(18-02-23) Blog 49a – Mirai – the botnet that just wont die
First seen in 2016, the mirai botnet has become one of the most notorious botnets the Internet has ever seen.
And now it’s back with 13 new vulnerabilities to target!
A bit of history
Named after the Anime series Mirai Nikki, the Mirai malware targets vulnerable IoT devices and attempts to gain access by initially trying a set of 60+ default username / password combinations.
Upon successful access, the malware will identify any “competing” malware, remove it from memory, and block any remote administration ports so that other hackers can no longer gain access.
Infected devices will continue to function normally, except for an occasional slowdown if the device is currently being used in a DDoS attack.

Since its arrival on the Internet, Mirai infected devices have been used to launch some of the most intensive DDoS (Distributed Denial of Service) attacks ever seen.
The first attack attributed to the Mirai botnet was on the 18th September 2016 against French technology company OVH, which saw their network crippled under approx. 1Tbps of data.
On the 21st September, the Mirai botnet was used to flood the website of security researcher Brian Krebs – Traffic levels directed at his website peaked at 620Gbps
On the 21st October, DynDNS – a large domain registrar and network optimisation company was targeted three times by the mirai botnet with traffic levels peaking at just over 1Tbps.
The attack against DynDNS meant that for many millions of Internet users, access to websites such as Reddit, Amazon, AirBnB, Github, Netflix, PayPal, and Twitter was severely affected – because the DNS requests for these sites could not be resolved, people couldn’t access the sites. Most people don’t know how to change their DNS server settings, so they were effectively cut-off from the WWW whilst DynDNS was under attack.
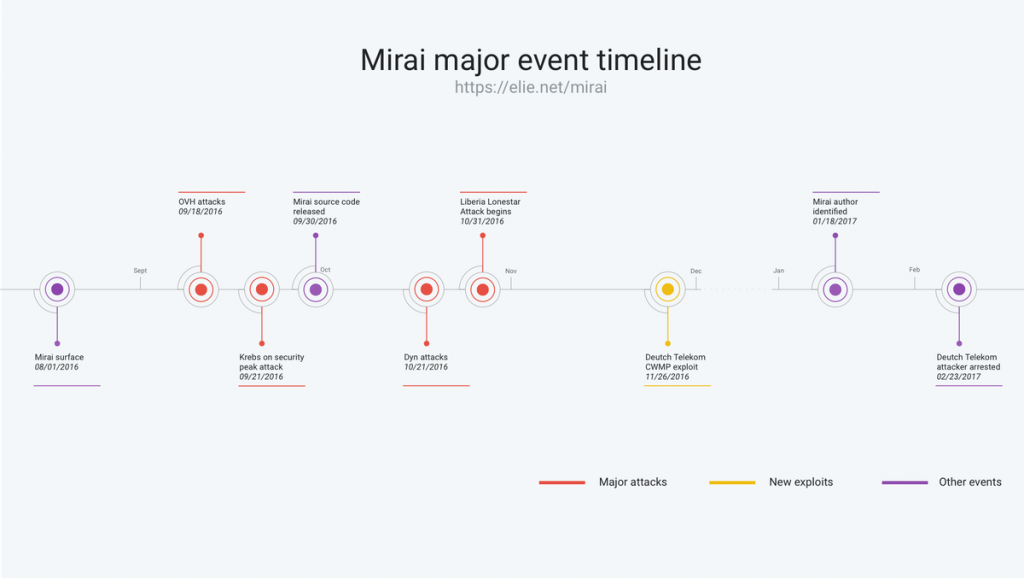
November 26th 2016 saw the German Internet provider Deutsche Telekom suffer a massive outage after 900,000 of its routers were compromised. This however was not a DDoS attack on the company, but rather the product of a “buggy” version of the Mirai code that caused the router to crash as the malware tried to infect them.
Open season for Mirai developers
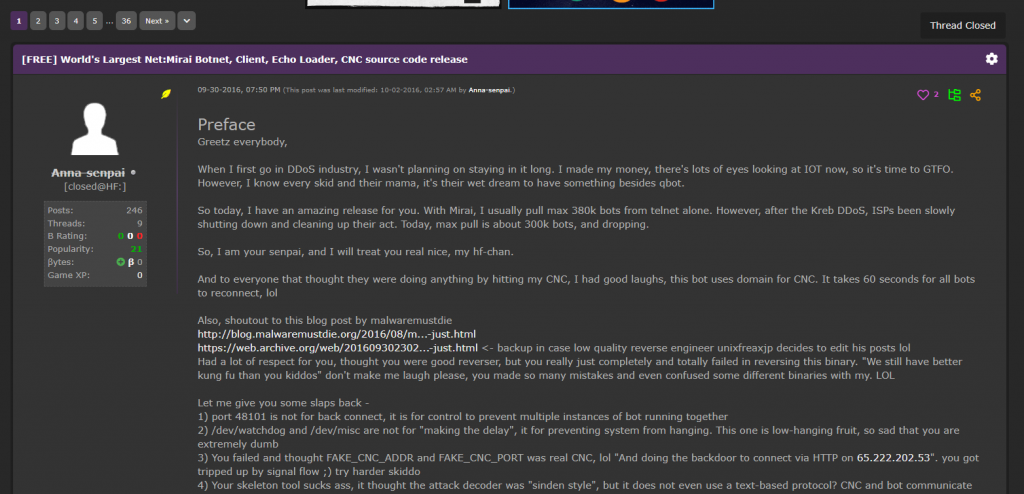
The reason for the “buggy” code is due to the fact that roughly 20 days earlier, the creators of Mirai, offered the source code for the malware for free via Hack Forums. Someone attempted to create their own variant of Mirai, but made mistakes.
