(07-03-23) Blog 66 – The Dark web – what is it exactly? Pt2
In this 2nd installment of this mini-series of blogs about the dark web, I will take a look at the system called Freenet.
What is freenet?

According to the website freenetproject.org, Freenet is a peer-to-peer platform for censorship-resistant and privacy-respecting publishing and communication, and is is built on the principle of small world networks. By connecting to systems of people you know, and those people you know in turn connect to people they know, one should be able to reach all nodes in a Freenet network.
Think of freenet a bit like the Six Degrees of Kevin Bacon game.
For those who have never heard of this game, The Six Degrees of Kevin Bacon or “Bacon’s Law” is a game based on the “six degrees of separation” concept, which posits that any two people on Earth are six or fewer acquaintance links apart. Movie buffs challenge each other to find the shortest path between an actor or director, and prolific actor Kevin Bacon.
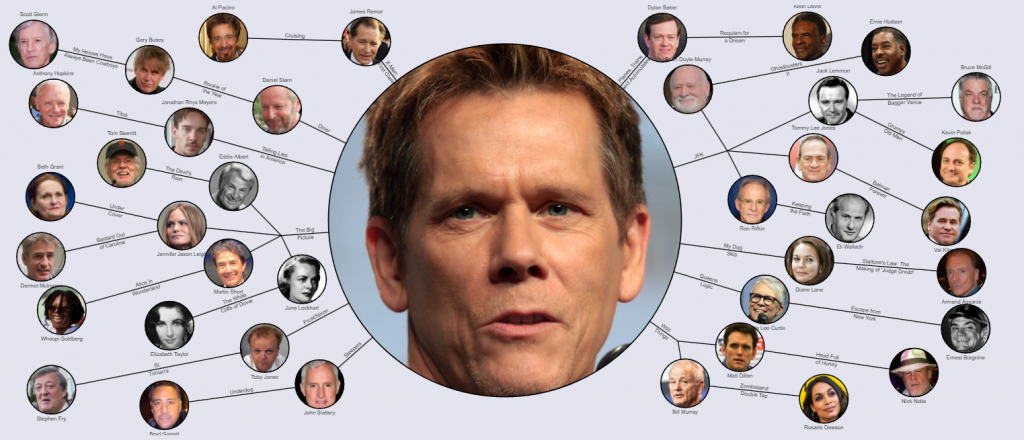
Freenet is a peer-to-peer network, in that there exists no traditional client/server architecture. Every node is both a client and a server at the same time. This means that the Freenet network is both decentralized and anonymised.
The nodes which you connect to only know their nearest neighbours and have no idea about how the network as a whole is structured.
So how does it work?
After downloading and installing the application software, you will be asked a couple of questions regarding how you wish to set up your Freenet environment, including how much hard drive space you want to donate to the network.

The Freenet datastore
All devices (nodes) in the freenet network contribute an amount of hard drive space to store encrypted pieces of files. These pieces are stored in the datastore directory which is located in the Freenet installation directory.
When files are added to the datastore, they are encrypted and distributed throughout the Freenet network
When using Freenet, you have very little control over what data is stored in your datastore. Instead, files are kept or deleted depending on how popular they are. This allows Freenet to be censorship-resistant. There is no “delete file” operation.
It is very difficult, but not impossible, to determine what the encrypted file pieces stored in your local Freenet datastore are part of. This allows for plausible deniability over the content.
File identifiers
Each file that exists on Freenet has a key associated with it. There are various kinds of keys which are used for everything on Freenet, and are a kind of URL ( e.g. freenet:=KSK@sample.txt).
Most keys are hashes, and to access a particular piece of data on Freenet, you need to know the key to the data, and enter it like the example shown below (or click a link which contains the key):
http://localhost:8888/[Freenet Key]
Content Hash Keys (CHKs) are used for files with static content, like an .mp3 or a PDF-document. These keys are hashes of the content of the file.
A hash is a reproducible method of representing a specific piece of data into a value (hash digest) which serves as a unique fingerprint for the data.
If the file content changes, even by a tiny amount, then the hash of the file changes greatly. This makes the data hard to tamper with without anyone noticing.
A typical CHK key has the following structure:
CHK@file hash,decryption key,crypto settings
For example:
CHK@SVbD9~HM5nzf3AX4yFCBc-A4dhNUF5DPJZLL5NX5Brs,bA7qLNJR7IXRKn6uS5PAySjIM6azPFvK~18kSi6bbNQ,AAEA--8
Because the decryption key is part of the key for the file, and is not included in requests for the file’s pieces, it is not possible to decrypt a file without the CHK key.
Using Freenet
Once Freenet is configured, a web server will be created and started on your system. To connect to this server, click the applications list in your system tray and the right-click the Freenet application. Here you will see the option to open Freenet which will launch your browser and connect you to your localhost IP address on port 8888.
Alternatively, open your browser, and in the URL bar type http://127.0.0.1:8888
When the browser launches, you will see a webpage with all the options to use Freenet, including links to other people’s “freesites”.
Use the webpage, just like you would any other webpage – click a hyperlink to open the page. When you follow a link, the pieces which make the site are gathererd from the other freenet users datastores and downloaded to your device where they are re-assembled and displayed in your browser – essentially you are viewing your own webpage at this point.
Two types of Freenet
When you use Freenet you have the option of connecting to “strangers” – (i.e. all the other freenet users), or “friends” – (i.e. people you actually know and trust)
The default connection type is to connect to strangers – this is called the insecure mode as you have no idea which systems you are sharing data with.
To connect to your friends’ nodes, you have to exchange Node references with them. The references must be added on both sides of the conversation to be established. That is, you need to add their data and they need to add yours.
This mode of operation creates completely private and undetectable Freenets.












