(12-03-23) Blog 71 – NetWire admin tool exposed as malware
The FBI announced on Thursday (9th March) that they had seized a domain which had been used to sell a Network Remote Administration Tool which was actually a malicious application that allowed threat actors to compromise computers across the globe.
The domain seized was worldwiredlabs.com, and the malware in question was a utility called NetWire.
Navigating to the domain now shows the FBI take-down notice.
Versions of the worldwiredlabs website can still be seen via the Internet Archive and show a very convincing website used to exist.


The NetWire application
It is believed that the NetWire software has been traded on various Dark Web sites since 2002 for prices ranging between USD $40 and $140.
The RAT is offered in various configurations capable of being used against a wide range of targets including Microsoft windows, Linux, and MacOS.
As a RAT, the software has the ability to take remote control of infected devices, record keyboard strokes and mouse behavior, take screenshots, check system information, and create fake HTTP proxies.
The developers of NetWire put in a lot of effort to ensure that once on a victim device the malware is difficult to detect, but also any analysis of the malware is a difficult thing to perform.
The application used PowerShell to bypass various Windows security utilities and gain it’s foothold on the victim machine
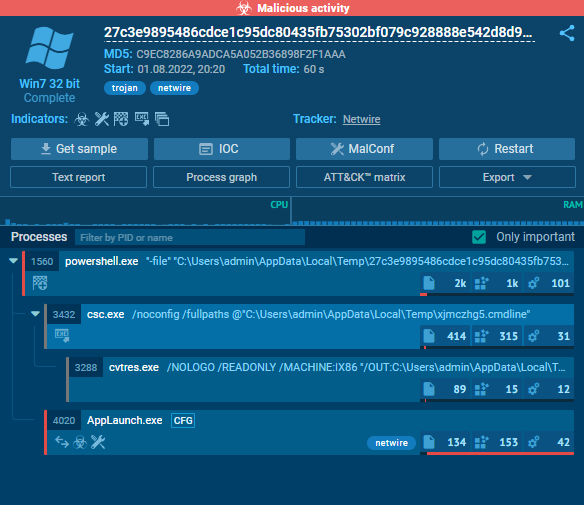
The software had many techniques to stay hidden, including multiple data encryption layers and string obfuscation.
Another technique used to to keep the malware hidden was to inject its code into the Notepad.exe executable. To most people, seeing Notepad.exe in their task manager utility would not raise many suspicions. However, it is not normal for Notepad to have an always active network connection, and this is one of the activities of the malware which ultimately gave it away to forensics examiners.
To maintain a level of persistence on an infected Windows device, the malware would create a Windows shortcut in the Startup menu to ensure that the trojan would always run when the user logged into the system.
Communication between an infected device and the attackers C2 servers used a custom binary protocol which was encrypted, along with any stolen data it sends.
Infection and installation
For most victims, the infection route for NetWire is the common phishing attack, however the malware has also been seen bundled into other tools and utilities found online.
One sample submitted to the file analysis website any.run shows the malware as a zipped attachment in an email purporting to be a tender submission document pack.
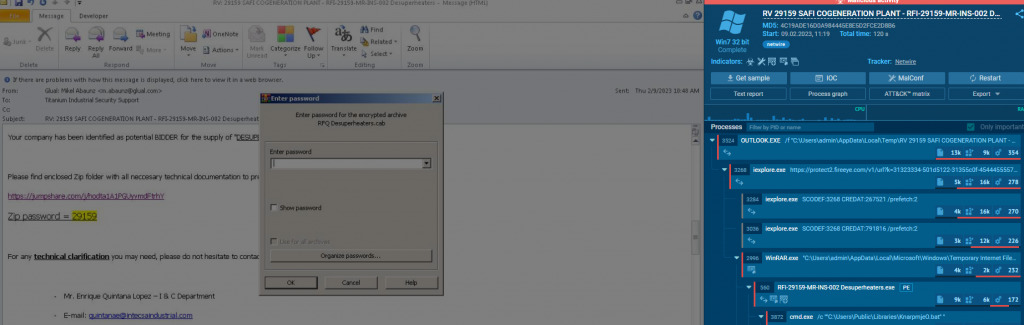
In another sample, a word document is used to drop an executable to the victim machine which then connects to a remote server to download the malware
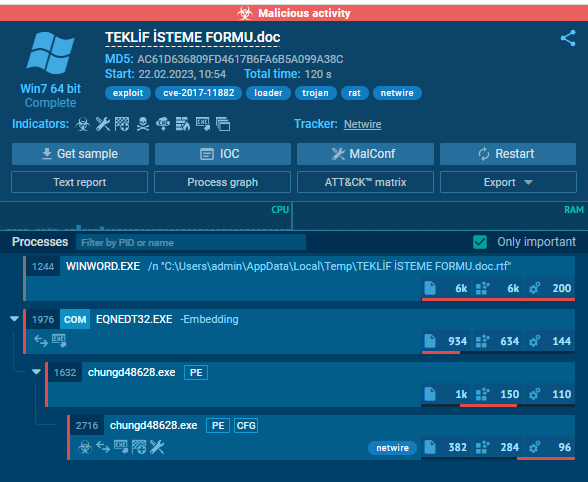
Another sample, uploaded 10th March 2023 shows that the malware is still being spread, in this case inside a utility used to copy chip information from payment cards.
