(16-03-23) Blog 75 – DNS – it’s always DNS…
The Domain Name System (DNS) has been a crucial part of the Internet / WWW since its conception back in 1983.
Invented by Paul Mockapetris whilst he was a member of the Information Sciences Institute at the University of Southern California, DNS is the system which connects the human readable web addresses we use to identify Internet resources (e.g. cybertrainer.uk) with the underlying IP address (e.g. 109.228.34.178) which the Internet uses to route data to and from the service hosting the resource.
If you want to read more about the workings of DNS, please take a look at my dedicated page on the protocol here.

Unfortunately, as with most things, DNS is also a system widely used by attackers to wreak havoc on the web and the Internet.
Akamai State of the Internet
The CDN (Content Delivery Network) provider Akamai has for many years produced a report called “The state of the Internet” where they detail the research they conduct into the billions of Internet data requests they receive on a daily basis.
As the operator of the worlds largest distributed content platform, Akamai are in a privileged position to be able to “see” much of the Internets traffic on a truly staggering scale. It’s this rivaled position that allows them to produce very accurate data regarding the state of the Internet.
The latest report from Akamai is titled “Attack Superhighway:A Deep dive on Malicious DNS Traffic.” and I recommend anyone with even a passing interest in how the Internet works take a read of this report.
For those who don’t have the time to digest all the report has to offer, please carry on reading here as I will summarize the report as best I can.
Many organisations are compromised
In the report, Akamai state that according to their data, between 10% and 16% of organisations are actively compromised by threat actors. They arrive at this conclusion by examining the DNS requests emanating from those companies which are looking for the IP addresses of known C2 (Command and Control) servers. Typically, a device will only seek the IP of a C2 once it is compromised and needs to connect back to it’s handlers.
The DNS queries seen by Akamai do not allow them to understand the actual malware, or compromise on the corporate devices, but the requests themselves do reveal what the compromised devices are trying to do.
26% of the affected devices seen making requests for known C2 servers are actually trying to connect to known IAB (Initial access Brokers) domains.
An IAB is someone who compromises a network, but then sells, or gives the access to the network to other threat actors.
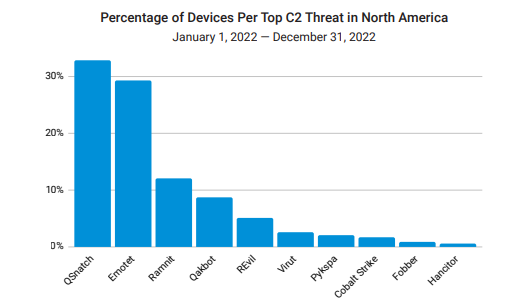
The highest proportion of devices seen globally searching for IAB DNS data are looking for the C2 servers of the Qsnatch IAB, followed by that of the Emotet and Rammit IABs.
NAS offers open doors into companies
The data analysed by Akamai suggest that 36% of affected devices in corporate networks which are attempting to connect to a C2 server are NAS (Network attached Storage) devices.
NAS drives are often forgotten about in companies, and as such they are commonly found to be unpatched, or have too many open ports which are not protected by other defenses.
As I mentioned above, the highest proportion of DNS requests looking for IAB domains are looking for IP addresses attributed to Qsnatch.
QSnatch is a malware specifically targeting NAS devices made by Taiwanese manufacturer QNAP. Once a device is infected, it will attempt to communicate with the attackers C2 servers by using a domain generation algorithm (DGA) which periodically generate a new destination domain name to avoid being tracked.