In November of 2016, Daniel Kaye (aka BestBuy) was identified as the author of the variant that brought down Deutsche Telekom and was arrested at Luton Airport.
In July 2017, Kaye was extradited to Germany where he was sentenced to 1.5 years in prison.
In August 2017 he was returned to the UK to face extortion charges after he attempted to blackmail Lloyds and Barclays banks. He reportedly had asked for approx £75K in bitcoins from Lloyds for his (non-Mirai) botnet to be called off.
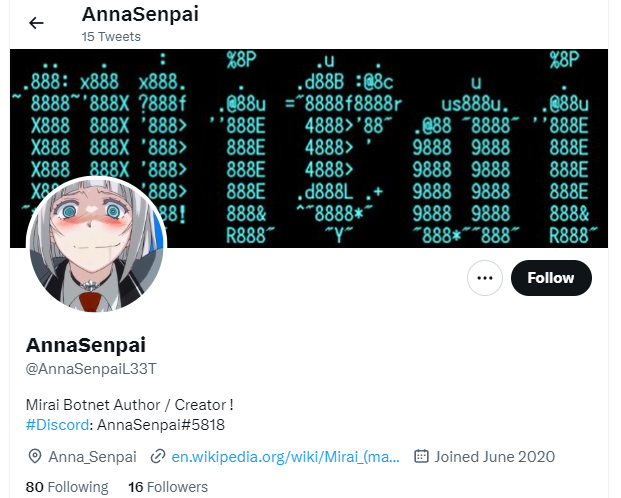
Anna-Senpai
As can be seen from the image above – the creator of the Mirai malware used the pseudonym Anna-senpai. This is a combination of two words:
Anna – From Anna Nishikinomiya – a character from Shimoneta: A Boring World Where the Concept of Dirty Jokes Doesn’t Exist
Senpai – an honorific used in Japan towards someone of a higher class than you, almost like a role model
We know that the person behind Anna-Senpai uses the avatar Anna Nishikinomiya because they use the image on a number of their social media accounts – see twitter image.
After the attack on his website, Brian Krebs embarked on an intensive hunt to identify Anna-Senpai. His investigation and discoveries are brilliantly documented on his website.
What’s Mirai been up to recently?
December 2017 – Mirai variant exploits zero-day vulnerability in Huawei HG532 routers
January 2018 – Mirai variant (Okiru) targets ARM, MIPS, x86, ARC processors in devices such as PCs, radios, cameras, smart meters, TVs, smart hubs, routers, and mobile devices.
January 2018 – Another Mirai variant used to hijack cryptocurrency mining operations and steal crypto currency.
January 2018 – two similar Mirai variants were reported (Masuta & PureMasuta), to attack EDB 38722 D-Link routers
March 2018 – a new variant of Mirai (dubbed as “OMG”) emerged with added configurations to target vulnerable IoT devices and turn them into proxy servers
May to June 2018, another variant of Mirai, (Wicked) emerged with added configurations to target at least three exploits including those affecting Netgear routers and CCTV-DVRs
July 2018 – at least thirteen versions of Mirai malware have been detected actively infecting Linux IoT in the internet
December 2018, a Mirai variant (Miori) started being spread through a remote code execution vulnerability in the ThinkPHP framework. This vulnerability is continuously being abused by the further evolved Mirai variants dubbed as “Hakai” and “Yowai” in January 2019, and variant “SpeakUp” in February, 2019
The here and now
So this brings me to the point of this blog – Mirai will not die…
Another new variant of Mirai has been found leveraging several security vulnerabilities to propagate itself to Linux and IoT devices.
Observed during the second half of 2022, the new version has been dubbed V3G4 by Palo Alto Networks Unit 42, which identified three different campaigns likely conducted by the same threat actor.
The attacks primarily single out exposed servers and networking devices running Linux, with the adversary weaponizing as many as 13 flaws that could lead to remote code execution (RCE).
Some of the notable flaws relate to critical flaws in Atlassian Confluence Server and Data Center, DrayTek Vigor routers, Airspan AirSpot, and Geutebruck IP cameras. The oldest flaw in the list is CVE-2012-4869, an RCE bug in FreePBX.












