(30-01-23) Blog 30 – “It’s an older code, sir, but it checks out.”
Security researchers at Palo Alto Network’s Unit-42 were working on a response to a Black Blasta ransomware attack recently, and in the process of doing so, uncovered a new variant of a RAT (Remote access Trojan) which has been around since 2008.
The RAT, known as PlugX is capable of hiding malicious files on removable USB storage devices and then can infect any other Windows device the USB is plugged into.
Initially developed by Chinese hackers, the RAT also goes by the names Destroy RAT, Kaba, Korplug, Sogu, TIGERPLUG, and RedDelta, and has been widely used by many hacking groups including:
- APT22 – China based threat group – active since 2014 – Targets include political, military, economic entities in East Asia, Europe, and U.S.A.
- APT26 – Suspected to be a Chinese threat group targeting Aerospace, Defense, and Energy sectors
- APT31 – Suspected to be a Chinese threat group targeting Government, Finance, Aerospace, high-tech, construction, telecoms, media, and defense sectors
- APT41 – Suspected to be a Chinese threat group targeting various industry sectors in over 14 countries since 2012, including those in healthcare, telecoms, and high-tech sectors.
The capability set of the RAT, once on a target machine is not widely different to that of other RATS and gives the controlling operative the ability to:
- obtain machine information
- capture the screen
- send keyboard and mouse events
- perform keylogging
- reboot the system
- manage processes (create, kill and enumerate)
- manage services (create, start, stop, etc.); and
- manage Windows registry entries, open a shell, etc.
The new variant discovered by Unit-42 uses a Unicode whitespace character to create a new directory on a USB device which renders the directory “invisible” by Windows File Explorer and the Windows CMD shell.
PlugX infection technique
The hackers behind this new strain of PluX have hijacked an open-source Windows debugging tool called x64dgb – more specifically, the 32-bit version of the debugger – x32dbg.exe.
When the infected debugger is run on a Windows device, the Windows operating system will attempt to locate any file dependencies needed to run the software.
One of the dependencies is X32bridge.dll which is usually digitally signed and safe to run. In the case of PlugX however, this is a malware version which is not signed.
X32bridge will then locate an encrypted payload file known as x32bridge.dat
Samples of X32bridge.dat uploaded to VirusTotal has a detection score of only 12 out of 61 anti-virus engines.
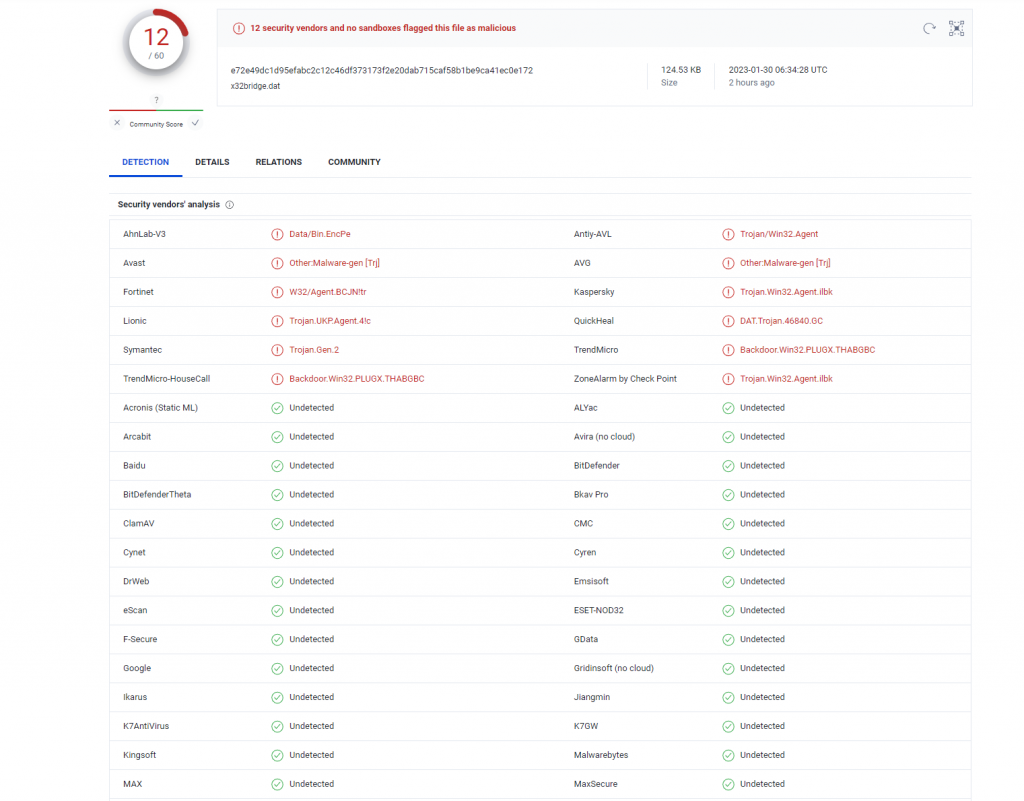
Once the payload executes the malware infects the host device, and any USB drives connected to it.
