(02-01-23) Blog 2 – Passwords
Sometimes called a passcode or a passphrase, passwords are supposed to be secret data typically used in association with an identity value (username, email address, etc.) to help secure a system such as a file, folder, phone, or PC, etc.
In days of yore, passwords were supposed to be values that could be memorised for the one or two systems that we used which required them. Today however, we have many hundreds of systems which require protection with such secrets.
Managing multiple passwords becomes problematic quite quickly, but there are some good options available to help you manage the plethora of credentials required for modern life, and towards the end of this blog I’ll outline some of those options.
First of all we need to understand that the point of a password is to secure a system so that unauthorised entities cannot gain access.
But how do unauthorised entities get access to our systems?
Typically they gain access because people don’t know what constitutes a good password and as such make some fundamental mistakes when creating accounts and using them.
Let’s look at the different ways passwords become compromised.
Guessing
A simple approach to compromising a password is so do some research into the owner of the password. People tend to be creatures of habit and very often will generate a password which to them is memorable. However, this tends to lead people to using a password which holds significance to them – child’s name, favourite sports team, first love, brand of car they drive, etc.
With a little bit of work (often called social engineering), it can be fairly trivial to build a list of possible passwords a person might choose.
A number of years ago, US TV chat show host, Jimmy Kimmel did a slot on his show highlighting how easy it can be to get people to reveal the passwords they use… (Youtube Link)
Password rule #1 – Don’t use easily guessable passwords
Common words / phrases
Millions of people use the same password. Various companies and researchers all over the world conduct analysis into what passwords are the most commonly seen in security breaches, and time and time again the results are the same…
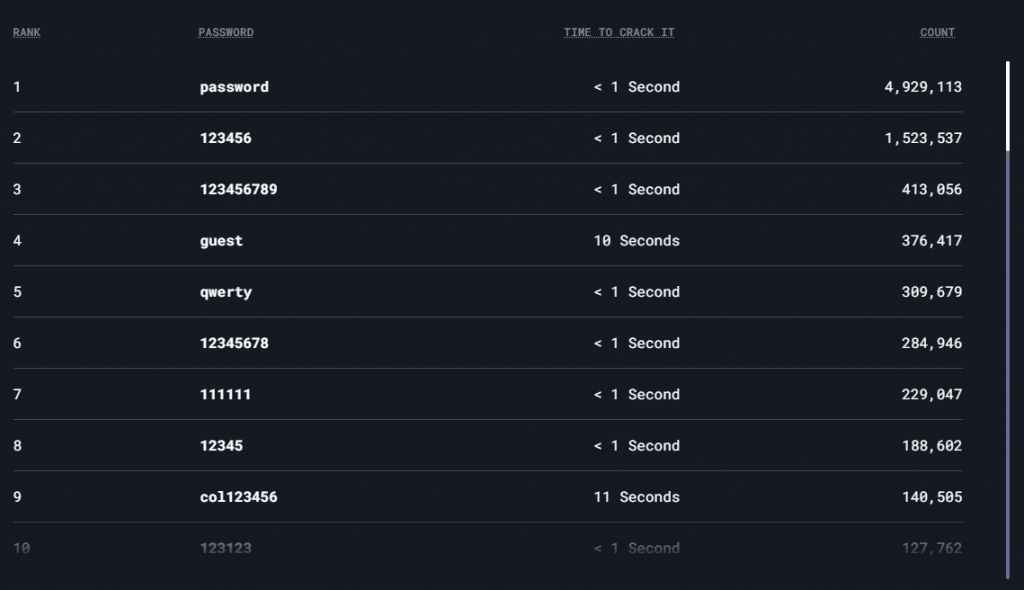
Password rule #2 – Don’t use common passwords
Single words
When you create a password on a system, that system will most likely store your data as a version of your password known as a hash (specifically, a hash digest)
To create a hash digest, the data is processed through a hashing algorithm which performs a number of operations on the data to change the output value significantly from the input data.
Hashing algorithms have a number of desirable attributes:
- The output digest will always be the same length, regardless of input value length
- The input value, if unchanged, will always produce the same output digest
- The hashing algorithm should be a one-way process. i.e. the digest should not be able to be reversed through the algorithm to recover the plain-text input.
- A minor change in the input value should have a massive change in the output digest – known as the avalanche effect
- No two (or more) different input values should ever produce the same hash digest – known as a hash collision
An example of a hashing algorithm which is no longer regarded as secure is MD5. In 1996, this algorithm was found to have a flaw that allowed for hash collisions to occur. Whilst MD5 is no longer regarded as a secure system to use, I will use it as an example in this blog.
