(13-02-23) Blog 44 – The Not-so Magnificent Seven
Last week, the United Kingdom and the united states placed sanctions on seven Russian nationals who are behind at least two of the most virulent ransomware campaigns seen in recent years.

Members of the TrickBot cybercrime group whose malware campaigns supported attacks by the Conti and Ryuk ransomware operations have been placed under a series of sanctions in a first-of-its-kind collaboration between the U.S. Department of the Treasury’s Office of Foreign Assets Control and the U.K.’s Foreign, Commonwealth, and Development Office; National Crime Agency; and His Majesty’s Treasury.
Breakthrough for attribution
The sanctions come after a massive trove of internal conversations, and personal information was leaked in early 2022 from Conti and TrickBot members in what was called the ContiLeaks and TrickLeaks.
A Ukrainian security researcher leaked over 60,000 internal messages belonging to the Conti ransomware operation after the gang sided with Russia over the invasion of Ukraine.
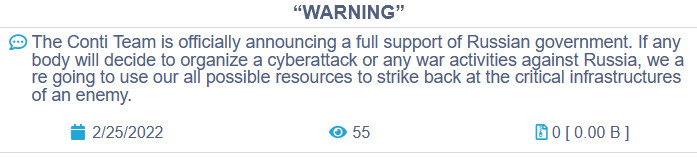
The leaked messages were taken from a log server (ejabberd database) for the Jabber communication system used by the ransomware gang.
The conversations contain various information about the gang’s activities, including previously unreported victims, private data leak URLs, bitcoin addresses, and discussions about their operations.
Whilst the ContiLeaks data dump focused on leaking internal conversations and source code, the TrickLeaks went one step further, with the identities, online accounts, and personal information of TrickBot members publicly leaked on Twitter.
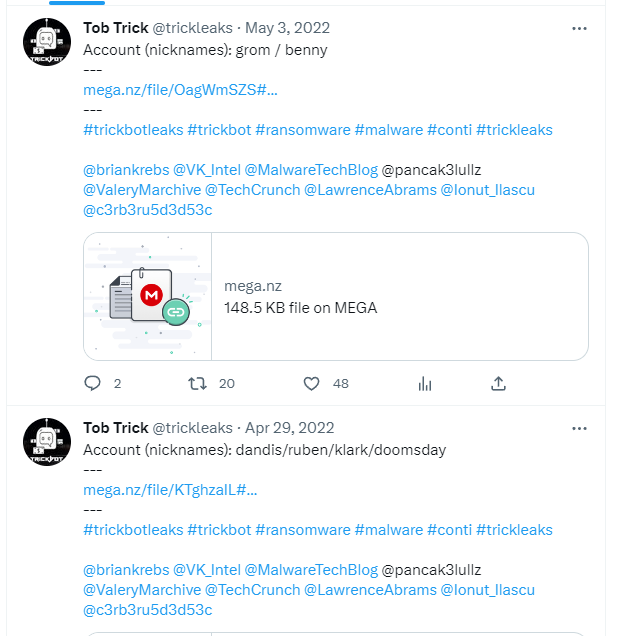
These data breaches ultimately led to the Conti gang shutting down their operation and their members starting new ransomware operations or joining existing ones.
As a result of these sanctions, all property and funds in the United States and the United Kingdom belonging to the following individuals have been blocked:
- Vitaly Kovalev (A.K.A. “Bentley” ,“Ben”, “Bergen”, “Alex Konor”) A senior figure within the Trickbot Group. Indicted for “conspiracy to commit bank fraud and eight counts of bank fraud in connection with a series of intrusions into victim bank accounts held at various U.S.-based financial institutions that occurred in 2009 and 2010”.
- Maksim Mikhailov (A.K.A. “Baget”) worked on development activity for the Trickbot Group.
- Valentin Karyagin (A.K.A. “Globus”) worked on the development of ransomware and other malware projects.
- Mikhail Iskritskiy (A.K.A. “Tropa”) contributed to money-laundering and fraud projects for the Trickbot Group.
- Dmitry Pleshevskiy (A.K.A. “Iseldor”) responsible for injecting malicious code into websites to steal victims’ credentials.
- Ivan Vakhromeyev (A.K.A. “Mushroom”) has worked for the Trickbot Group as a manager.
- Valery Sedletski (A.K.A. “Strix”) worked as an administrator for the Trickbot Group, including managing servers.
The sanctions released by the US / UK partnership also state that individuals and companies are blocked from performing transactions with the individuals named, including paying ransoms, and that any foreign financial institution that knowingly facilitates a significant transaction or provides significant financial services for any of the individuals or entities designated today could be subject to U.S. correspondent or payable-through account sanctions.”
Vitaly Kovalev is also said to have worked closely on Gameover ZeuS, a peer-to-peer botnet that was temporarily dismantled in 2014.
U.K. intelligence officials further assessed that the organized crime group has “extensive links” to another Russia-based outfit known as Evil Corp, which was also sanctioned by the U.S. in December 2019.
NOTE: I have an upcoming blog devoted to Evil Corp – hopefully I shall be in a position to release this in the next week or two.
The announcement is the latest salvo in an ongoing battle to disrupt ransomware gangs and the broader crime-ware ecosystem, and comes close on the heels of the take-down of Hive last month. [See my previous blog on Hive here]












