(21-01-23) Blog 21 – Download and be damned
It’s always been a bit tricky when you are looking for a new app to solve a problem. You do a Google search, you find a bunch of links, but which one is the right one?
It’s always been a bit like playing Russian roulette – Are you getting the correct version, or a cracked version full of malware?
Fortunately, Google has invested a huge amount of resource at cracking down on sites like this as part of their safe browsing technology and display warnings within the browser if a user attempts to connect to a potentially malicious website.
Details about how many warnings Google issue can be seen via the Google Transparency Report
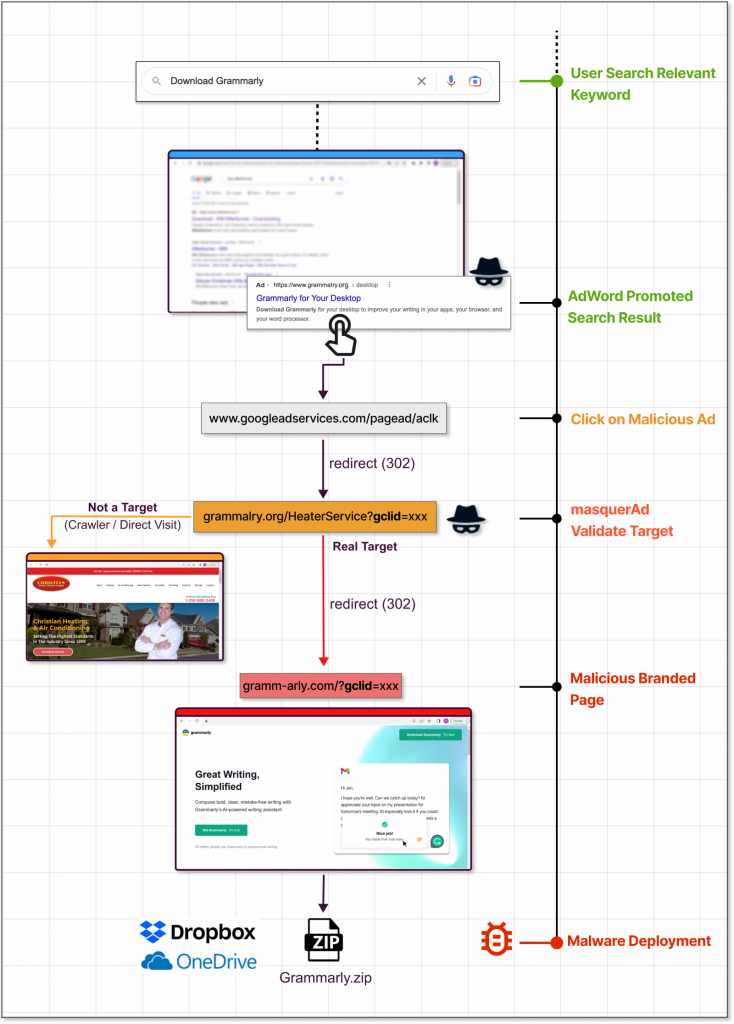
However, a new twist on this type of attack has started to surface in recent months whereby criminals are exploiting a loophole in how Google detects malicious domains.
Hiding behind trusted domains
The way this new attack works lies in the way people are redirected to the download they want.
So, a user searches for an application via Google. In the results page, a series of sponsored adverts prominently display the app at the top of the page.
The links to these pages take the user to a 100% benign site, thus avoiding Googles safe-browsing alerts. When the Google web crawler visits the site, it detects no signs of malware and as such does not add the domain to its safe browsing list of dodgy sites.
