(21-03-23) Blog 80 – Ransomware attacks too much faff? Go straight for extortion instead
Ransomware is big business, but for some threat actors, it’s not big enough.
A large number of ransomware attacks tend to use the same encryption algorithms, or ones which have only been slightly altered. As such, the number of ransomware attacks that can now be defeated with decryptors is rising.
The nomoreransom project is working wonders in this field providing over 70 decryptor tools for free.
Just last week, Kaspersky released a decrypter for the Conti ransomware which contains 258 keys, source-code, and some pre-compiled decryptors for some victims.
The decrypter has been added to the RakhniDecrypter which is available on the nomoreransom website.
As a result of this work, a number of ransomware gangs are now turning to pure extortion techniques instead.
The BianLian gang is just one which has done that.
First seen in July 2022, the BianLian gang are one of a number of threat actors to turn their hand to the Go language for their malware.
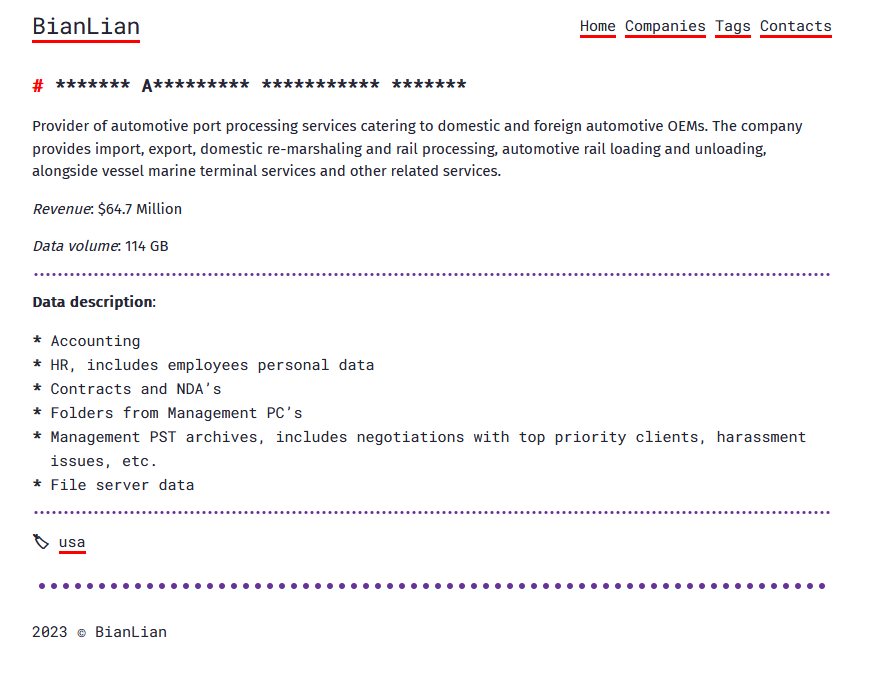
The ransomware used by the gang has targeted many well-known organizations across several industry sectors such as Manufacturing, Education, Energy, Healthcare, and Media.
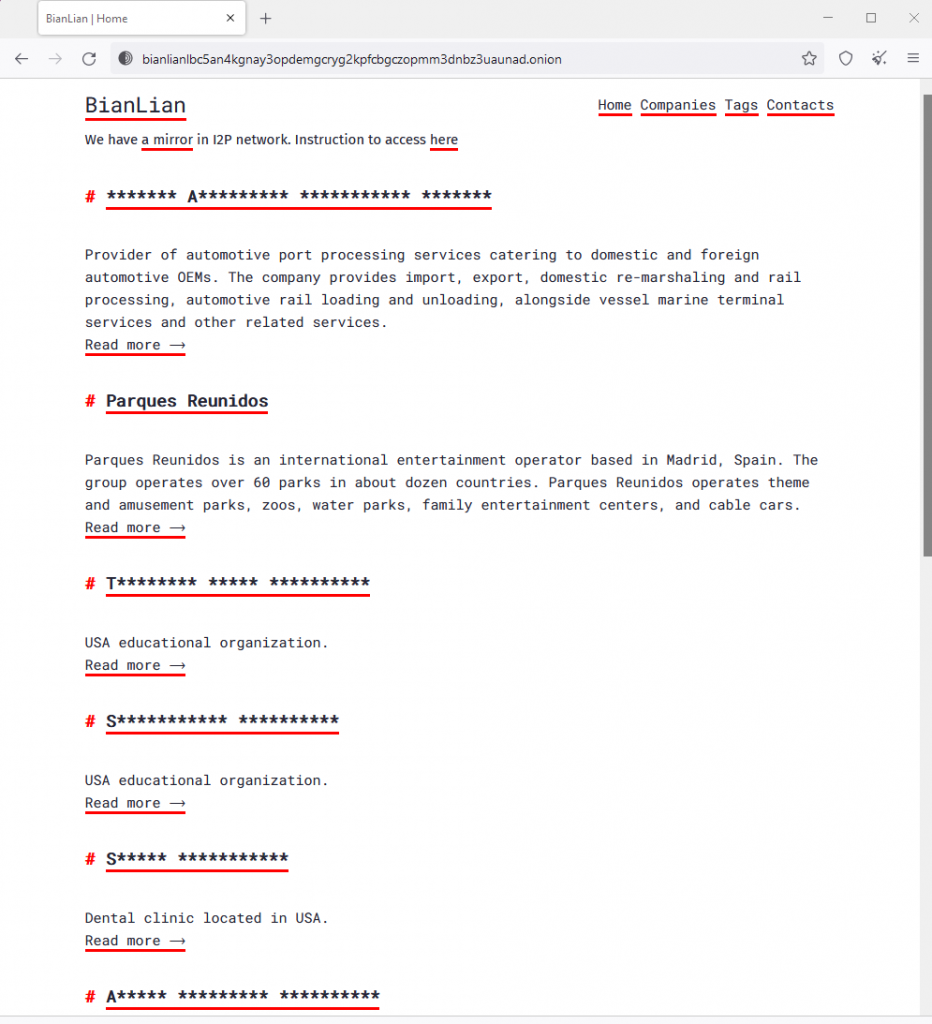
Like most gangs of this type, they use dark web sites to post their stolen data, and expose the information if companies don’t pay up on time.
BianLian decrypted
In January 2023, security firm Avast released a free decrypter for victims of the BianLian ransomware – this announcement apparently convinced the gang that it was pointless wasting time developing new code for a new ransomware tool, so they decided to go for just stealing and extorting instead.
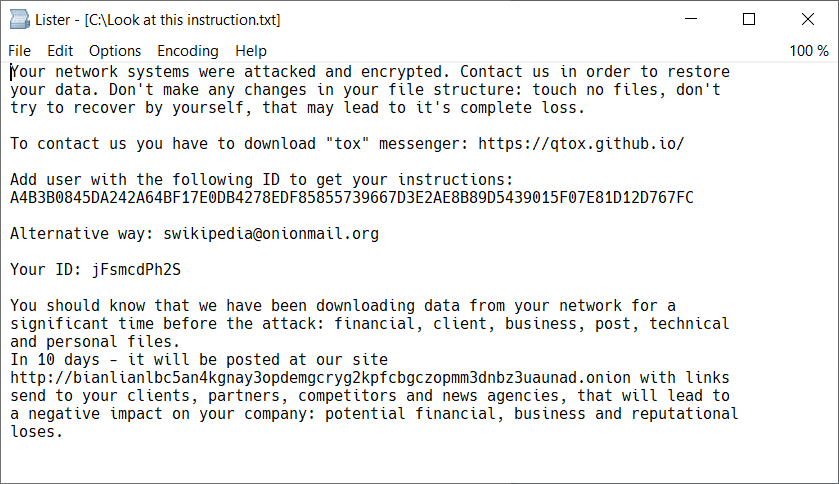
