DNS
DNS, or the Domain Name System, is the system that translates human-readable website names (such as cybertrainer.uk) into the numerical IP addresses that computers on the Internet use to communicate with each other.
When you type a website name into your web browser, your computer sends a request to a DNS server to translate the name into the corresponding IP address.
The DNS server then responds with the IP address, and your computer uses that address to establish a connection to the server where the website is hosted.
Here is a brief overview of how DNS works:
- A user enters a website name into their web browser.
- The browser sends a request to a DNS resolver, asking for the IP address of the website.
- The DNS resolver checks its cache to see if it already knows the IP address for the website. If it does, it returns the IP address to the browser.
- If the DNS resolver does not have the IP address in its cache, it sends a request to a DNS root server.
- The root server responds with a referral to the appropriate top-level domain (TLD) server, based on the website’s TLD (e.g., .com, .net, .org, etc.).
- The TLD server responds with a referral to the authoritative name server for the website.
- The authoritative name server responds with the IP address for the website.
- The DNS resolver caches the IP address and returns it to the browser.
- The browser uses the IP address to establish a connection to the web server and request the website content.
DNS records
When a device transmits a DNS query, it typically would be asking for the IPv4 data associated with the domain. However, there are a number of other data that could be retrieved.
Each data item is recorded in a DNS record and there are are several types of DNS records, including the following:
- A record: Associates a domain name with an IPv4 address.
- AAAA record: Associates a domain name with an IPv6 address.
- CNAME record: (Cananonical Name)Maps a domain name to another domain name.
- MX record: Specifies a mail exchange server for the domain.
- TXT record: Stores text-based information, such as a description or instructions.
- NS record: Specifies the name servers for the domain.
- PTR record: Associates an IP address with a domain name.
- SOA record: Specifies the start of authority for a domain.
- SRV record: Specifies the location of a service, such as a server or website.
Each DNS record consists of a name, a class, a type, a time to live (TTL), and a value.
The name is the domain or hostname the record is associated with, the class is usually “IN” for Internet.
The type is the type of record (e.g., A, CNAME, MX, etc.), and The TTL is the length of time the record is cached on local DNS servers before it must be refreshed.
The value is the actual data for the record, such as an IP address or server name.
Root Servers
DNS root servers are the top-level servers in the Domain Name System (DNS) that directs traffic on the Internet.
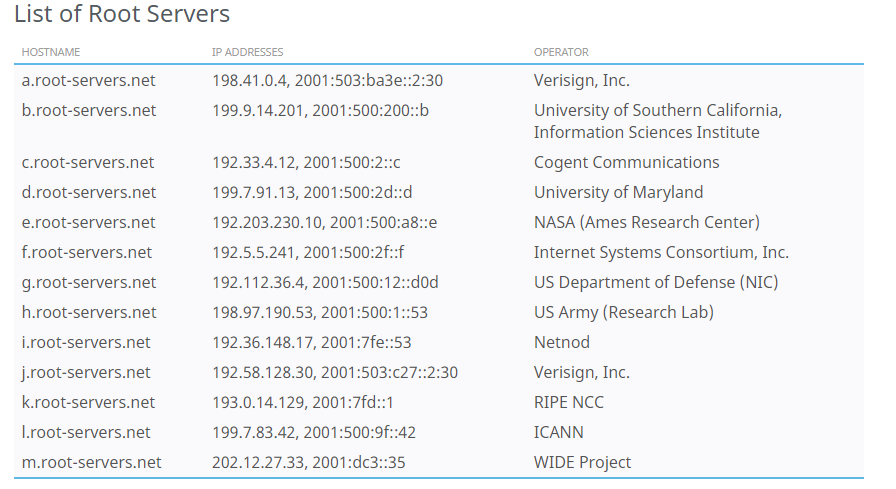
There are 13 logical root servers that are organised and operated by 12 independent organisations.
These root servers form the top of the DNS hierarchy and are responsible for providing the initial referral for all DNS queries.
