(02/04/23) Blog 92 – 3k bot-net rental targets Android devices
A new malware strain is targeting Android devices, and is capable of complete account takeover.
Branded Nexus, the malware is a banking app trojan and has been available to threat actors since the middle of 2022.
Nexus is one of many examples of Malware-as-a-Service (MaaS), which allows criminals to rent access to malicious tools rather than designing them personally.
Renting access to Nexus costs approximate USD $3,000 per month, but it comes with the ability to steal banking data that could net the operator much more than that.
Once a subscription is purchased, criminals gain access to a Web portal which contains a dynamic dashboard allowing the criminals the ability to interact with compromised devices. The dashboard comes complete with a built-in list of injections against 450 financial applications, giving threat actors an easy way to monitor their attacks.
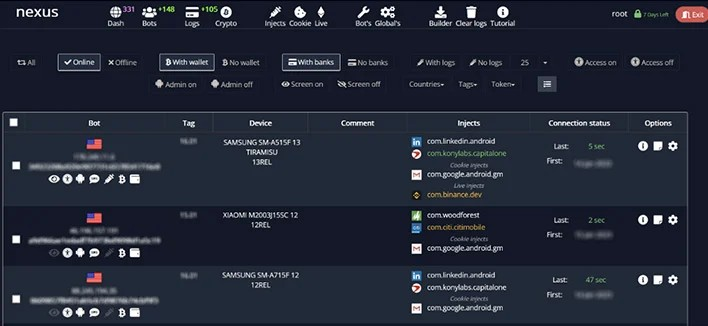
Like most tools of this nature, Nexus uses system overlays and keylogging to steal account credentials. Even accounts secured with two-factor codes are at risk—Nexus uses accessibility APIs to steal SMS verification codes, cryptocurrency wallet data, and even codes from authenticator apps.
The malware includes a remote update capability, allowing the designers to push out new capabilities as they are developed. Labelled as a Beta version, Nexus has already added a number of features since its launch in 2022.
Russian origins
As is often the case with such malware, it appears that this new tool has its origins with Russian cyber criminals. The developers state that subscribers do not attempt to use Nexus in Russia or any Commonwealth of Independent States (CIS).
The developers have implemented a geo-lock the malware to prevent its use against targets in those areas.
New code base?
The developers claim that the code has been written from scratch, with no reused code from existing malware strains, however security analysts at Cleafy, seem to think that’s not exactly true.
In their analysis of the Nexus code, technical indicators suggested some similarity between Nexus samples and SOVA, an Android banking trojan which emerged in mid-2021.
It appears that the malware authors may have reused some parts of SOVA internals, to write new features (and rewrite some of the existing ones).
The author of SOVA, who operates under the alias “sovenok”, started sharing some insights on Nexus and its relationship with SOVA, calling out an affiliate who previously rented SOVA for stealing the entire source code of the project.












