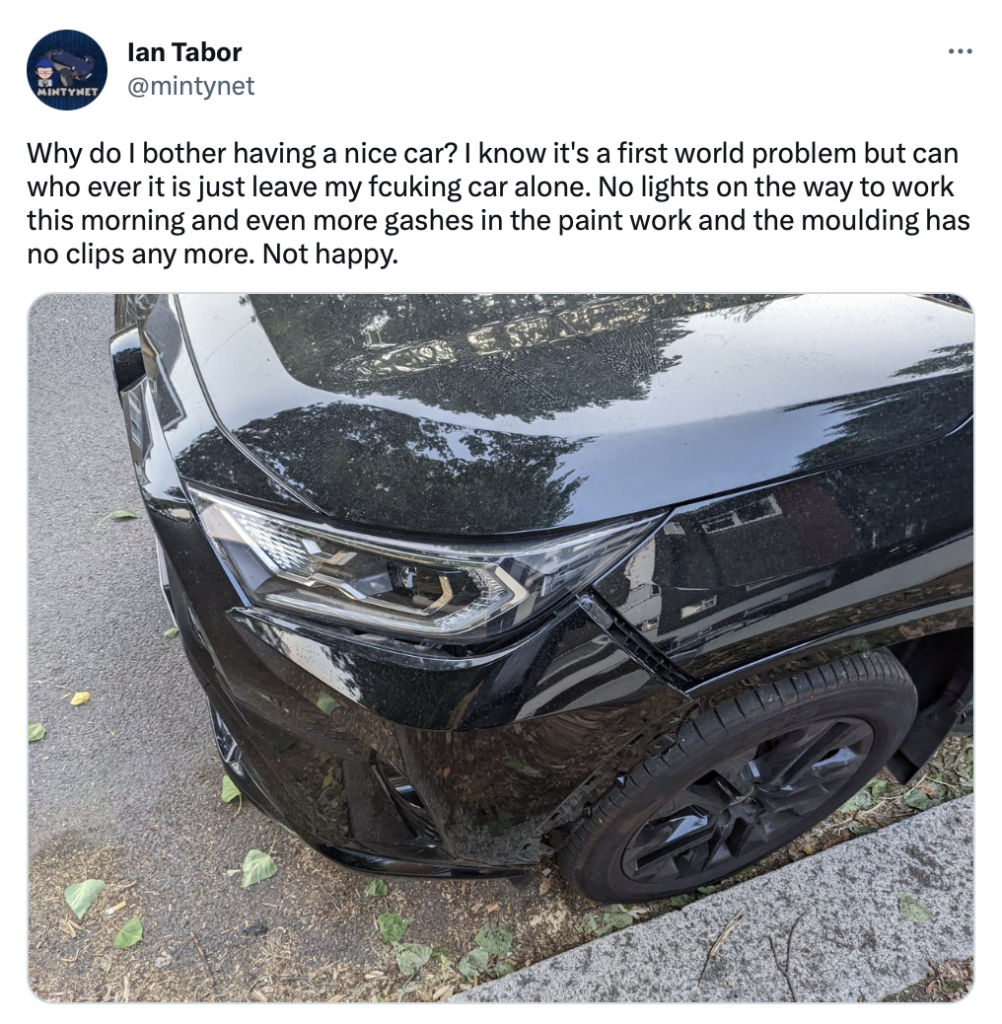
Just a couple of days later, the car was gone:
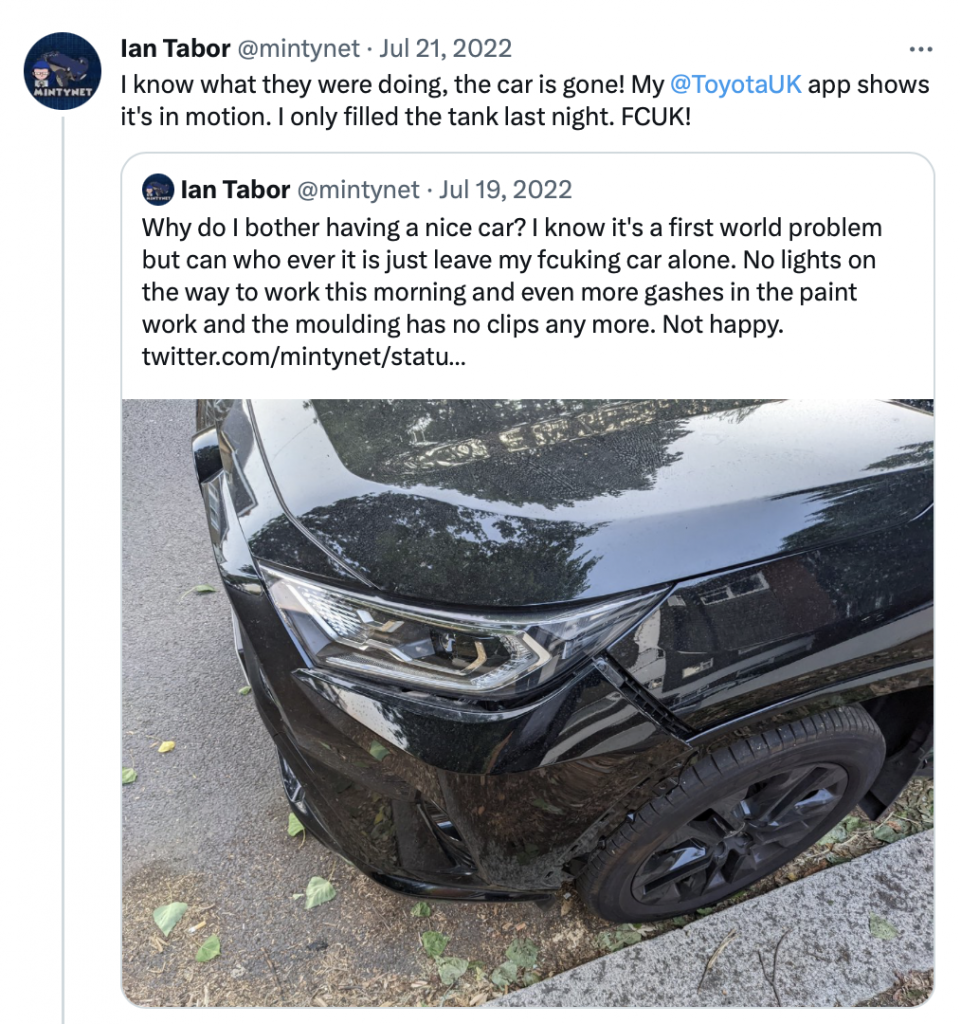
Analysis of the theft
After discovering a hole where his car used to be, Mr Tabor and Dr Tindell started to take a deep look at what the link was between the previous months worth of odd vandalism and the actual theft.
A number of Toyota vehicles have a telematics system called “MyT” which can display its data in the accompanying MyT app. This app displays data from the cars CANBus and can be useful in helping diagnose any fault with the vehicle.
By analysing the data from the CANBus, the pair started to unravel the activities which had lead to the car being taken.
Dropping a DTC
When an Electronic Control Unit (or ECU) in a vehicle detects a fault, it records a code in an EEPROM – It’s these codes which help technicians diagnose where the fault may lie.
In the automotive industry, the recording of these codes is called ‘dropping a DTC’ (or Diagnostic Trouble Code).
Analysis of the stolen Toyota’s data showed that around the time of the theft, the vehicle dropped a number of DTCs – all from the ECU which controls the cars headlights.
In his post, Dr Tindelll says:
“In the front of the RAV4 there is an ECU that controls the lights (the high and low beam headlights and the turn indicators). In most cars there is such an ECU because the days of there being a simple switch to turn on lights are long gone: lights are smart, and include things like motors to level the headlights (so when the car is loaded with heavy luggage, the lights are turned to compensate), steering headlights to illuminate the corners, to automatically detect if the lights have failed, to turn on pumps to spray water on the lights, and so on. And on the RAV4, it’s to also choose which LEDs in a grid are lit up to not dazzle oncoming drivers but still light the rest of the road.
