(03-02-23) Blog 34 – $30 Web injects for sale
Research and analysis conducted by threat intelligence company Cyble reveals that over 1,890 web injects are for sale on Russian cybercrime forums for the low price of just $30 by a hacker who goes by the name InTheBox.
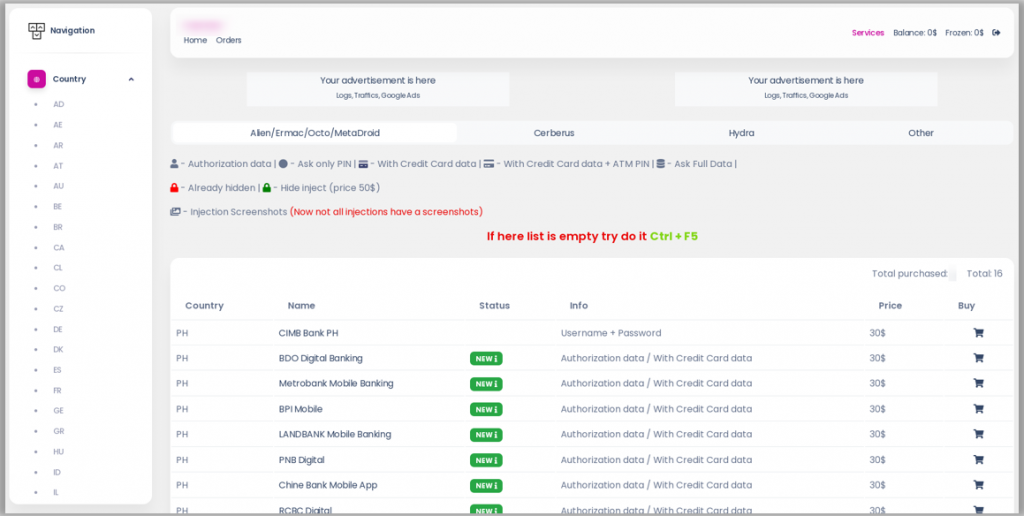
The available injects are compatible with numerous Android banking malware and mimic apps operated by banks, crypto-currency exchanges and other e-commerce apps.
What is a web inject?
A Web inject is a module or package used in malware (typically financial) that typically inject HTML or JavaScript code into web content before it’s rendered on a web browser.
As a result, web injects can alter what the user sees on their browser, as opposed to what’s actually sent by the server. For example, it can add or remove text, labels, text fields, and other elements.
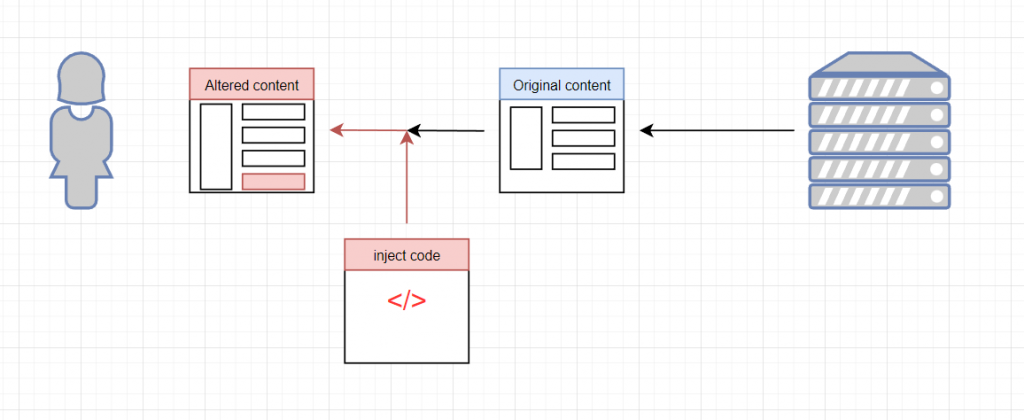
The malicious code is injected in the course of a legitimate transaction after a secure login. As such, the unwitting victim wouldn’t suspect anything is wrong and would usually enter the requested information.
Once the attackers get a hold of any information, they can then use that to perform unauthorised activities, such as carry out fraudulent transactions.
Typically, mobile trojan malware check what apps are present on an infected device and pull web injects corresponding to the apps of interest from a command and control server.
When the victim launches a target app, the malware automatically loads the overlay that mimics the interface of the legitimate product.
InTheBox is currently providing up-to-date injects for hundreds of apps.
