(29-03-23) Blog 88 – Protecting your online activity – Pt8
In my last post, I talked about the use of cookies by companies when they want to track our online browsing activities. Well, cookies are just one of a number of technologies used by companies to get our data. In this post, I’ll take a look at the use of web-beacons.
What’s a web-beacon?
A web-beacon (AKA Web-bug) is a technique used on web pages and in emails to unobtrusively (usually invisibly) allow checking that a user has accessed some content. Web beacons are typically used by third parties to monitor the activity of users at a website for the purpose of web analytics or page tagging.
Web-beacons have a number of uses, they can be used to see if an email was read or forwarded or if the contents of a web page is copied to another website.
So how are they used to track activity?
Before I can answer that, I need to make sure you understand how web transactions take place…
When you type a web address in a browser, or click a hyperlink, your browser sends an HTTP GET request to the web server asking for the page to be delivered.
In this request, a number of data items are sent to the web server that help smooth things along. One of the things that is sent is the browsers “User Agent” header – Something like this:-
Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/111.0.0.0 Safari/537.36
This header data tells the web server what sort of browser is making the request and what capabilities it has. This is used by the server to make sure the correct data is returned which the browser can process.
In the example above, my browser is Google Chrome running on 64-bit Microsoft Windows 10.
If you want to see your User Agent header and what each of the values presented by your browser mean, visit useragentstring.com
The user agent header isn’t the only data that is passed from browser to server, I’m using it here to illustrate a point.
There is much data which is passed from browser to server – this can include things such as installed fonts, date/time, plug-in info, screen size, operating system, and more. This collection of data is commonly known as your browser fingerprint, and like a real fingerprint, it is unique to your browser, on your device.
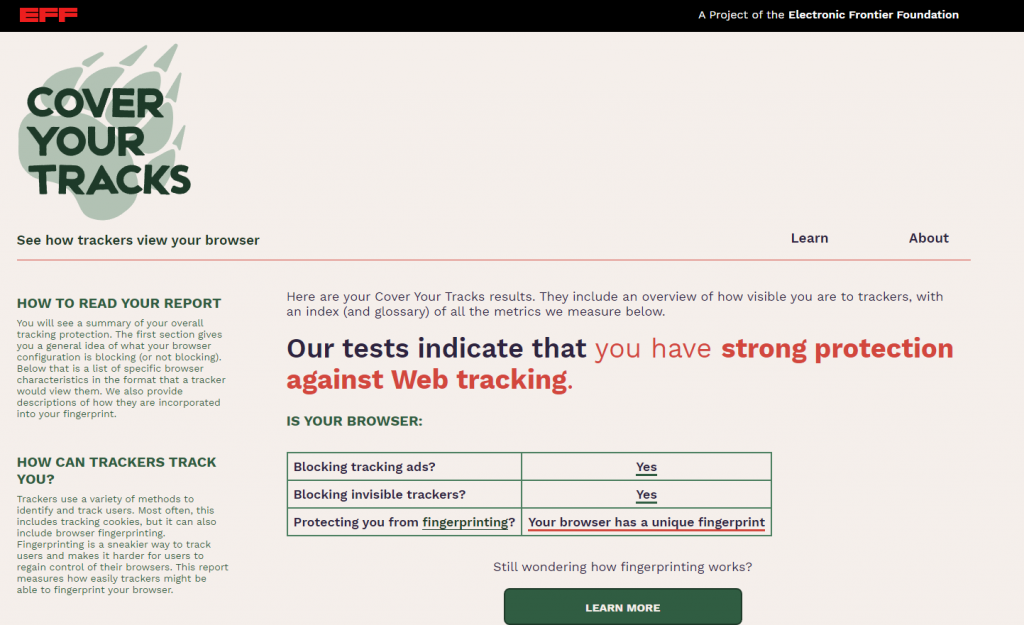
If you want to see more of the data that is passed between browser and server, visit coveryourtracks.eff.org and press the “test your browser” button.
Needless to say, my tests show that I have strong protection against tracking 🙂
But what does all this have to do with web-beacons and tracking?
When you download a webpage from a server, there will be instructions in the HTML that tell the browser to retrieve other data from different locations in order to display the page correctly. For each of the instructions, the browser will automatically instigate a new HTTP GET request.
When a page utilises web-beacons, the file isn’t in the page you visit, but rather there is a link to instruct the browser to retrieve the file from a 3rd party server.
A such, your browser will make the required HTTP GET request to that 3rd party server and reveal your browser fingerprint to the web server. The owners of this server can now see that someone with your specific browser data has viewed the page that contains the web-beacon link.
Over time, they will be able to see multiple instances of that exact fingerprint visiting various sites where they have installed their web-beacon links.
Let’s look at this activity using the example of a Facebook web-beacon.
This morning I viewed an article on the BBC news website. This site contains Facebook web-beacons, so when I viewed the site, my browser sent an HTTP GET request to the Facebook server asking for the web-beacon file. Now, to Facebook, this only means that someone with a particular set of browser attributes has looked at a specific BBC news article.
No big deal so far….
I later logged into Facebook using the same browser to check my wall posts.
As such, I sent Facebook the exact same browser fingerprint to that which I sent them earlier. This now gives Facebook the data they need to tie the two activities together. My profile is linked to my browser fingerprint, therefore Facebook can now see that I visited the BBC news article.
This type of tracker is very different to that of a cookie, and allows website owners an insight into user activity across thousands of sites without having to build thousands of different cookies.
So you can see, even without the use of cookies, a site such as Facebook can gain knowledge of your online activities.
As I mentioned at the beginning of this section, the use of Web-beacons isn’t limited to web pages though. They are readily used in HTML emails as well.
When a normal email is sent, the sender can enable tracking to let them know if the recipient has read the message or not. Unfortunately, programs such as Outlook inform the recipient that tracking has been enabled and allows the recipient to block the receipt from being sent back to the sender.
A web-beacon bypasses all this.
Email systems such as Outlook or Gmail receive HTML formatted emails and as such act in exactly the same way as a browser would in terms of generating HTTP GET requests asking for a web-beacon to be delivered.
In this way, the owner of the web-bug will get a notification that the email has been opened, because they will be able to see the request for the web-beacon.
In the next post, I’ll take a look at the use of HTMLv5 for tracking activity.












