(27-02-23) Blog 58 – Lazarus group – an Exposé
You may or may not have heard of the North Korean hacking group known as Lazarus Group. If you haven’t – you will most certainly have heard of some of their activities: Sony Hack? WannaCry? Bank of Bangladesh hack?
The Lazarus group is a name given to a collective of hacking teams associated with the North Korean Government, and is made up of a vast array of smaller teams.
Timeline of activity
Denial of Service attacks
The gang, now known as Lazarus group, have been active since 2009 when they waged a DDoS attack on various South Korean Government services for a period of three years.
It is possible that they were responsible for an earlier attack against South Korea in 2007, but that has not officially been attributed, so it cannot be said for certain that Lazarus group were responsible
Sony Pictures hack
In 2014, the group was responsible for the now infamous attack on Sony Pictures in retaliation for the entertainment company’s release of the film “The Interview” which is a comedy about a plot to assassinate North Korean leader Kim Jong-un.

The exact timeline of the attack against Sony is not fully understood. Digital forensic investigators say the hackers spent at least two months copying critical files from the Sony network, although a purported member of the gang who claimed to have performed the hack stated that they had access for at least a year.
The hackers claimed to have taken more than 100 terabytes of data from Sony, but that claim has never been officially confirmed.
Components of the attack included a listening implant, a backdoor, a proxy tool, a destructive hard drive tool, and a destructive target cleaning tool. The se components clearly suggest an intent to gain repeated entry, extract information, and be destructive, as well as remove evidence of the attack.
Sony employees were made aware of the hack on November 24th 2014, as the previously installed malware rendered many employees’ computers inoperable.
Staff who’s PCs were not on, were met with a message when they tried booting the PC’s that the machine had suffered an error and was trying to recover – these machines had been wiped and would never recover.
Those employees who’s PCs were already on, but locked, were shown a warning by a group calling themselves the Guardians of Peace – The warning was displayed via the desktop background – something which could only be displayed by an update to the Group Policy Object – something which could only be altered by having access to the Sony Active Directory server – The hackers had full control of the Sony network.
The warning contained a message that the Sony systems had been compromised and that data had been taken. The message also displayed links to portions of the confidential data taken during the hack to prove legitimacy.

The stolen data included personal information about Sony Pictures employees and their families, emails between employees, information about executive salaries at the company, copies of then-unreleased Sony films, plans for future Sony films, scripts for certain films, and other information.
The message stated that Sony had already been warned – this was in reference to the fact that the previous Friday (November 21st ) an email had been sent to numerous Sony executives from a group called “God’sApstls” which demanded “monetary compensation” or otherwise, “Sony Pictures will be bombarded as a whole”.
Sony said that the emails had either been ignored by their staff, or that they had never received them as the system had marked them as spam and deleted them.
In the days following the attack, the Guardians of Peace began leaking films and portions of the confidential data to attract the attention of social media sites, although they did not specify what they wanted in return.
Sony Pictures contacted the FBI and the private security firm FireEye to help protect those whose personal data was exposed by the hack, repair the damaged computer infrastructure and trace the source of the leak.
On December 8th, the hackers released their eighth data dump of confidential information, but also threatened Sony with language relating to the September 11 attacks which drew the attention of U.S. security agencies. The language referenced bombing movie theaters which were due to show the up-coming film The Interview.
North Korean officials had previously expressed concerns about the film to the United Nations, stating that “to allow the production and distribution of such a film on the assassination of an incumbent head of a sovereign state should be regarded as the most undisguised sponsoring of terrorism as well as an act of war.”
This was one of the first pieces of the puzzle that pointed a finger to North Korea’s involvement in the hack.
Attacks against banks
In 2015, the Lazarus group were behind attacks against the Ecuadorian bank – Banco del Austro, in which they managed to steal USD $12M.
The same year, they stole a further USD $1M from the Vietnamese bank – Tien Phong Bank.
It was in 2016 however that they achieved their biggest financial haul. In the February of that year, thirty-five fraudulent instructions were issued via the SWIFT banking network to transfer close to US$1 billion from the Federal Reserve Bank of New York account belonging to Bangladesh Bank, the central bank of Bangladesh.
Five of the thirty-five fraudulent instructions were successful in transferring USD $101M
The Federal Reserve Bank of New York blocked the remaining thirty transactions, amounting to US$850 million, due to suspicions raised by a misspelled instruction
USD $20M of the stolen money has been traced to Sri Lanka and USD $81M to the Philippines.
All the money transferred to Sri Lanka has since been recovered. However, as of 2018 only around US$18 million of the US$81 million transferred to the Philippines has been recovered.
The USD$20M transfer to Sri Lanka was intended by the hackers to be sent to the Shalika Foundation, a Sri Lanka-based private limited company, however the hackers misspelled “Foundation” in their request to transfer the funds, spelling the word as “Fundation”. This spelling error gained suspicion from Deutsche Bank, a routing bank which put a halt to the transaction in question after seeking clarifications from Bangladesh Bank.
Sri Lanka-based Pan Asia Bank initially took notice of the transaction, with one official noting the transaction as too big for a country like Sri Lanka. Pan Asia Bank was the one which referred the anomalous transaction to Deutsche Bank.
The money transferred to the Philippines was deposited into five separate accounts with the Rizal Commercial Banking Corporation (RCBC); the accounts were later found to be under fictitious identities.
The deposited funds were transferred to a foreign exchange broker to be converted to Philippine pesos, returned to the RCBC and consolidated in an account of a Chinese-Filipino businessman.
The conversion was made between 5th to 13th February 2016.
On February 8th during the Chinese New Year, Bangladesh Bank informed RCBC through SWIFT to stop the payment, refund the funds, and to “freeze and put the funds on hold” if the funds had already been transferred.
Chinese New Year is a non-working holiday in the Philippines and a SWIFT message from Bangladesh Bank containing similar information was received by RCBC only a day later. By this time however, a withdrawal amounting to about USD $58.15M had already been processed by RCBC’s Jupiter Street (in Makati City) branch.
Timeline of the Bank of Bangladesh attack
The Philippines’ National Bureau of Investigation (NBI) launched a probe and looked into a Chinese-Filipino who allegedly played a key role in the money laundering of the illicit funds.
On 10 January 2019, Maia Santos Deguito, a former manager at RCBC was convicted and sentenced to 4 to 7 years imprisonment at a Philippine court for money laundering.
Federal prosecutors in the United States have revealed in a report, possible links between the government of North Korea and the theft.
The report said that “alleged Chinese middlemen” facilitated the transfer of the funds after it had been diverted to the Philippines.
The Cybersecurity and Infrastructure Security Agency (CISA) published an alert “FASTCash 2.0: North Korea’s BeagleBoyz Robbing Banks”, which attributed the Bank of Bangladesh hack in 2016 to BeagleBoyz.
The agency claimed that BeagleBoyz is a threat actor group under the North Korean government’s Reconnaissance General Bureau, and have been active since 2014.
The U.S. has charged a North Korean computer programmer with hacking the Bangladesh Bank, alleging this was carried out on behalf of the regime in Pyongyang.
The same programmer has also been charged in connection with the WannaCry 2.0 virus and the 2014 Sony Pictures attack.
WannaCry
In May 2017, the world woke to a computer nightmare many had never seen before. Tens of thousands of computers across the globe were under attack.