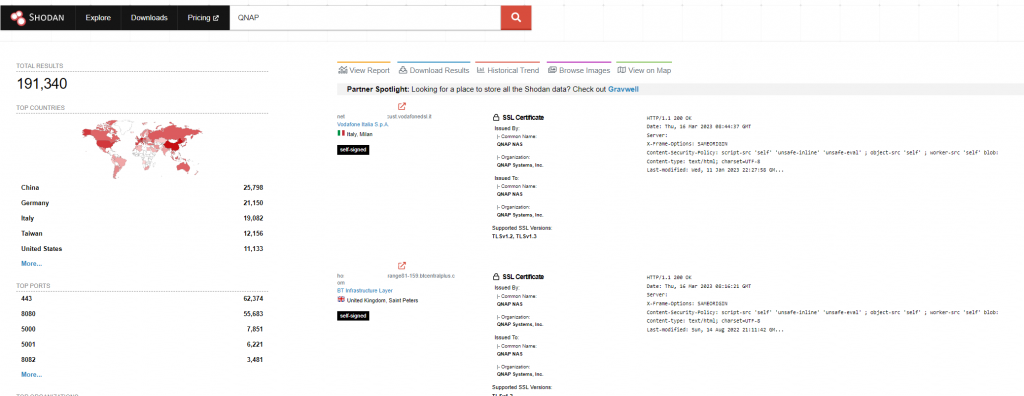
A cursory search for QNAP devices on shodan.io reveals over 191,000 devices available online with multiple open ports.
Manufacturers are big targets
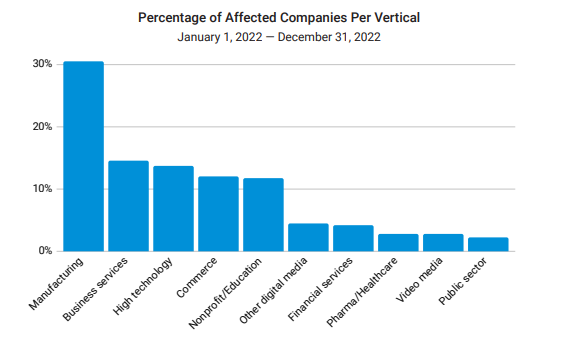
The report by Akamai highlights the different industry sectors which are the most widely targeted, and the manufacturing sector tops the list with 30% of malicious DNS requests originating from companies in that sector. This value is almost double the value from the second most widely targeted sector – Business services.
This indicates the type of data being prized by the threat actors conducting these attacks.
Home users are targets too
Corporate networks are a known entity, and so are often specifically targeted for a defined reason. Home owners however are often unknown entities, with every home having a diverse set of Internet connected devices.
However, home networks are often seen as soft targets in comparison to that of the corporate network, and so attackers will use “spray and pray” tactics to attempt to compromise as many devices as possible to “pwn” those devices into a botnet which they can the use in further attacks on other networks.
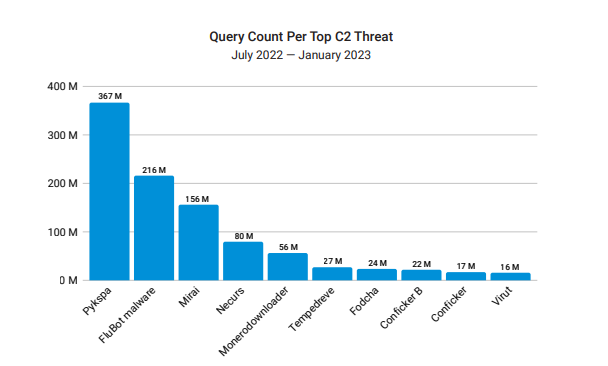
Akamai’s ability to see all types of data traversing the Internet has revealed that home networks are beginning to show heavy traffic from such botnets. Their data shows that the Pykspa botnet is currently the most prolific with 367 million DNS queries, followed by FluBot (216M queries) and our old “friend” Mirai (156M queries) coming in third place.
Criminals will try any technique to get a foothold in a targets network, and in some cases they are easy to spot and defend against, but when the attack leverages a fundamental component of how the entire Internet works, it becomes a very difficult thing to control.
As evidenced in the report, DNS is a vital part of the WWW / Internet, but is also a very fragile part of the network.
Manufacturers need to do more to ensure that whatever service or product they sell is as secure as possible in the implementation of services such as DNS in order to protect their customers.












