(01/04/23) Blog 91 – The Vulkan files – Russia’s own Snowden incident
A few days after Russia’s invasion of Ukraine (24/02/22), thousands of secret files were leaked to the German newspaper Süddeutsche Zeitung.
The files were form a Russian company called NTC Vulkan (НТЦ Вулкан), and describe in detail acts of cybercrime, political interference in foreign affairs (such as in the 2016 United States presidential election) through social media, censorship of domestic social media, and espionage, in collusion with Russia’s Federal Security Service (FSB), their armed forces (GOU and GRU); and Foreign Intelligence Service (SVR).
An anonymous whistle-blower who opposed the illegal war leaked the files which have since been analysed by journalists from Süddeutsche Zeitung , The Guardian, Le Monde, The Washington Post, and several other media outlets, as part of a consortium led by Paper Trail Media and Der Spiegel.
The files have also been verified by five Western intelligence agencies and several independent cybersecurity experts.
On 30 March 2023, the consortium published the first details of its investigation.
Sandworm & NotPetya
One document in the huge trove of files links a Vulkan cyber-attack tool with the hacking group Sandworm. the group which have caused blackouts in Ukraine, disrupted the Olympics in South Korea and launched NotPetya, the most economically destructive malware in history.
See my post about NotPetya for info
The tool, codenamed Scan-V, scans the internet for vulnerabilities, which are then stored for use in future cyber-attacks.
CozyBear
The leaked files also reportedly link NTC Vulkan to APT29 (AKA CozyBear). This group compromised the Democratic National Committee in 2015, and has been attributed to the SolarWinds supply chain compromise.
Iron Fist control & Disinformation
Amezit, is the codename given to another system which seems to be a multi-faceted system with various abilities, one of which is dedicated to surveilling and controlling the internet in regions under Russia’s command.
This component of Amezit is domestic-facing, allowing operatives to hijack and take control of the internet if unrest breaks out in a Russian region, or the country gains a stronghold over territory in a rival nation state, such as Ukraine.
Internet traffic deemed to be politically harmful can be removed before it has a chance to spread.
The leaked files contain a 387-page document which explains how Amezit works.
The military needs physical access to communications hardware, such as mobile phone towers, and wireless communication systems. Once they control transmission, all traffic can be intercepted. Military operatives can then identify people browsing the web, see what they are accessing online, and track information that users are sharing.
The Vulkan files contain documents linked to an FSB operation to monitor social media usage inside Russia on a gigantic scale, using semantic analysis to spot “hostile” content.
Since last year’s invasion of Ukraine, Russia has arrested numerous anti-war protesters and passed punitive laws to prevent public criticism of what Putin’s “special military operation”.
The text in the above image relates to the fact that the system can augment data over a map to allow operatives to get a visual representation of data.
Figure 69 – Displaying the integrated situation on the electronic map in the “combined” mode, without indicating the number of elements
Implementation of output functions on the electronic map when hovering over the symbol of the object of its abbreviated form
To implement the function of displaying on an electronic map when you hover over the symbol of an object of its abbreviated form, it is proposed to display the following information about the object in the operator interface:
Name;
location;Google Translated text from above image
- additional description.
- Signed and date
An example of the output of an abbreviated form on an electronic map when you hover over a symbol is shown in Figure 70.
The tool also enables disinformation via fake social media profiles.
This Amezit component allows the Russian military to carry out large-scale covert disinformation operations on social media and across the internet, through the creation of accounts that resemble real people online, or avatars.
The avatars have names and stolen personal photos, which are then cultivated over months to curate a realistic digital footprint.
The leak contains screenshots of fake Twitter accounts and hashtags used by the Russian military from 2014 until earlier this year. They spread disinformation, including a conspiracy theory about Hillary Clinton and a denial that Russia’s bombing of Syria killed civilians.
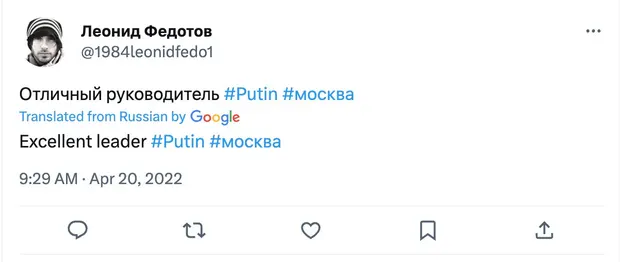
Following the invasion of Ukraine, one Vulkan-linked fake Twitter account posted: “Excellent leader #Putin”.
CNI exploitation
A third Vulkan-built system – Crystal-2V – is a training program for cyber-operatives in the methods required to attack Critical National Infrastructure (CNI).
Capable of allowing simultaneous use by up to 30 trainees, it appears to simulate attacks against a range of CNI targets including railway lines, electricity stations, airports, waterways, ports and industrial control systems.
“The level of secrecy of processed and stored information in the product is ‘Top Secret’.”
Vulkan files – Crystal-2V