The DTCs showed that communication with the lighting control ECU was lost. This isn’t surprising since the thieves had ripped the cables out of it. But the DTCs also showed that lots of systems had failed: the control of the front cameras, the hybrid engine control system, and so on. How could that be? This was the next clue: the ECUs probably hadn’t failed, but rather the communication to them had been lost, and the diagnostics had flagged this as a fault. The common factor: CAN bus.”
Dr Ken Tindell
So how was it done?
After discovering that the CANBus was the way in which the car was stolen, Dr Tindell started to research online how criminals attack the CANBus to achieve their goals, and discovered one website selling more than a hundred different products for by-passing car security.
The prices for some of the devices were in excess of €5,000 which may seem pricey for an ordinary owner, but for a gang of car thieves this is an investment that will make it’s money back with just a couple of successful thefts.
Dr Tindell discovered products targeting many car models, including those from Jeep, Maserati, Honda, Renault, Jaguar, Fiat, Peugeot, Nissan, Ford, BMW, Volkswagen, Chrysler, Cadillac, GMC – and Toyota.
For Toyota, the theft tool is a collection of electronics hidden inside a JBL Bluetooth speaker case.

This gives any thief plausible deniability: if stopped by the police, they don’t look like they are going equipped with any obvious car theft tools. All they have is a portable speaker system.
On purchasing one of the devices and opening it up for analysis, it was found that the device had been altered to include circuitry to allow the device to generate and inject CANBus data.