Shortly after Avast published the decrypter tool, BianLian posted a message on their site that they had unique keys for each victim and that if a victim used Avasts decrypter it would permanently corrupt the files – something which proved to be not true.
The gang has now moved away from using the ransomware and instead simply steal data and then send messages to the victims threatening to post the stolen data online of a ransom is not paid.
The group has also started tailoring its messages to victims to increase pressure on the organisations. Some of the messages make references to legal and regulatory issues facing organisations if a data breach became public, with the laws referenced appearing to correspond to the jurisdiction where the victim is located.
On their website, companies who the gang have breached have their names masked until the deadline passes, at which point the names are revealed and the data released.
Go & Malware
The reasons why malware developers are using Go (GoLang) is multi-variate.
Firstly, the language enables a single codebase to be compiled for all major operating systems. In other words, code written in Go on a Linux system can run on a Windows or a Mac.
Secondly, Its rich library ecosystem of tools and utilities smoothens the process of malware creation, making it very quick to use when producing new malware code.
Finally, although a program written in Go can be decompiled like Python or any other language, its automatic compilation feature makes it very difficult for researchers to analyse and reverse engineer.
Threat actors will adapt and grow as soon as an opportunity arises for them, or when a door closes for them. As professionals in the security space we have to keep adapting and growing as well.