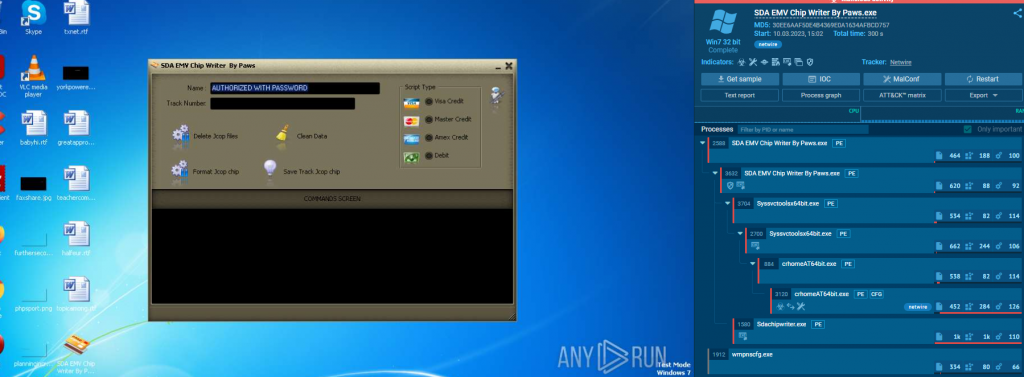
However, it was the existence of the worldwiredlabs website which has been the focus of the FBI in that this was a site masquerading as a legitimate company selling a utility to corporate entities.
One piece of advertising spiel on the worldwiredlabs site said:
“NetWire is specifically designed to help businesses complete a variety of tasks connected with maintaining computer infrastructure. It is a single ‘command center’ where you can keep a list of all your remote computers, monitor their statuses and inventory, and connect to any of them for maintenance purposes”
Long game to arrest
The arrest and close-down of the site has been a while in the planning. Over the years, a number of cyber security research sites had commented on the rise and proliferation of the malware.
In 2014, PaloAlto Networks released a comprehensive report into the Rise of Nigerian business email compromise, where they identified NetWire as one of a number of Remote Access Trojans (RATs) used by the criminal gangs operating out of the West African country.
In 2016, cyber security company SecureWorks reported on a case they had worked where they had observed unknown treat actors harvesting credit card data via a tool which they identified as being NetWire. The tool used a keylogger component to grab data as it was input by victims on compromised USB card readers.
In November 2019 researchers from another cyber security company – proofpoint uncovered email campaigns distributing NetWire in a targeted campaign against Bulgarian citizens.
The FBI began their investigation in earnest back in 2020 when they purchased a copy of the software and examined it in a sandboxed network.
The forensic analysts used NetWire’s Builder Tool on a test computer to construct a customized instance of the NetWire RAT, which was then installed on a Windows virtual machine.
During this process, the NetWire software never required the analyst to confirm that it owned, operated, or had any property right to the test victim machine that they “attacked” during its testing (as would be appropriate if the attacks were for a legitimate or authorized purpose).
In other words, based on this experiment, the FBI concluded that the owners of NetWire never bothered to check that its customers were using it for legitimate purposes on computers they owned or controlled.
Using the virtual machine they set up, the analysts then tested all of NetWire’s functionalities, including remotely accessing files, viewing and force-closing apps, exfiltrating stored passwords, recording keystrokes, executing commands via the command prompt or shell and taking screenshots.
The analysts emphasised that in all the features tested above, the infected computer never displayed a notice or alert that these actions were taking place. This is contrary to legitimate remote access tools where consent from the user is typically required to perform specific action on the user’s behalf.
The evidence supplied by the FBI analyst allowed the FBI to request the warrentry to seize the servers and arrest those involved.
Law enforcement agencies in Croatia arrested a Croatian national who is suspected of being the websites administrator, whilst law enforcement agencies in Zurich seized the physical servers used to host the website itself.
Following the announcement by the FBI, cyber security journalist Brian Krebs published an article where he used publicly accessible DNS records, WHOIS website registration data, information provided by a service that indexes data exposed in public database leaks and even a Google+ profile, to link the worldwiredlabs.com website to a person named Mario Zanko.












