Pixnapping attacks target Android devices
A new side-channel attack has been discovered that affects Android devices and could allow a threat actor to steal sensitive data from victim devices without them knowing.
Called pixnapping, the attack analyses how pixels are rendered on a screen, and this data can be used to identify displayed data such as credit card information, MFA codes, passwords, and more.
The vulnerability (and attack) has been exposed by researchers at a number of US universities and can be read in full in their paper Pixnapping: Bringing pixel stealing out of the stone age [link here]
The title of the paper refers to the work described by Paul Stone at the 2013 Black Hat conference where he described a quirk in how web browsers render images encoded in the SVG format. Stone discovered that by measuring the time it took for a browser to render a morphological filter over a known set of pixels and then comparing this with the time taken to render the same filter over a pixel from an unknown website, he could infer the colour of the pixels. This allowed him to build a grayscale image of the other website which could be then used to leak information about the website.
Fortunately, this type of web-browser attack has been mitigated by most major browser manufacturers. This attack however focuses on how images are rendered on an android screen – browser, or otherwise.
The researchers have identified that the attack works on most, if not all Android-based mobile devices, including the Google Pixel (v6 – 9) and Samsung Galaxy devices running Android 13 – 16.
The vulnerability is recorded as CVE-2025-48561 and is outlined on the Google security bulletin here
So how does it work?
The victim installs a malicious app which can be disguised as a benign app, such as a game. The malicious app does not need any special permissions to operate.
Once installed, the malware uses standard Android APIs to invoke another app, such as Google Authenticator, Signal, or a banking app for example
The malicious app then overlays a stack of semi-transparent windows on top of the targeted app and uses a known GPU side-channel technique, (previously used in the 2023 “GPU.zip” attack), which exploits how a device’s graphics processing unit (GPU) compresses data.
The GPU zip attack affects GPUs from AMD, Apple, Arm, Intel, Qualcomm, and NVidia, so is likely to affect every GPU currently on sale today
By isolating and manipulating a single pixel at a time, the malware allows a threat actor the ability to measure the tiny variations in the rendering time of a frame. These timing patterns reveal the colour value of the pixel, from which, which the threat actor can piece together the information to reconstruct the on-screen image.
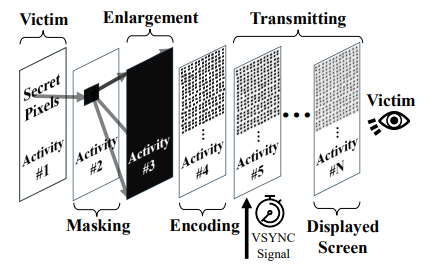
This inferred data is then processed using an optical character recognition-style technique to read text, such as an MFA code.
Google Authenticator codes refresh every 30 seconds, the researchers proved they could steal the code in as little as 14 to 26 seconds on various Pixel models.
A video produced by the researchers shows how the attack works.
Pixnapping demo – © Alan Wang, Pranav Gopalkrishnan, Yingchen Wang, Christopher W. Fletcher, Hovav Shacham, David Kohlbrenner, Riccardo Paccagnella
Currently the researchers state that they do not know if this attack is being used in the wild, but advise that users of affected devices should install patches as soon as they are published