The root servers are all names after letters in the Alphabet. The image below shows the 13 named root servers and their associated IP addresses along with the entity which is responsible for the maintenance of the server and its data.
Root server locations
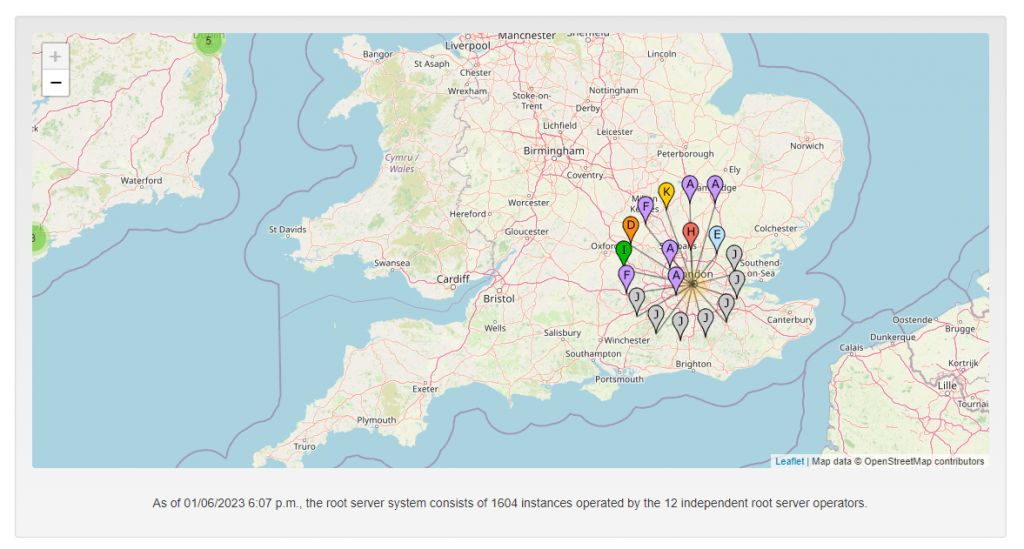
Whilst there are only 13 named root DNS servers, they are replicated all over the world in clusters giving a total of 1604 instances.
The locations of these clusters can be seen via the website root-servers.org
Querying DNS manually
It is possible to use command-line utilities to manually query DNS. On a Windows PC, the utility is called nslookup, whereas on a Linux machine, the common utility to use is called dig, although there are others.
Using nslookup
To use nslookup, you must first open a windows cmd prompt, or use the terminal application
The quick syntax is simply nslookup <domain name>
E.g. nslookup cybertrainer.uk
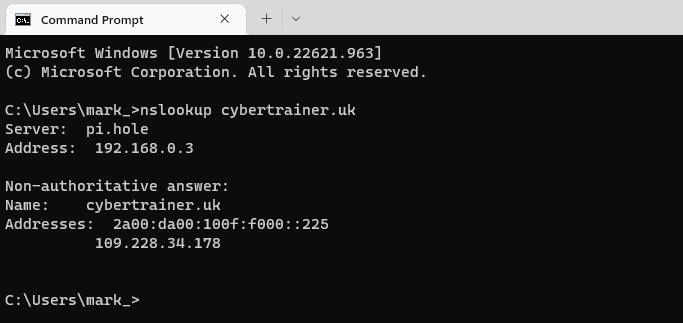
In the screenshot above, you can see the response for the DNS lookup stating that cybertrainer.uk has 2 IP addresses, an IPv4 and an IPv6 address.
You can also see that the answer is non-authoritative. this means that the server which gave the answer is not the authoritative name server for the cybertrainer domain and that the answer has been retrieved via a series of recursive lookups.