The attack began at 07:44 UTC on 12th May and was halted a few hours later at 15:03 UTC by the registration of a kill switch domain which was discovered by British computer security researcher Marcus Hutchins.
The kill switch prevented already infected computers from being encrypted or further spreading WannaCry.
In those few short hours, it is known that over 300,000 devices in more than 150 countries were affected by WannaCry, such is the interconnected nature of the Internet.
What is WannaCry?
WannaCry is a malware categorised as a ransomware cryptoworm in that it encrypts files on victim machines, displays a ransom note, and then propogates through the network looking for other devices to infect.
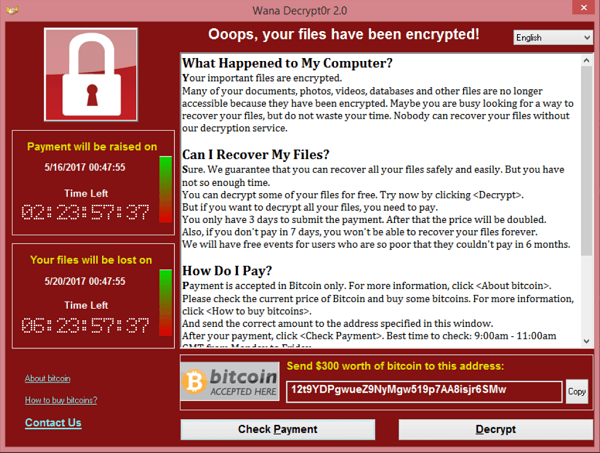
The malware targets devices running vulnerable versions of Microsoft Windows and propagates throughout networks by using an exploit known as EternalBlue, which was originally developed by the United States National Security Agency (NSA).
EternalBlue leverages a vulnerability in Microsoft’s implementation
of Server Message Block (SMB) – CVE-2017-0144
EternalBlue was stolen and leaked by a group called The Shadow Brokers a month prior to the attack.
After the NSA breach, Microsoft patched the vulnerability and issued a security update but many companies did not implement the updates due to ignorance of their importance, or an inability to update.
After the attacks, security researchers across the world collaborated online to develop open source tools that allow for decryption without payment under some circumstances,
It is known that the hackers behind WannaCry only accrued a small amount of money form the ransoms. Analysis of the three bitcoin addresses in the ransom message shows that 430 payments have been made and 54.43228033 BTC has been sent to those accounts.
The price of bitcoin fluctuates wildly, but on May 11th 2017 the high-price for bitcoin was USD $1,873.93 which would equate to a total of approx. USD $101,940 for the 54.4 BTC paid.
The recovery costs to the affected organisations however is much higher. Estimates put the global recovery costs at over USD $4B. The NHS estimate that it cost £92M to fix the issues caused by WannaCry.
In 2020, the UK government formally attributed the WannaCry attack to an organisation linked to Lazarus Group, and as such – the North Korean regime.
The attacks don’t stop
In February 2023, a new malware downloader named Wslink was discovered and has been linked to Lasarus group.
The deployed payload, called WinorDLL64 is a fully-featured implant that can conduct multiple activities including:
- Data exfiltratration
- Data overwrites
- Data deletion
- PowerShell command execution
- Device information collection
- List active communication sessions
- Create & terminate arbitrary processes
- Enumerate connected storage
- Perform data compression
Cyber Security researchers at ESET said in a recent report that “The Wslink payload can be leveraged later for lateral movement, due to its specific interest in network sessions”
ESET researcher Vladislav Hrčka said. “The Wslink loader listens on a port specified in the configuration and can serve additional connecting clients, and even load various payloads.”
The links to Lazarus Group stem from overlaps in behavior and code to that of previous campaigns – Operation GhostSecret and Bankshot – which have been attributed to the group.
ESET said the payload they examined was uploaded to the VirusTotal malware database from South Korea, where some of the victims are located, adding credence to the Lazarus involvement.
It seems like there is no stopping the North Korean hackers.