I’m the invisible man
The way in which this new strain of PlugX hides itself from Windows is by creating a directory containing the Unicode value of 00A0, which is the character codepoint for a no-break space. Windows operating systems cannot render this value which means that the folder is simply not displayed as opposed to showing a nameless folder.
To allow for the malicious code to be executed from an invisible folder, a Windows shortcut file (.lnk) is created in the root folder of the USB device. This creates a link to the malware payload which can be followed by Windows, it’s just not visible.
When the malware detects a USB drive, it follows the steps below to infect the device:
Step 1.
It creates the following directory structure:<usb volume>:\u00A0\u00A0\RECYCLER.BIN\files
E.G. F:\ \ \RECYCLER.BIN\files
Step 2.
It creates a hidden file named desktop.ini in each folder, which specifies the icon for the folder. This file contains the following data:
[.ShellClassInfo]
IconResource=%systemroot%\system32\SHELL32.dll,7
The Windows operating system uses a single file to retrieve icon images that are displayed on the desktop as shortcuts or from Windows Explorer files and folders. The Shell32.dll file contains a list of icons and a unique number. In this case, the drive icon and the number 7 are used.
Step 3.
In the second directory, it creates a sub-folder named RECYLER.BIN. This directory acts as a recycle bin. In that directory is a sub-directory named files and a hidden desktop.ini file. This desktop.ini file contains the following data:
[.ShellClassInfo]CLSID = {645FF040-5081-101B-9F08-00AA002F954E}
This CLSID instructs Windows Explorer to display the created RECYCLER.BIN folder as a recycle bin directory by giving it the recycle bin icon.
The files sub-folder contains copies of the PlugX malware x32dbg.exe, some encrypted .dat files and the actor’s malicious DLL.
Whenever the shortcut file from the infected USB device is clicked, the PlugX malware launches Windows Explorer and passes the directory path as a parameter.
This then displays the files on the USB device from within the hidden directories and also infects the host with the PlugX malware. The victim sees their files and assumes all is working as expected.
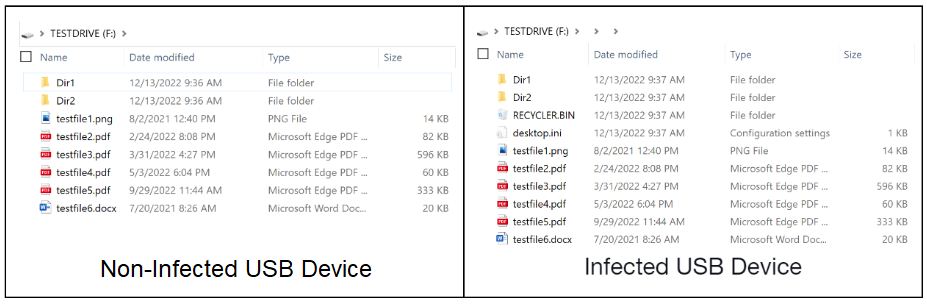
When a host is infected with this variant of the PlugX malware, the malware continuously monitors for USB removable devices. Once a USB device is discovered and infected, any new files written to the USB device root folder post-infection are moved to the hidden folder within the USB device.
Unit-42 also found versions of the new strain which scan the infected device for all .pdf and all .docx files and copy them to the infected device’s hidden folder.
Since the Windows shortcut file resembles that of a USB device and the malware displays the victim’s files, they unwittingly continue to spread the PlugX malware.
Just because something is old, it should not be considered out-of-date…