Another way to use nslookup is to enter the command nslookup with no data
By entering the nslookup command, we now have some options available which allow us to specify what type of record we wish to retrieve. Entering the ? character will display the list of possible commands/options
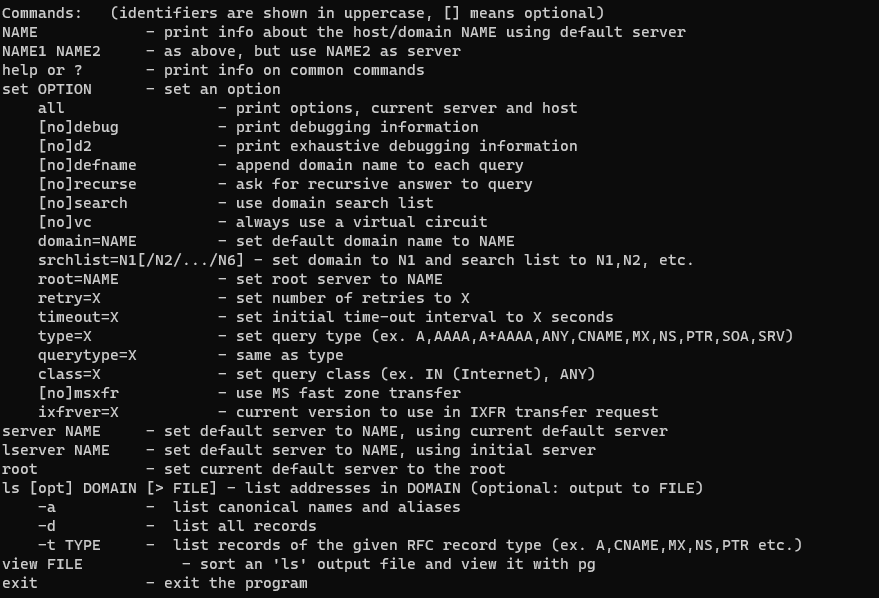
The most useful option to use is the set type option. This will allow you to retrieve different DNS records (if they are available).
In the screenshot below, I have set the record type to ns to try to retrieve the details of the authoritative nameservers for the cybertrainer.uk domain
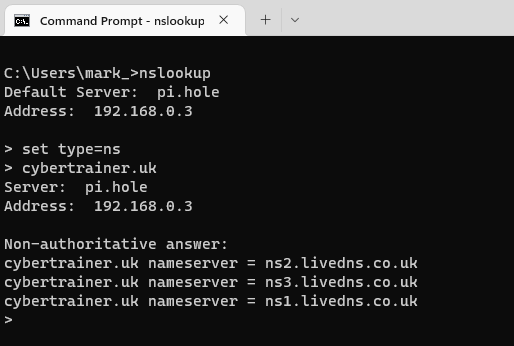
This tells me that there are 3 nameservers which are authoritative for the cybertrainer.uk domain
In the screenshot below I have set the type back to A to retrieve the IPv4 address of the ns1.livedns.co.uk server
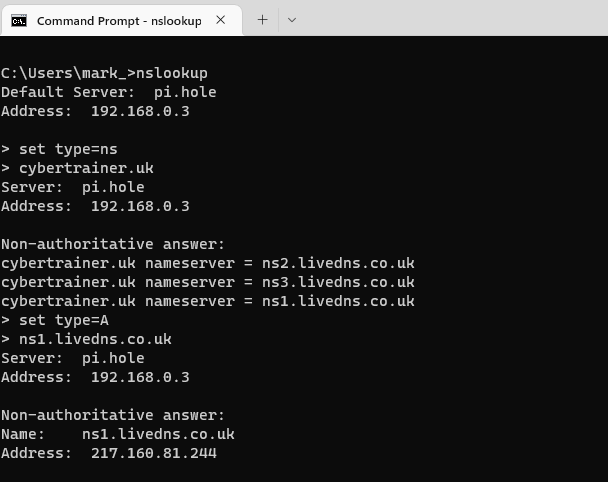
Now that I have the IP address of the nameserver I can go direct to the server with my query.
In the screenshot below, I have used the quick nslookup syntax as shown earlier, but I have appended the IP address of the ns1.livedns.co.uk to the query. this forces the query to go straight to that server as opposed to any other DNS resolver.
