(31-03-23) Blog 90 – Wi-Fi Vulnerability discovered
Cybersecurity researchers have discovered a vulnerability in the design of the IEEE802.11 standard – This is the standard from which Wi-Fi is based.
In a paper released on Monday, the researchers say that the vulnerability allows a threat actor to trick a Wireless access point into leaking data in an un-encrypted form.
How the attack works
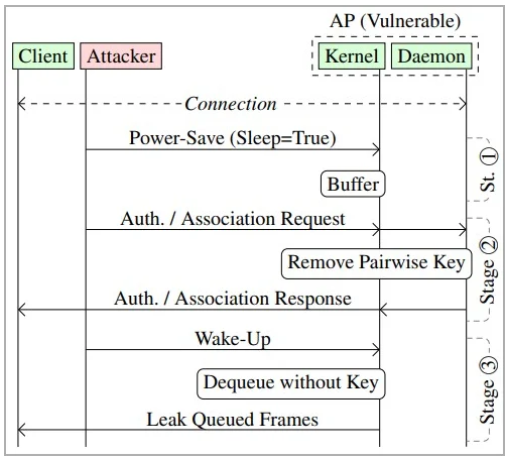
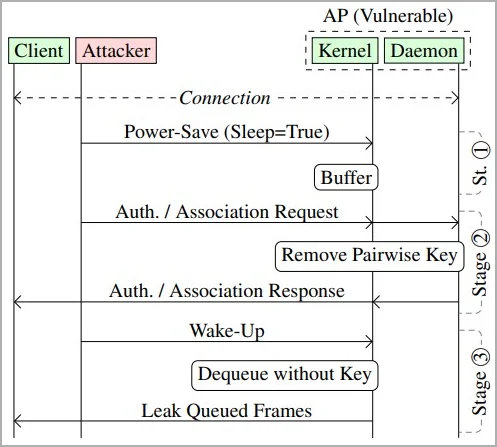
The IEEE 802.11 standard includes a number of features which allow WiFi devices to conserve power by buffering or queuing frames destined for sleeping devices.
When a receiving device is not busy managing data frames, to conserve energy it enters a sleep mode. Before doing so, it sends a data frame to the wireless access point with a header that contains a power-saving bit set. This instructs the access point to queue all frames destined for the device.
Unfortunately, the standard does not provide explicit guidance on managing the security of these queued frames and does not set limitations like how long the frames can stay in this state.
When the client station wakes up, it transmits a wake-up frame to inform the access point that it can now start to receive data once more. The access point now dequeues the buffered frames, applies encryption to them, and transmits them to the client device.
However, a threat actor can spoof the MAC address of a receiving device on the network and send power-saving frames to the access point. This has the effect of forcing the access point to start queuing frames destined for the target.
The attacker then transmits a wake-up frame to retrieve the buffered frame stack.
The transmitted frames are usually encrypted using either the group-addressed encryption key which is shared among all the devices in the WiFi network, or a pairwise encryption key, which is unique to each device and used to encrypt frames exchanged between two devices.
In this attack, the threat actor can change the security context of the frames by sending authentication and association frames to the access point, thus forcing it to transmit the frames in plaintext form or encrypt them with an attacker-provided key.