(11-02-23) Blog 42 – Healthcare & Finance companies attacked by Gootkit
Gootkit – a malware which has been around since 2014 has recently been seen to have adopted a new mechanism of deployment, and attackers are using it to deliver Cobalt Strike and SystemBC on compromised machines.
The new attacks have been exclusively targeting healthcare and finance organisations in the UK, The United States, and Australia.
Versatile malware
Originally, Gootkit was a banking trojan consisting of an x86 loader and a payload which embedded nodejs as well as a set of js scripts into victim browsers.
The loader downloaded the payload, stored it in the victims Windows registry and injected it in a copy of the loader process.
The loader contained two encrypted DLLs intended to be injected into each browser process launched in order to place the payload as a man in the browser and allow it to apply the webinjects received from the command and control server on HTTP exchanges.
This allowed Gootkit to intercept HTTP requests and responses, steal their content or modify it according to the webinjects.
Gootkit evolution
Over the past several years, Gootkit has evolved into a multi-stage tool used to facilitate a range of hands-on-keyboard activities in multi-pronged attacks, wherein more than one objective is likely accomplished.
Gootkit was originally delivered via spam email campaigns and older exploit kits, but over time its initial access has shifted towards Search Engine Optimisation (SEO) poisoning tactics where search engine results are altered to direct victims to legitimate, but compromised websites hosting Gootkit.
Upon visiting a compromised website, victims are prompted to download a ZIP archive containing a malicious JavaScript file, which if executed can allow an adversary to remotely access a victim’s system.
In the latest revision of Gootkit (also called Gootloader), heavily-obfuscated JavaScript files are served through compromised WordPress sites which have artificially been ranked higher in search engine results through poisoning techniques.
The attack chain relies on luring victims searching for agreements and contracts via DuckDuckGo and Google to the booby-trapped web page, ultimately leading to the deployment of Gootloader.
The latest Gootkit attacks are notable for concealing its malicious code within legitimate JavaScript libraries such as jQuery, Chroma.js, Sizzle.js, and Underscore.js, which is then used to spawn a secondary 40 MB JavaScript payload that establishes persistence and launches the malware.
The Gootloader infection paves the way for Cobalt Strike and SystemBC to conduct lateral movement in the victim network, and possible data exfiltration.
What is Cobalt Strike?
Cobalt Strike, developed by Fortra (formerly HelpSystems), is a popular adversarial framework used by pentesting red teams to simulate attack scenarios and test the resilience of cyber defenses.
The framework comprises a team server which acts as a command-and-control (C2) hub to remotely commandeer infected devices, and a stager which is designed to deliver a next-stage payload called the Beacon, which is a fully-featured implant that reports back to the C2 server.
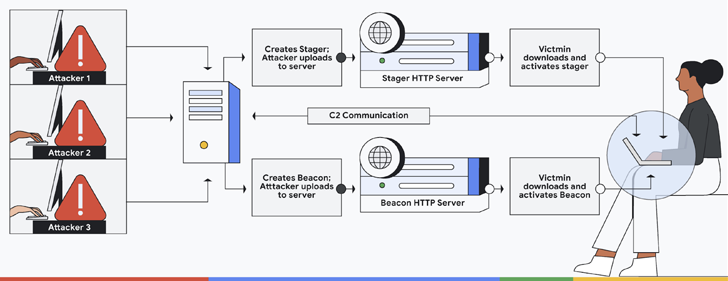
Given its wide-ranging suite of features, unauthorised versions of the Cobalt strike have been increasingly weaponised by threat actors to enhance their post-exploitation activities.
What is SystemBC
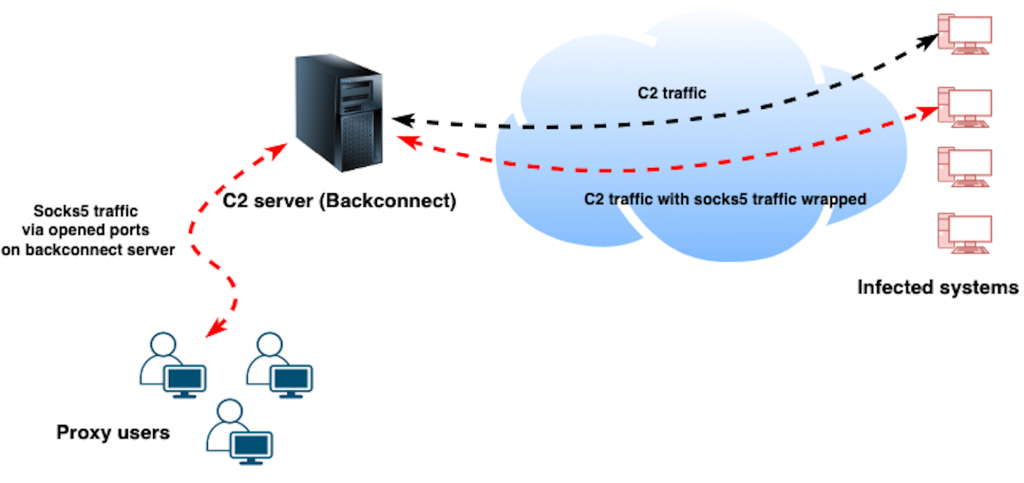
SystemBC is a malware written in the C programming language that turns infected computers into SOCKS5 proxies. Attackers communicate with the infected machines via a command and control server using a custom binary protocol over TCP with RC4 encryption.
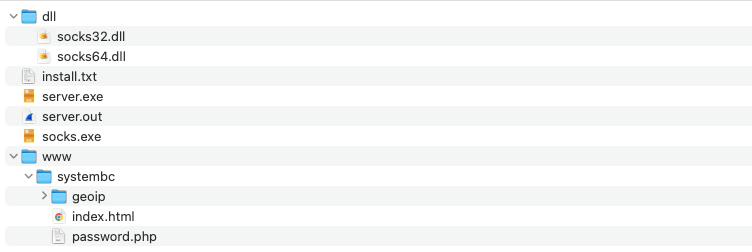
After purchasing SystemBC, the buyer receives an archive file containing the bot executable, the command and control (C2) server executable, and a PHP admin panel.
SOCKS5 proxy
A SOCKS5 proxy routes data packets from a specifically configured source through a remote server, and offers authentication methods to ensure that only authorised users can access this server. Whereas other types of proxies are limited to re-routing web-browser traffic, SOCKS5 proxies are more flexible.
SOCKS5 proxies can be configured to work with multiple protocols, which means they’re compatible with multiple types of applications, not just web browsers.
Be wary
Normally, the advise given for avoiding malware is to be cautious with unsolicited emails, and the links they contain. In the case of Gootkit however that advise won’t work because it’s not deployed via phishing emails, it’s deployed via compromised websites.
When reviewing the results of web searches, it is almost impossible to determine if a website is legitimate, or as been compromised to host malware. So how do you protect against an attack such as the one being used to deploy Gootkit?
The best you can do in such a case is ensure you have updated all your software to the latest security patches – especially your operating system and your browser. Additionally, ensure you have an up-to-date anti-malware solution running.
These fairly simple steps will go quite a long way to protecting against such an attack. But you still need to be wary with your online activities.












