(08-03-23) Blog 67 – The Dark web – what is it exactly? Pt3
For my 3rd installment of this mini-series of blogs about the dark web, I will take a look at the system called I2P.
What is I2P?
I2P, or the Invisible Internet Project is a fully encrypted private network layer which sits atop of the usual Internet layer which we use.
The construct of the system is such that it hides the servers you visit from the you, and you from the servers you visit.

In a similar way to some other Dark web technologies such as Tor you can communicate with traditional web services when using I2P, however this is not recommended as it may expose sensitive data. When using I2P services, all I2P traffic is internal to the I2P network and does not interact with the Internet directly.
I2P uses encrypted unidirectional tunnels between you and those which you connect to. In principle, it’s a bit like you creating a one-way VPN to a server to send it data, and the server creates a one-way VPN back to you through which it sends you the data.
No one can see where traffic is coming from, where it is going, or what the contents are.
I2P was designed initially for the transmission of messages, but web hosting is also possible. Websites within I2P are known as ‘eepsites’.
Like with Tor, eepsites are only accessible via the I2P network and do not have publicly addressable DNS domain names.
So how does it work?
The I2P application is available for download from geti2p.net, and after download, when you install the I2P software it builds a service similar in operation to that of a router. This is the core service of the I2P system and is how you communicate within the network.
As well as the router application, the software builds a webservice, and hosts the I2P router console through which you configure your I2P network connections, and access the content hosted within the network.
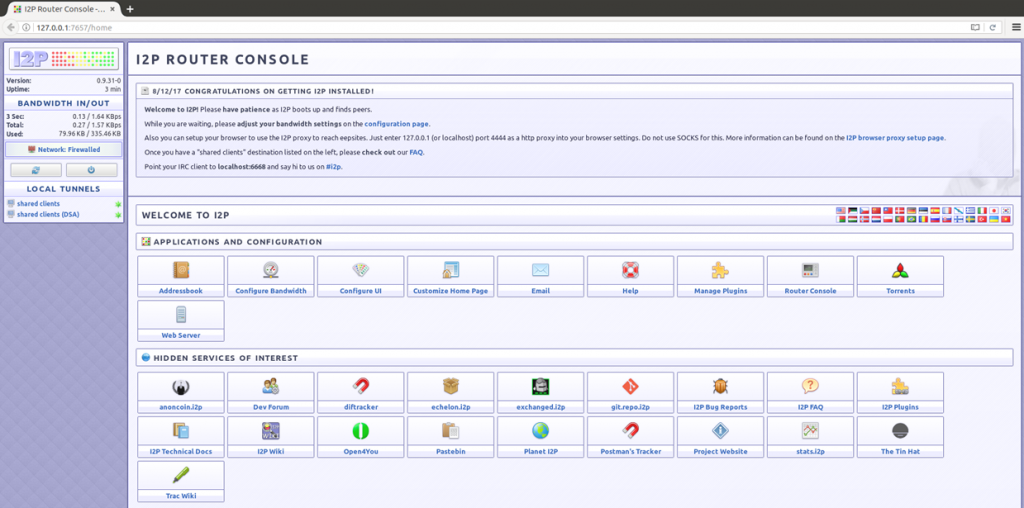
In a similar approach to Freenet, this webservice is hosted on your loopback IP address and listens on port 7657. As such, this can be accessed by opening your browser and typing either http://localhost:7657, or http://127.0.0.1:7657.
In addition to these services, I2P comes bundled with a number of applications designed to run through the I2P network:
- SusiMail – A secure email client
- I2PSnark – An I2P BitTorrent client
- The Address Book – A service which allows you to locate and store I2P eepsite addresses
- QR code generator – A quick way to share eepsite addresses
- I2P Hidden services manager – An adapter that allows for services such as SSH, FTP, etc to communicate in and out of the I2P network and the surface Internet
Using I2P
When using I2P for the first time, or if you have not used the systems for a few days, your router will need to build its list of inbound and outbound tunnels. This process can take a very long time to build a set of reliable routes – sometimes upto 24hours before the system is in anyway useable.
I2P tunnels are encrypted using NTCPv2 – a propriety implementation of the NOISE protocol using AES-256-CBC.
When a client wants to send a message to another client, the transmitting client identifies the endpoint, and transmits the message via one of their outbound tunnels targeting their neighbouring client’s inbound tunnel. This process is repeated until the message reaches its destination.
Every participant in the network chooses the length (number of hops) of the tunnels to a destination, and in doing so, makes a trade-off between anonymity, latency, and throughput according to their own needs. The longer the tunnels, the more secure, but the slower they will be.