CANi
The way CANBus Injection works is to inject fake messages as if originating from the smart key receiver, essentially saying “Key validated, unlock immobilizer”.
In most vehicles on the road today, these internal CANBus messages are not protected by any form of authentication – the receivers simply trust them.
On the Toyota in question, the thieves simply break into the wiring for the CANbus and then use their device to send fake CAN frames on to the bus such as “Key is validated” messages as if from the smart key receiver.
The gateway ECU then repeats that fake message over to a different CANBus which sends the data to the engine control system which deactivates the immobilizer function.
The thieves can then use their CAN Injector to send a other fake CAN messages into the vehicle such as “Key is valid, unlock the doors”. So they don’t even need to damage the car to break into it: they can simply open the door, get in, and drive the car away – all without needing the key.
$10 to steal a £35K car
On receiving the fake JBL speaker, it was dismantled to find out how the system worked. It turns out that the CAN Injector components were soldered on to the original JBL circuit board and then enclosed in a big blob of resin.
Dr Tindell melted the resin away with a heat gun and managed to identify the components being used to turn the speaker into an injector.
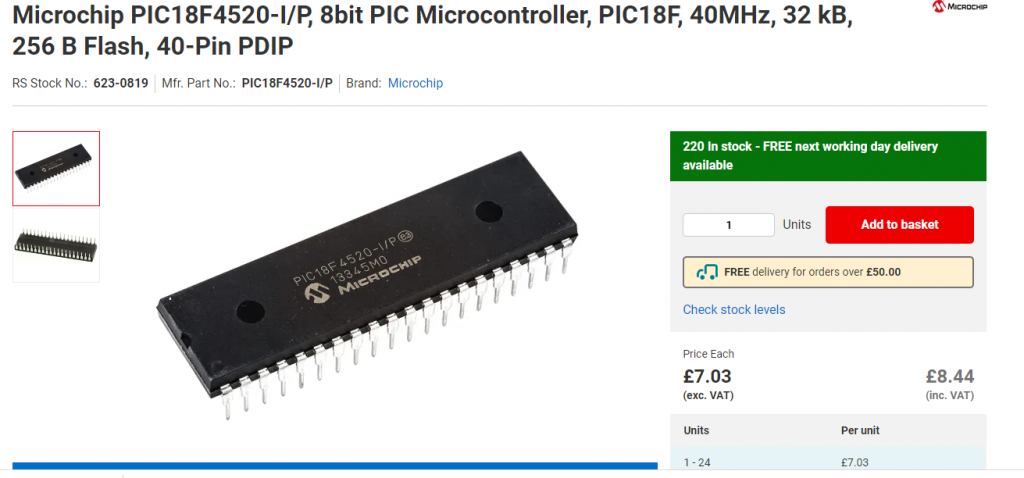
Dr Tindell identified that the injector uses approx. $10 of components:
- A PIC18F chip that contains CAN hardware, plus some firmware code
- A CAN transceiver which turns digital signals from the CAN hardware on the PIC18F into the analog voltages sent on CAN wires
- An extra circuit connected to the CAN transceiver that allows for different CAN messages to be injected
All that is needed for the injection attack to take place is access to the CANBus wires, and in most modern vehicles, the easiest access point is the headlights.
When first powered on, the CAN Injector listens for a particular CAN message to know that the car is ready.
When it receives this message it does two things. First it starts sending a burst of CAN messages (at about 20 times per second) which contains the ‘smart key is valid’ signal.
Normally, this would cause confusion on the control bus – CANBus messages from the real smart key controller would clash with the impostor messages from the CAN Injector, and this could prevent the gateway from forwarding the injected message.
The the extra circuitry in the JBL device solves this problem.
The second function of the device changes the way the CAN bus operates so that other ECUs on that bus cannot talk.
By swamping the gateway CANBus with signals, devices can still receive messages, and can still forward them on to the power train CAN bus, they just cannot communicate on the targeted section of the CANBus. Thus drwoning out any real signals which wuld otherwise cause the confusing data signals.
On the JBL speaker case is a play button which is wired into the PIC18F chip, which, when pressed, changes the burst of CAN messages slightly and can allow the criminals to send other messages to the vehicle, such as the one to instruct the door ECU to unlock the doors (as if the ‘unlock’ button on the wireless key had been pressed). The thieves can then unhook the CAN Injector, get into the car, and drive it away.
There is CCTV of this exact attack on a Rav4 taking place for a different victim – You can see the point at which the attack is successful approx. 3 minutes into the video.
Dr Tindell has reported his findings to Toyota who so far have not been back in touch, so it is unknown as to whether Toyota are working on a solution to this fairly serious issue.
For now though, as mentioned in my previous post – a physical steering wheel lock, or parking on a driveway with security bollards are just a couple of added extras you might want to think about in order to deter thefts like this.












