(17-02-23) Blog 48 – OT:ICEFALL – a bad day for OT manufacturers
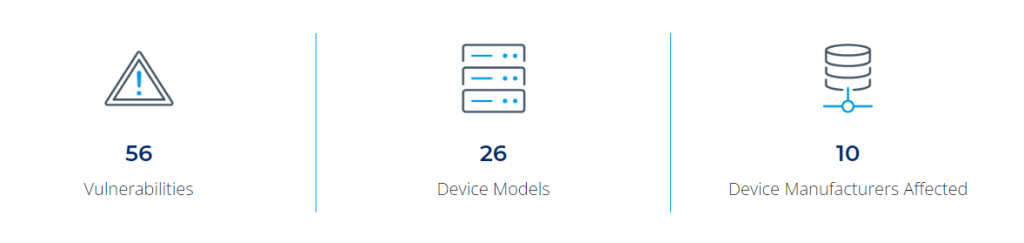
Security researchers at Vedere Labs (part of Forescout Technologies) have recently released details of 56 different vulnerabilities across 10 OT (Operational Technology) companies devices in a security brief called ICEFALL in an attempt to illustrate how the opaque and proprietary nature of such systems, the sub-optimal vulnerability management surrounding them, and the often-false sense of security offered by certifications significantly complicate OT risk management efforts.
What is ICEFALL?
Back in 2015, Digital Bond released a set of detailed data relating to the fragility and insecurity of SCADA and PLC systems. This release was known as Project Basecamp, and was the first of its kind – focusing on OT systems from manufacturers such as:
- 3S CoDeSys
- GE D20
- Koyo / DirectLOGIC
- Rockwell Automation ControlLogix
- Schneider Electric Modicon
Basecamp is the name given to the starting point for the ascent of Mt.Everest.
ICEFALL is the second stop on the climb, after basecamp and gives a sense of scale to the mountain that still needs to be climbed when it comes to OT security.
Main findings
Insecurity by design remains very relevant in OT
The past decade has shown that one of the biggest security problems in OT continues to be the lack of basic controls, and OT focused attackers have exploited this in practice.
Insecure-by-design vulnerabilities abound
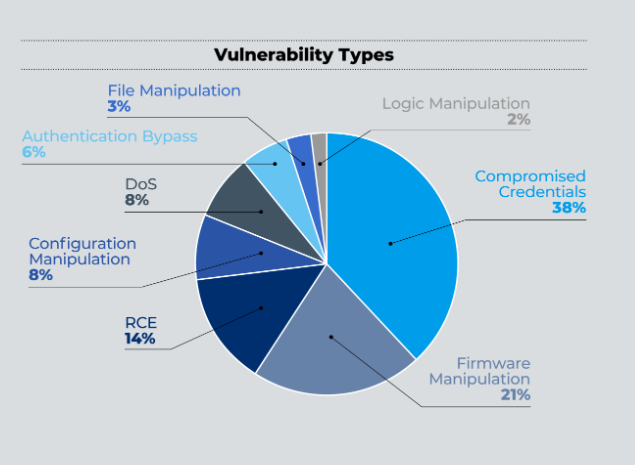
The researchers found 56 vulnerabilities affecting 10 major OT vendors. More than one-third of these vulnerabilities (38%) allow for compromise of credentials, with firmware manipulation coming in second (21%) and remote code execution coming third (14%). The prime examples of insecure-by design issues are the nine vulnerabilities related to unauthenticated protocols, but they also found many
broken authentication schemes, which demonstrates subpar security controls when they are implemented.
Vulnerable products are often certified
74% of the product families affected by the found vulnerabilities have some form of security certification and most issues should be discovered relatively quickly during in-depth vulnerability discovery.
Risk management is complicated by the lack of CVEs
It is not enough to know that a device or protocol is insecure. To make informed
risk management decisions, asset owners need to know how these components are insecure. Issues considered the result of insecurity by design have not always been assigned CVEs, so they often remain less visible and actionable than they should.
There are insecure-by-design supply chain components
Vulnerabilities in OT supply chain components tend to not be reported by every
affected manufacturer. We discuss two vulnerabilities with CVEs assigned to the ProConOS runtime that we often encountered in PLCs and RTUs without an associated CVE or public discussion that they were affected.
Not all insecure designs are created equal
Investigators looked at three main pathways to gaining RCE on level 1 devices via native functionality:
- logic downloads
- firmware updates
- memory read/write operations.
None of the systems analyzed support logic signing and most (52%) compile their
logic to native machine code. 62% of those systems accept firmware downloads via Ethernet, while only 51% have authentication for this functionality.
Offensive capabilities are more feasible to develop than often imagined
Reverse engineering a single proprietary protocol took between one day and two man-weeks, while achieving the same for complex, multi-protocol systems took 5
to 6 man-months. This shows that basic offensive cyber capabilities leading to the development of OT focused malware or cyberattacks could be developed by a small but skilled team at a reasonable cost
Vedere labs divided the vulnerabilities discovered into four categories:
- Insecure engineering protocols
- Weak cryptography / broken authentication schemes
- Insecure firmware updates
- Remote code execution
The uptick in the development of malware for OT systems shows that threat actors are well aware of the insecure by design nature of many OT systems, and it is reasonable to assume that a skilled team of hackers could write some basic offensive OT malware in a reasonably short timeframe.
It appears that very little has been done by the industry since project basecamp, but maybe OT:ICEFALL will have the desired effect and make manufacturters have a serious look at the systems they sell.












