(10-03-23) Blog 69 – Stealerium – an overview
Stealerium is an open-source stealer malware available on GitHub, and as the name suggests, the malware steals information from various applications as well as the host device.

The applications targeted by Stealerium include:
- Browsers
- Cryptocurrency wallets
- Discord
- Pidgin
- MS Outlook
- Telegram
- Skype
- Element
- Signal
- Tox
- Steam
- Minecraft
- VPN clients
The malware employs multiple anti-analysis techniques in its attempts to stay persistent on an infected device. These techniques include detecting if it is running inside a virtual machine or sandbox, and the presence of analysis tools such as Wireshark, process hacker and TCPView.
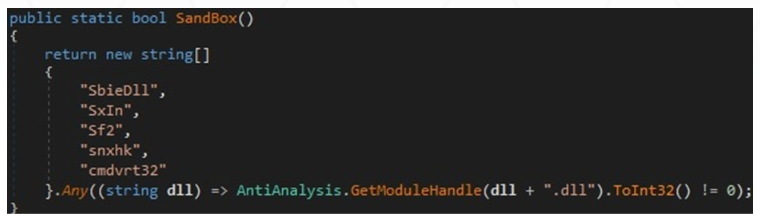
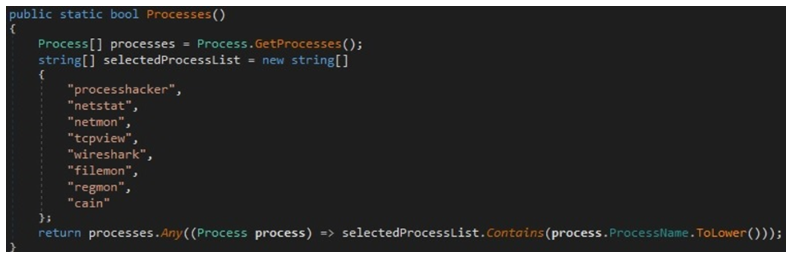
The binary can also check to see if its process is being debugged via the Microsoft Kernel32 CheckRemoteDebuggerPresent API.
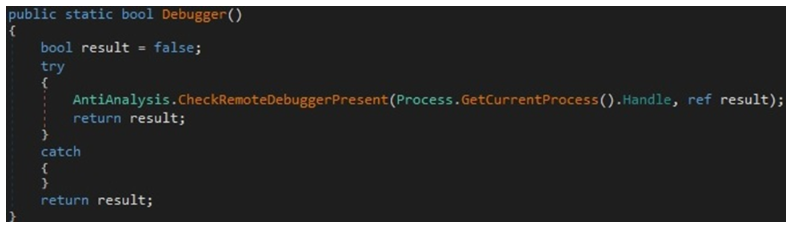
Stelerium code to check for debugging – securityscorecard.com
If any of the above applications or processes are detected by the malware, it will display a fake error message and terminate its process
Attacking browsers
Stealerium targets chromium -based browsers (Google Chrome, MS Edge, Brave, etc.) and extracts data from the LocalAppData dirxctory.
The focus of attention for the malware is to extract sensitive items such as credit card data, passwords, cookies, browser history, and bookmarks.
To extract credit card data stored in the browser, the malware decrypts the information in the credit_cards table of the Web Data database.
It is able to decrypt the data because it obtains the master key from the host by using the DpapiDecrypt function which is a powerful Windows decrypter utility available from Nirsoft.
Saved username/password data is also extracted from the victim device from the logins table of the Login data database via the same method as described above.
Similarly, browser history, bookmarks, autofill data, and cookies are also able to be obtained.
Chromium based browsers are not the only target for Stealerium. Those browsers which are based on Gecko can also be targeted. E.G. Firefox, K-Meleon, Waterfox, Flock, IceCat, etc.
Stealerium has similar capabilities for attacking these browser and can extract bookmarks, cookies, and browsing history.
Hostname, EncryptedUsername, and EncryptedPassword data is extracted from the browser via the logins.json file and is decrypted by calling the Pk11SdrDecrypt function.
Keylogging, scraping, and more
Stealerium actively hunts for running applications and harvests as much data as it possibly can.
The malware obtains “state” information of the infected machine by obtaining information about the current network configuration, including Wi-Fi names and passwords, public & private IP addresses, Windows product key data, CPU and GPU data, the amount of installed RAM, Screen size(s) and battery information.
The contents of the clipboard are extracted and a list of all installed applications is retrieved.
All stolen information is compressed to an archive file and is uploaded to GoFile.io which returns a URL which is then sent to the attacker via discord for them to retrieve.
The Stealer function runs a keystroke capture utility which looks for physical key presses as well as those used via the virtual keyboard.
When the stealer scrapes the browser, it actively looks for browser window titles which contain words such as facebook, twitter, telegram, chat, etc. and if any of these words are present, it starts recording keystrokes as well as takes a screenshot of the active window.
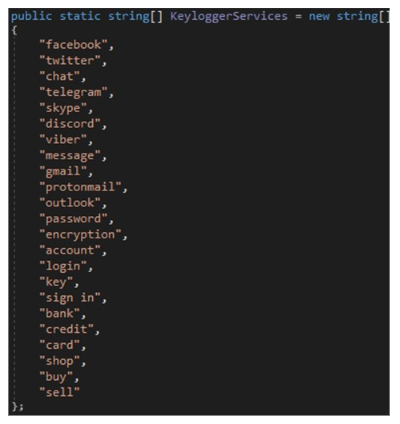
If the active window contains adult content, then the malware takes a screenshot, but also grabs an image from the victims webcam (if available).
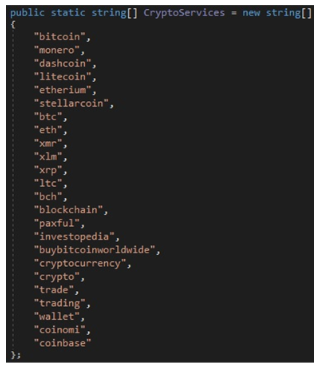
If the malware detects that the active window contains data relating to cryptocurrencies, a clipper module replaces any cryptocurrency wallet addresses with the attackers addresses whenever the victim makes a transaction.
This is one malware you really do not want on your device.
- Always keep your device up-to-date with the latest security patches
- Use an anti-malware solution, and perform regular scans of your system(s)
- Use a firewall
- Be cautious about clicking links in unsolicited emails












