(13-03-23) Blog 72 – In cyberspace, no one can hear you scream
The (adapted) most iconic poster tagline for any film starts this blog*, and with good reason, a new variant of the Xenomorph banking trojan has been seen in the wild causing issues for Android users.

The cybercriminal gang Hadoken Secury Group has somewhat boringly named this new variant Xenomorth 3rd Generation and say that this revamped malware has the ability to perform financial fraud in a seamless manner.
What is Xenomorph?
Xenomorph is a malware which targets Android users by being bound to other legitimate applications in the Google Play store to avoid detection by Googles’ security scanners.
It is believed that the choice of name for this malware is that the underlying code is derived from another banking trojan called Alien, which itself a fork of the code of the most successful Android banking trojan ever – Cerberus – which was shutdown in 2020.
Users are tricked into downloading and installing what they perceive to be useful, legitimate applications, but in the background the malware is deployed.
Many thousands of Android users have unwittingly installed this trojan since its first appearance back shortly after the demise of Cerberus. In one case, 10,000 users downloaded a fitness app called GymDrop which was a front for the Alien malware.
What does Xenomprph do?
Once deployed, the malware harvests device information, and intercepts all SMS messages – this is so that it can receive any Out-Of-Bounds security PINs from financial transactions.
The malware then uses an overlay approach to change the appearance of websites the victim visits and apps they use to trick the user performing actions such as confirming activities, or entering extra data.
The malware also makes changes to the Android security subsystems in an attempt to stay hidden and also to achieve a level of persistence on the device.
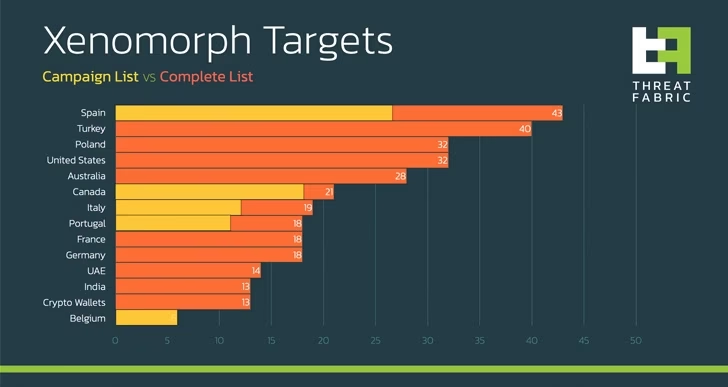
Xenomorph is known to target the users of over 50 different European banks with the majority of victims to be in either Spain and Turkey. The new Xenomorph v3 however has been seen with a much broader global set of targets
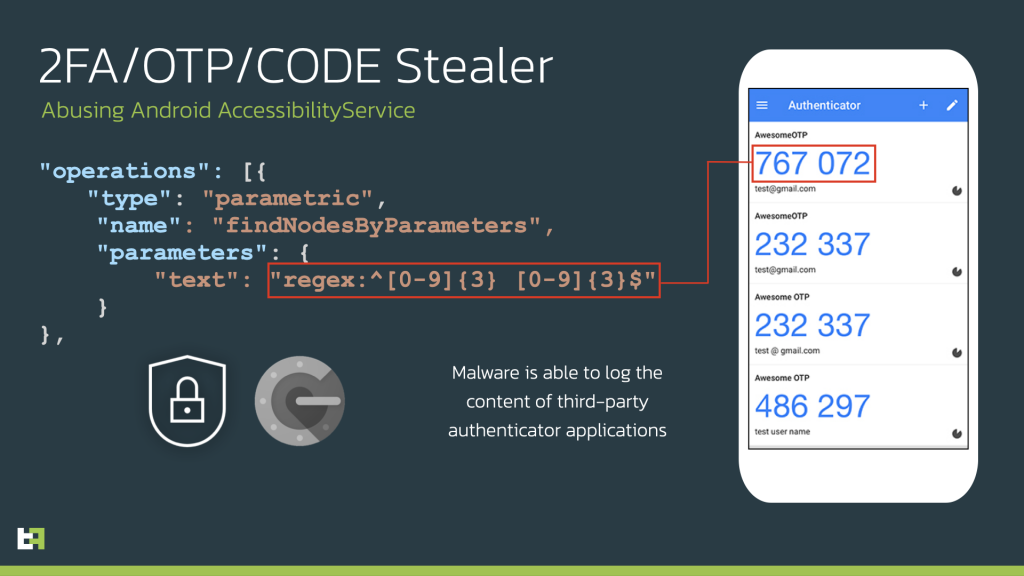
The Xenomorph malware update now also sees the malware capable of intercepting authenticator app data. Financial institutions are gradually moving away from SMS authentication due to the rise in SIM swapping / cloning attacks and are moving to the seemingly more secure authenticator app approach.
Xenomprph uses an ATS module (Automated Transfer Systems) to allow the malware to automatically extract user credentials, retrieve account balances, initiate transactions, obtain MFA tokens, and authorise fund transfers all without any human interaction.
This ATS module uses Regular Expressions (RegEx) to extract authenticator codes from the app and relay them back to the malware for use.
In a detailed report about Xenomorph, Cyber security company Threat Fabric say that:
“Xenomorph v3 is capable of performing the whole fraud chain, from infection, with the aid of Zombinder, to the automated transfer using ATS, passing by PII exfiltration using Keylogging and Overlay attacks. In addition, the Threat Actor behind this malware family has started actively publicizing their product, indicating a clear intention to expand the reach of this malware. ThreatFabric expects Xenomorph to increase in volume, with the likelihood of being one again distributed via droppers on the Google Play Store”
Threat Fabric
*fun fact – The line “In Space, no one can hear you scream” is never mentioned in the film – it was just on the movie posters!