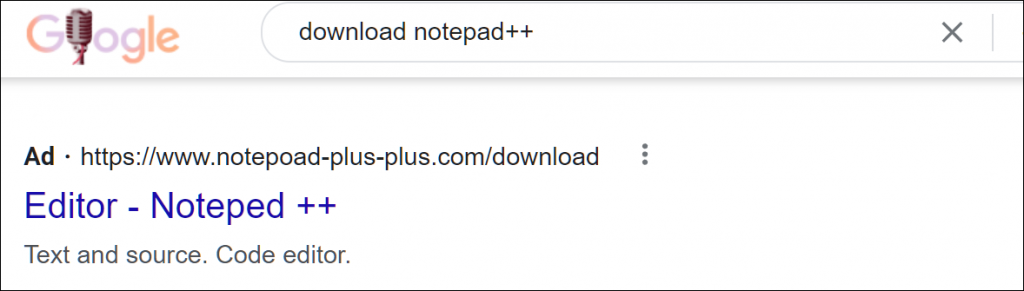
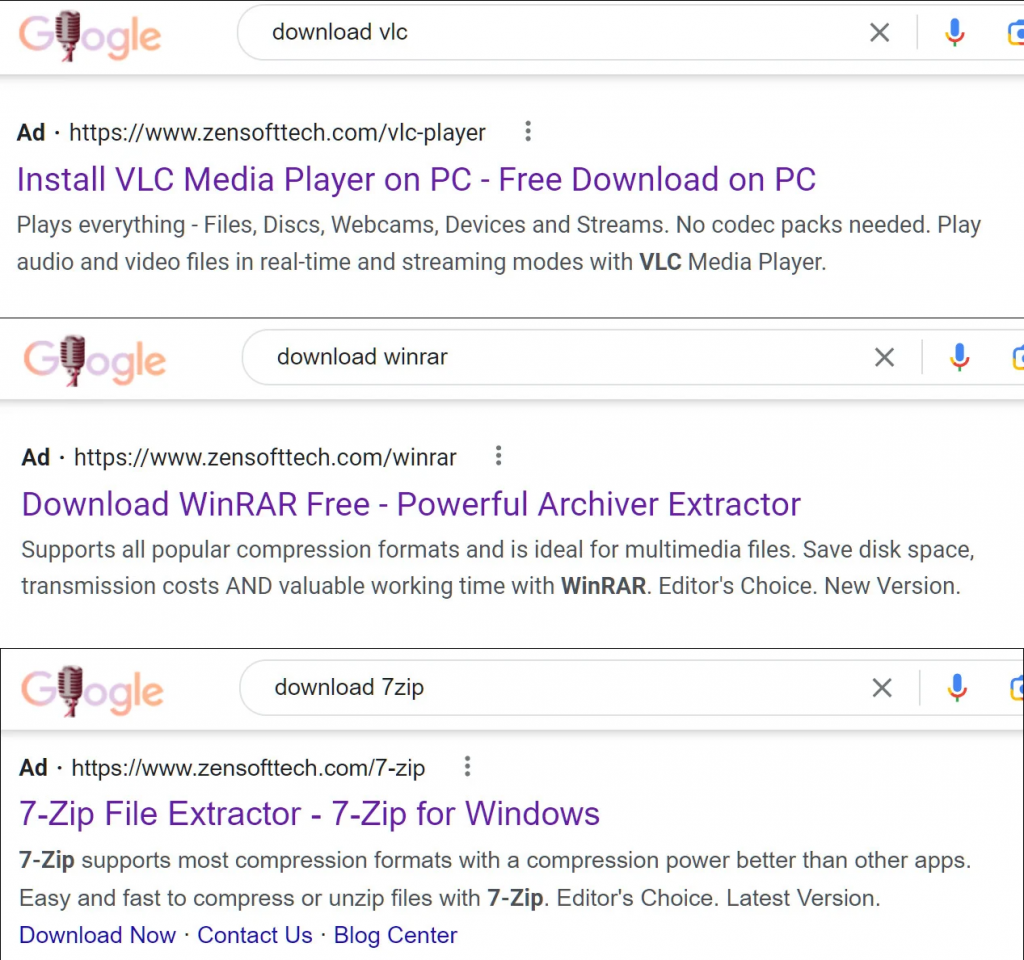
Due to how Google obtains revenue from advertising, adverts will always appear at the top of the results page – often above the true link to a manufacturers site.