As of January 2023 InTheBox lists the following web inject packages, updated as recently as October 2022:
- 814 web injects compatible with Alien, Ermac, Octopus, and MetaDroid for $6,512
- 495 web injects compatible with Cerberus for $3,960
- 585 web injects compatible with Hydra for $4,680
For those who don’t want to buy entire packages, InTheBox is providing the web injects individually for $30 each. The shop also allows users to order custom injects for any malware.
How does the malware get on a device?
If we take a look at the Ermac malware mentioned above. One of the first known infection methods seen was via a copy of the bolt food website in Poland.
The legitimate website is food.bolt.eu, whereas the attackers had created a clone of the site at bolt-food.site
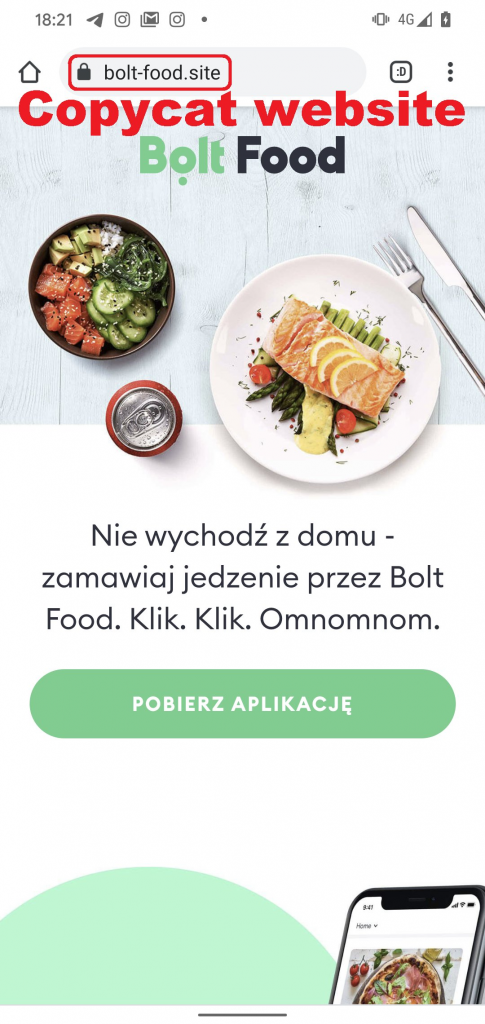
This fake site prompted people to download the bolt-food app from the website (as opposed to via the app-store, or play store), which was the malware-infected version.
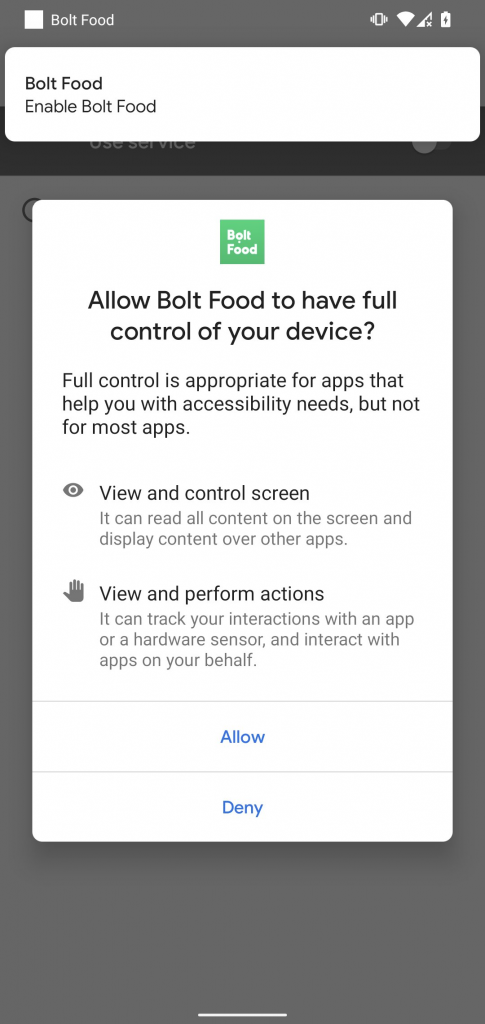
Granting access to the Accessibility Service is required for the malware to serve the web inject application overlays, tricking the victim into entering their credentials, etc.
On analysis of the malware, cyble found that Ermac grants itself 43 permissions upon installation (via Accessibility), including SMS access, contact access, system alert window creation, audio recording, and full storage read and write access.
Cyble has confirmed that InTheBox’s web injects have been used by the ‘Coper’ and the ‘Alien’ Android trojans in 2021 and September 2022, respectively, while the most recent campaign occurred in January 2023 and targeted Spanish banks.












