(18-03-23) Blog 77 – Meta develops new Cyber Kill Chain
Meta, the parent company behind Facebook, Instagram, and WhatsApp has released what they say is a new, more modern Cyber Kill Chain – A list of the stages and events by which threat actors prepare and conduct cyber attacks.
The Original Kill Chain
Back in 2011, Lockheed Martin developed a model for cyber attacks which most people in the industry still use today. Indeed, the term “The Cyber Kill Chain” is a registered trademark of Lockheed Martin.
The Lockheed Cyber Kill Chain has 7 stages:
- Reconnaissance – e.g. Harvesting email addresses, conference information, etc.
- Weaponization – e.g. Coupling an exploit with a backdoor into a deliverable payload
- Delivery – Delivering the weaponized bundle, e.g. via email, USB, IM, SMS, etc.
- Exploitation – Exploiting a vulnerability to execute code on the victims system
- Installation – Installing malware on the asset
- Comand & Control (C2) – Command channel(s) for remote manipulation
- Actions on Objectives – Intruders accomplish goals. e.g exfiltrate data, utilise victim system for further attacks, etc.
Why use a kill chain model?
By breaking down the stages of a cyber attack, security professionals can hone their skills and controls to better defend against an attack in a multi-layered approach – commonly called defense in depth.
Like any chain, if you can weaken one of the links, the chain is likely to fail, and thus in the context of a cyber attack, you stand a better chance of defending against any would-be attack.
Take the reconnaissance phase as an example, If you limit your data footprint, be that a digital one, or a physical one, an attacker will not have much ammunition to start launching attacks such as a spear-phishing campaign, etc.
As another example, if you can understand the tricks an attacker would use in the exploitation phase, you will be in a better position to deploy strategies to defeat them. I.e. using Network Intrusion Detection Systems (NIDS) and complex firewall rules, aligned with modern anti-malware solutions will stave off many remote exploit attacks.
The Meta Kill Chain
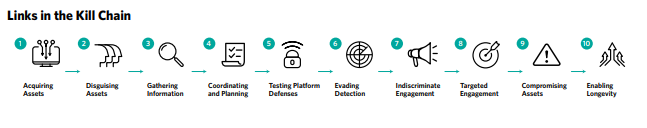
Enter Meta with their re-vamped version – “The Online Operations Kill Chain“. In this model, Meta have created 10 separate phases:
- Acquiring Assets
This refers to any instance in which an operation acquires or sets up an asset or capability - Disguising Assets
This tactic covers any action an operation uses to make its assets look authentic - Gathering Information
This covers any effort an operation makes to gather information, whether manually or by automation - Coordinating & Planning
This covers any method an operation uses to coordinate and plan its activity. This can include both overt and covert coordination and both manual techniques and automation - Testing Platform defenses
Some operations test the limits of online detection and enforcement by sending a range of content with varying degrees of violation and observing which ones are detected. - Evading Detection
Any repetitive method an operation uses to sidestep online defenses qualifies as evading detection - Indiscriminate Engagement
This tactic includes any form of posting or engagement in which the operation makes no apparent effort to reach a particular audience - Targeted Engagement
Targeted engagement, by contrast, covers any sort of method an operation uses to plant its content in front of a specific audience - Compromising Assets
An operation that attempts to access or take over accounts or information is considered to be compromising assets - Enabling Longevity
Operations that take steps to survive takedown, or to prolong their activity after exposure, are considered to be enabling longevity
In the white paper published this week, its authors – Ben Nimmo and Eric Hutchins say that the Kill Chain is “an analytic framework that is designed to be applied to a wide range of online operations – especially those in which the targets are human. These include, but are not limited to, cyberattacks, influence operations, online fraud, human trafficking, and terrorist recruitment.”
The ten phases of the new model are covered in great detail in the white paper and are showcased against real-world hacking event including:
- DCLeaks – This event saw multiple email hacks leaked to DCLeaks.com and were intended to interfere with te 2016 US Presidential election
- PeaceData – This event was a Russian-linked campaign across social media (inc. 13 Fake Facebook profiles) to fuel political chaos in the U.S.
- V_V – An Anti-Covid19 vaccine extremest group active in Europe which targeted healthcare professionals and spread mis-information across social media platforms.
”Our goal is for this new kill chain framework to allow different investigative teams across industry, civil society, and government to share and compare their insights into operations and threat actors according to a common taxonomy, giving each a better understanding of each threat and a better chance of detecting and disrupting it.”
Meta – The Online Operations Kill Chain












