(01-03-23) Blog 60 – Exfiltrator-22, coming to a network near you…
A new post-exploitation framework called Exfiltrator-22 has begun to appear online – offered by its developers on dark-net websites for a subscription fee.
First seen in November 2022, the developers have begun a broad advertising campaign to entice would-be customers. The main platform to see and buy Exfiltrator-22 is Telegram, but the developers have also posted a couple of demo videos on YouTube.
The developers have announced that they will continue to update the framework with tools specifically designed to help stay hidden on a target network.
What do you get for your money?
Prices for the utility come at either USD $1000/mth, or USD $6000 for a lifetime subscription.
For your money, you get the ability to access control dashboard hosted on a bullet-proof VPS (Virtual Private Server) with the capability to execute various capabilities on a compromised machine, including:
- Establish a reverse shell with elevated privileges.
- Upload or download files between the victim and the C2 server
- Activate a keylogger
- Activate a ransomware module
- Capture a screenshots
- Start a VNC (Virtual Network Computing) session for real-time access
- Elevate access privileges on the infected device
- Establish persistence
- Activate a worm module that spreads the malware to other devices on the same network or the internet
- Extract passwords and tokens from the LSAAS (Local Security Authority Subsystem Service).
- Generate cryptographic hashes of files on the victim device to help monitor file locations and content change events
- Examine and manipulate running processes
- Extract authentication tokens from the breached system
Who are the developers?
Security research company Cyfirma have analysed exfiltrator-22 and have suggested that the developers behind the code are none other than the LockBit ransomware gang.
In a post on their website, they state that the threat actors are “operating from North, East, or South-East Asia (possible countries include China, Taiwan, Hong Kong, Malaysia, Singapore, Philippines, etc.).”
These individuals possess a thorough knowledge of defense evasion and anti-analysis techniques. They have utilized leaked source code from post-exploitation frameworks to develop their own post-exploitation-framework-as-a-service model. Likely, ex-affiliates of LockBit, the threat actors are willing to build their own affiliate program and are coming out with an aggressive marketing strategy – claiming to be FUD (fully undetectable) by every Antivirus and EDR vendor.
Cyfirma research
Attribution
A screenshot posted by the threat actors on their telegram channel, showed that a sample of their malware was uploaded to Virus Total for dynamic analysis on 2nd December 2022 at 5:54 PM UTC, which is 3rd December 2022 1:55 AM in the threat actors’ host time- zone. Putting the threat actors 8 hours ahead of the browser timestamp – hence the Asia attribution.
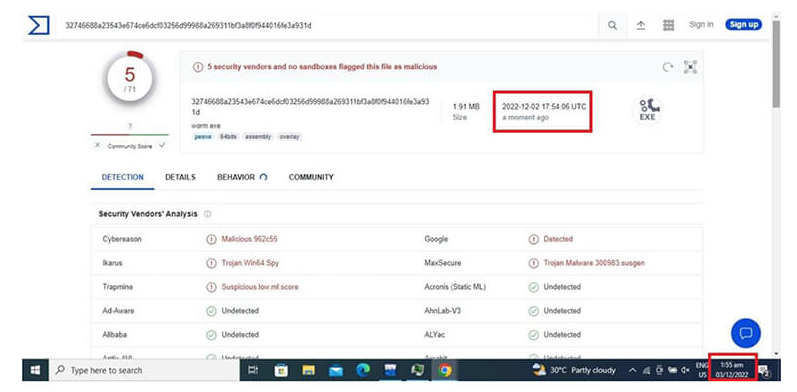
On further analysis of the sample’s activities in the dynamic analysis sandbox, it was noted that the sample was a compiled executable which was created on 2022-12-02 at 14:08:08 UTC, and is designed to target devices with x64 architecture.
The C2 infrastructure used by the malware points to an IP Address belonging to the Akamai Content Delivery Network (CDN).
Whilst this is not unusual for hackers to hide their traffic & locations behind CDNs – a technique called Domain Fronting – analysis of other malware samples revealed that a sample for LockBit 3.0 shares the same domain fronting technique, and that LockBit 3.0 uses the same IP Addresses for it’s C2 infrastructure.
Whoever is behind this new threat – they seem to be well skilled and organised, and companies the world over should be expecting this to hit them at some point.