Because I have done this, the answer returned is now the authoritative answer.
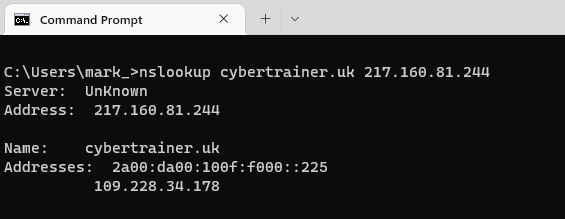
In most cases, performing a DNS lookup will involve entering a domain name to retrieve IP data. This is commonly referred to as a forward lookup.
It is possible to conduct a reverse lookup, which is where you enter an IP address to get the domain data as the answer.
However, this will only yield results if the DNS database holds a PTR (pointer) record.
In the screenshot below, I have queried the IP address for the cybertrainer.uk domain, but I receive an answer stating that this is a non-existent domain.
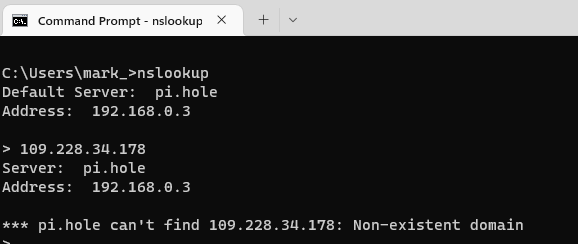
We know that the domain does exist, what this is saying is that the query cannot reverse the lookup back to a domain due to the lack of a PTR record
By setting the nslookup type to PTR and running a query, we can see that nop pointer record exists, so the results just bring back generic information about the cybertrainer.uk domain.
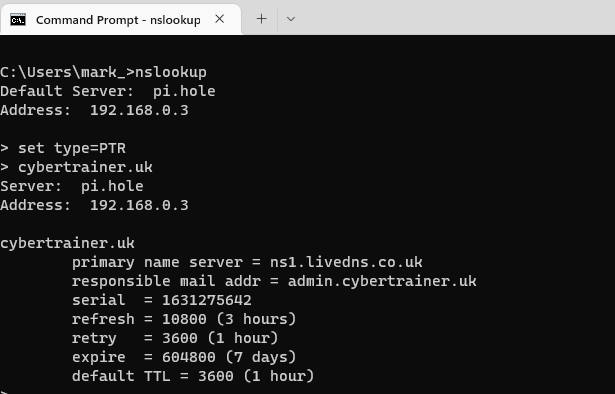
If we try to retrieve data for a domain which does have a PTR record such as qa.com, we get the following results:
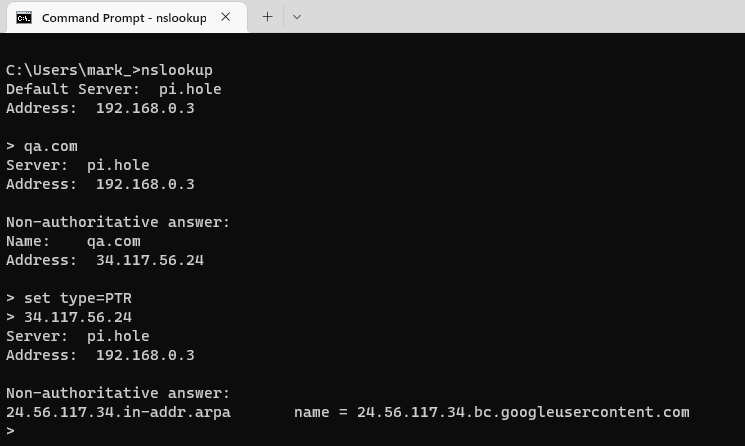
In this example, the qa.com IPv4 address is 34.117.56.24, so by performing a reverse lookup for that IP address retrieves the answer that the IP address is a part of the google domain (QA’s website is hosted in Google’ s cloud).
This data is recorded in the PTR record for the domain.
Hopefully this blog gives you a better understanding of the workings of DNS.