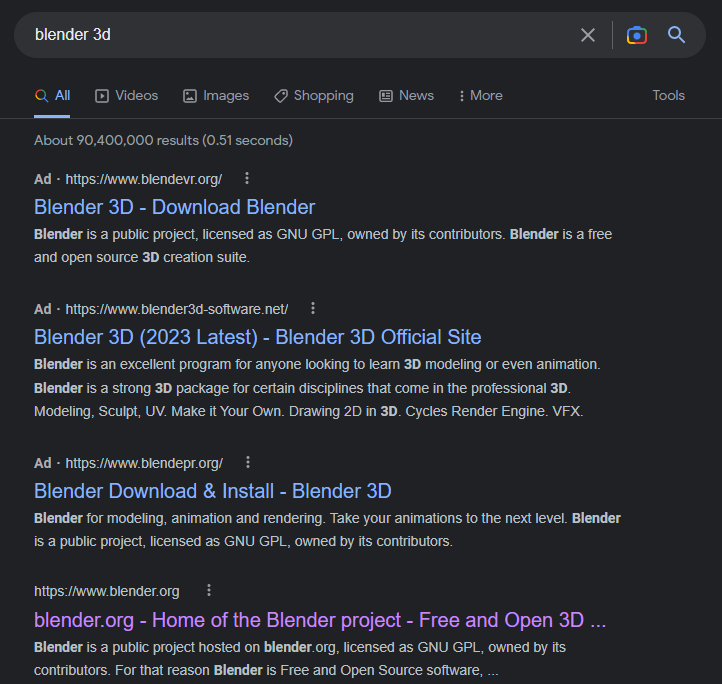
These sites however do not contain the application download, rather it contains a link to a second domain which contains the download which is packed with malware.
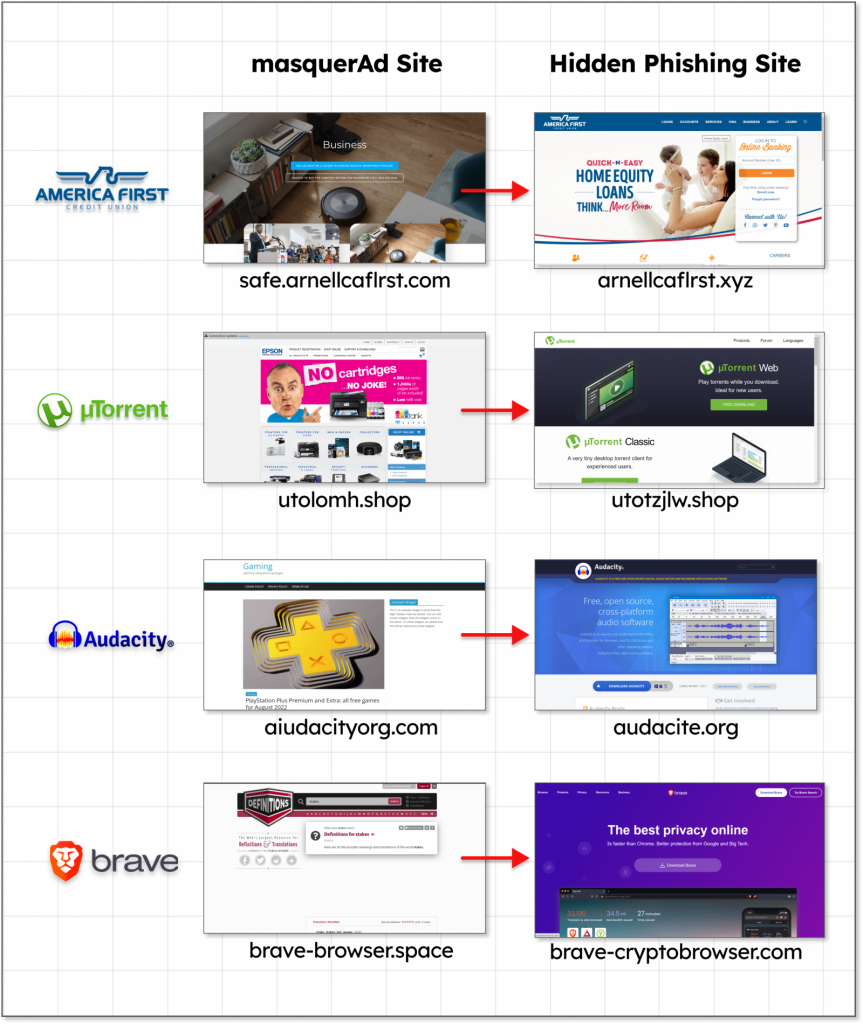
If a user follows the link, and performs the download, that’s when the malware gets deployed.
+1 for the pi-hole
If you followed my earlier blogs about building, configuring, and running a pi-hole, you would know that one of the things a pi-hole does is block Google ads.
With a pi-hole protected network, you will rarely see any google ads, and even if some get through, the pi-hole will block you from clicking on them – thus protecting you from accidentally visiting a malicious domain.
The security adage of Defense-in-depth is apparent here – using both the Google Safe Browsing, and a Pi-hole, you are using two levels of protection against would-be attackers.












