(25-01-23) Blog 25 – Another cautionary tale
Back in December last year – between December 6th and 8th to be more precise, PayPal discovered that they had been on the receiving end of a cyber attack.
After conducting their internal investigations, it appears that approx. 35,000 users had had their accounts compromised and in the 2 day window in which the attackers had access, managed to obtain:
- Full names
- Date of Birth
- Postal address
- Social Security Numbers
- Tax identification numbers
- Transaction histories
- connected credit card / bank details
PayPal have said that there is no evidence of unusual transactions on any of the accounts has been seen.
The data obtained could be used by criminals to conduct fraudulent activities on other platforms. With the data obtained, criminals now have the ability to create completely legitimate-looking fake identities.
As part of the security investigation, PayPal have said that all the affected accounts have been accessed with valid credentials, and that those credentials have not been obtained from PayPal itself.
So how did it happen?
It appears that the attackers have used what is commonly termed in the cyber security world as a “credentials stuffing” attack to gain access to the accounts.
According to OWASP (The Open Web Application Security Project®), credential stuffing is the automated injection of stolen username and password pairs (“credentials”) in to website login forms, in order to fraudulently gain access to user accounts.
Attacks like this occur when hackers gain access to previously stolen credentials from other sites and then re-use them on different sites because they know that many people re-use the same credentials instead of generating new credentials for each website they use.
So, the cautionary tale here is to never reuse the same credentials across multiple accounts/websites. Generate a different set of credentials for each account.
Check to see if your accounts have been stolen
It is wise to do regular health checks on your online data, and one place to go to help do this is HaveIBeenPwned.com
This website is owned and managed by security researcher Troy Hunt as a side project to his day job working as a regional director for Microsoft.
He scours the dark web looking for data dumps where criminals share stolen databases of credentials, and adds them to his website.
If you enter your email address or mobile phone number in the site, it will conduct a look up to see if that data has been exposed in any number of security breaches.
If you find that your data has been leaked in a breach, it is advised that you change all passwords on any site which uses that data – just in case.
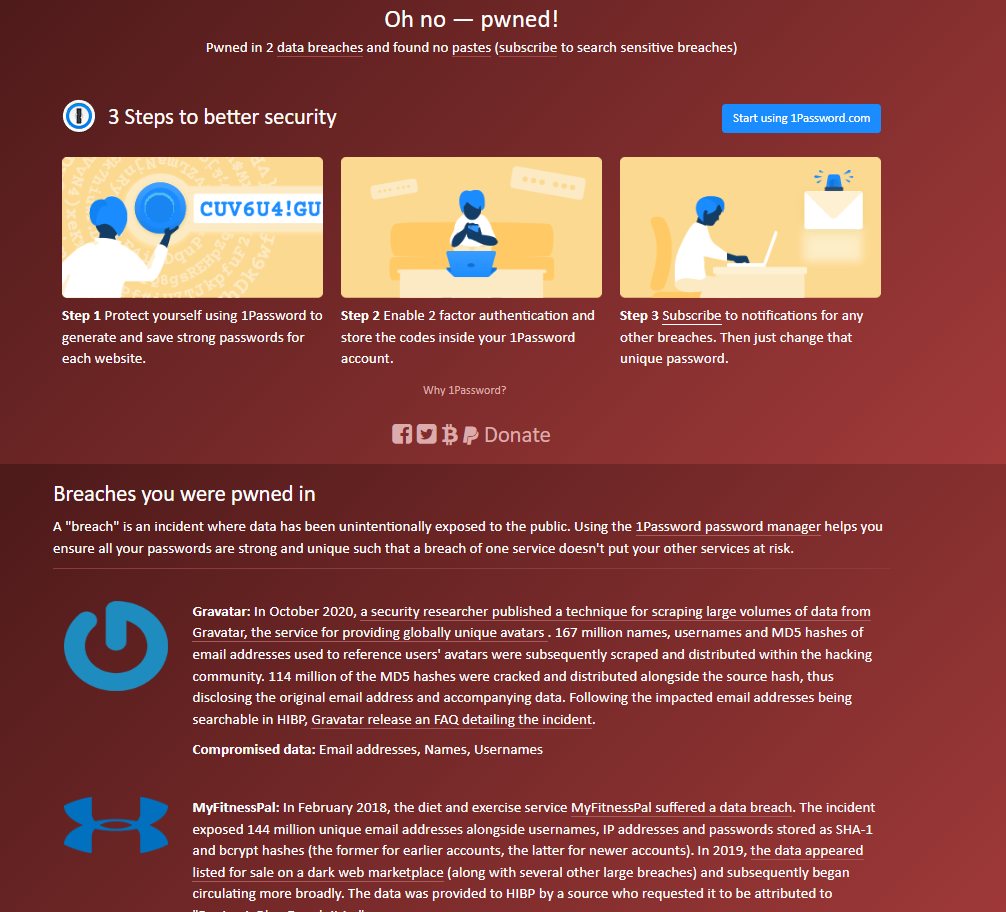
It must be noted that just because an email address is included in a breach, that the passwords associated with the account have been recovered – they should have been stored securely by the website, but that’s not always the case, and it’s just a matter of time before criminals manage to recover the plain-text passwords from their hashed versions.
Good advice to help you out
The NCSC has some great advice and guidance on passwords on their website:












