(03/04/23) Blog 93 – Riding the ransomware wave
Ever keen to earn a quid buck from a situation, cyber criminals are now starting to use the spectre of ransomware attacks in an attempt to extort monies with fake ransom requests.
Midnight cowboys
The scammers behind this fake attack go by the name Midnight and have been targeting companies since March 2023 according to investigators at Kroll – A US-based corporate investigation and risk consulting firm.
Kroll investigators say that organisations started filing an increased number of reports for emails received under the Silent Ransom Group name around March 23rd and say that some similar emails also included threats of DDoS attacks.
CTRL+C / CTRL+V
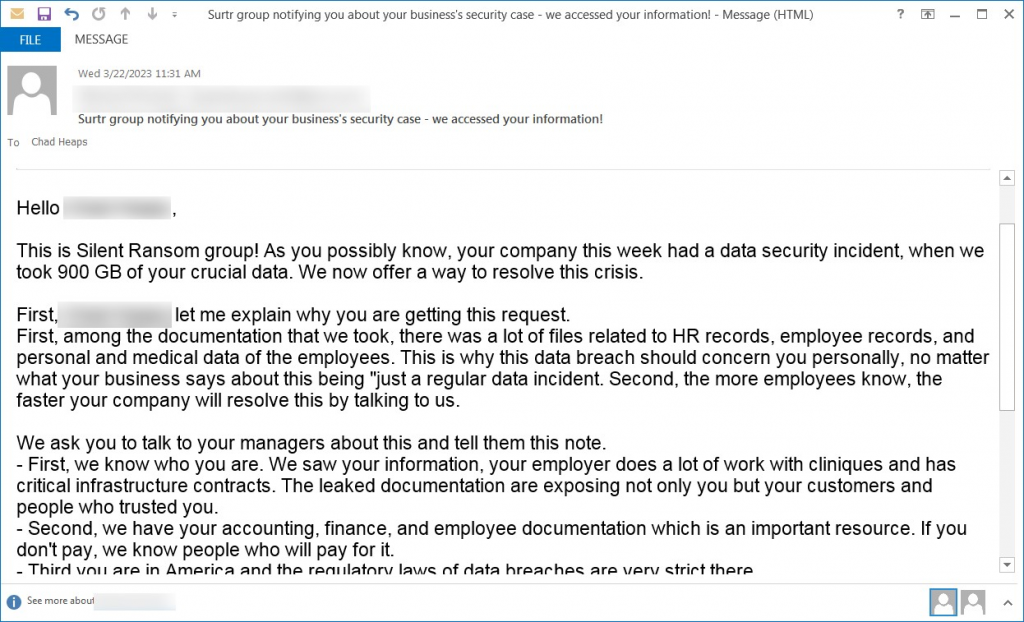
In their attempt to add legitimacy to their threats, the gang have impersonated other ransomware and data extortion gangs in their emails and claimed to be the authors of the intrusion, stealing hundreds of gigabytes of important data.
In one email, the threat actors claimed to be the Silent Ransom Group (SRG) – a splinter of the Conti syndicate focused on stealing data and extorting the victim.
However, this same message has been seen in another email, this one purportedly from the Sutr gang.
Lack of planning
It appears that the gang are using a scatter-gun approach to how they target staff of companies they attempt to extort and are not doing much by way of OSINT before hitting send.
One ransom note was sent to a potential victim, and maybe it would have been successful if it weren’t for the fact the recipient had left the company over a year before the email landed.
A separate report from incident response company Arete backs up Kroll’s observations about Midnight Group’s fraudulent emails impersonating Surtr and SRG and that Midnight seemed to be targeting organisations that had previously been victims of a ransomware attack.
According to Arete’s analysts, the initial attackers are QuantumLocker (currently rebranded as DagonLocker), Black Basta, and Luna Moth.
Arete reported that at least 15 of their current and previous clients received fake threats from the Midnight Group, who supported their data theft claims with vague details.
It is possible that targets re chosen from publicly available sources, such as data leak site, social media, news reports, or company disclosures. However, Arete notes that the fake attacker identified some ransomware victims even when the info was not publicly available, possibly indicating collaboration with other gangs.