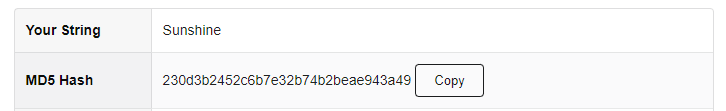
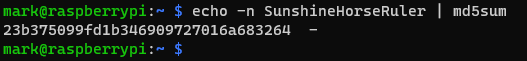
In the image below, I have used the website md5hashgenerator.com to produce a hash digest of the word “Sunshine”. The MD5 digest can be seen.
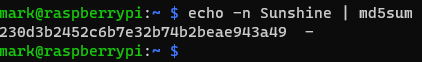
In the image below, I have used the MD5 hashing algorithm within Ubuntu to produce a hash digest of the word “Sunshine”. Note that the value is exactly the same as the one in the 1st image. This demonstrates desirable hash attribute No.2 from the list above.
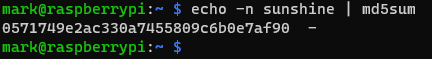
In the image below, I have used the MD5 hashing algorithm once again to produce a hash digest of the word “sunshine”. Note that the only difference in the input value is the lower-case letter “s”, yet the output digest is completely different – an example of desirable hash attribute No. 4 – the avalanche effect.
From these few images it can be seen that hashing algorithms, whilst great at producing altered outputs, will always produce known outputs.
If you took every single word from every single dictionary you would produce every single hash for a given hashing algorithm. As such, it wouldn’t take too much time to simply look-up a given hash digest to recover the original input value used to produce the digest.
In a very simplified way, this is what a rainbow-table attack does.
In an attempt to defeat a rainbow table attack, some systems add some random data to the hashing process which results in a hash that will never be the same.
This random data is known as a salt. In the image below, I have used the openssl hashing algorithm to produce a number of salted hashes of the word “Sunshine”
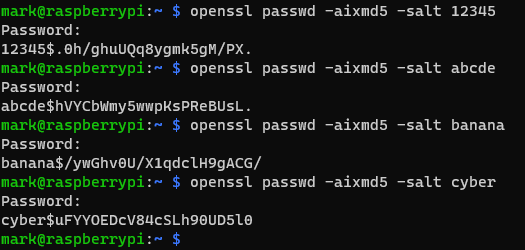
Notice how the hash digest changes with the use of different salts
Whilst this is a great way of protecting your data, the problem is that when you create a password on a system you do not own, you have no control as to whether the system uses a salt or not.
If it does, then that’s great. If it does not, hmmmm.
So, one solution that you can control is to add your own extra layer of randomness,.
Rather than use a single word as your password, use 2 or even 3 randomly paired words.
By doing this, you completely remove all risk associated with someone producing a rainbow table of every randomly paired set of words to produce every possible hash digest.
Three Random Words is the NCSC’s (The UK’s technical authority on cyber security) recommended approach to password security (NCSC link)
Password rule #3 – Don’t use single words
The use of multiple, randomly paired words also helps combat the final way passwords are often cracked – brute force.
When criminals retrieve password data, they will try the common passwords, the guessable passwords, and the rainbow table attacks, one of which will typically yield success.
However, if one of the above approaches don’t give the criminals access, then the final method is to try every possible character in every possible combination until they get success. An approach purely based on maths.
As an example, lets say your password consists of 1 character and only uses letters of the alphabet in either upper, or lower-case forms. In this case, the maximum number of tries to get the correct password is 52 (26 lower-case, 26 upper-case)
If you have a 2 character password, this now becomes 2,704 possible attempts (52 x 52 options, or 522)
A 3 character password now becomes 140,608 possibilities (52 x 52 x 52, or 523)
The more characters in the password, the harder it becomes to crack it. Using the example above (SunshineHorseRuler) gives a password with 18 characters (5218) which is 7,727,876,721,872,448,746,791,521,746,944 possible options.
As such, the length of the password is crucial in being able to defend against a brute-force attack
Password rule #4 – Make the password long
Losing access to one of your accounts is bad enough, but what about losing access to 6 or 7 of your accounts, or maybe even 20 or 30 of them?
Once a criminal successfully cracks a password, they will attempt to use the credentials to not only gain access to the system it was used to secure, but to also try to gain access to other systems, because they know that people very often reuse credentials across multiple accounts.
Password rule #5 – Never reuse passwords on multiple accounts
What solutions exist?
All the above ways a criminal could access your accounts means that we have to remember hundreds of unique, lengthy, random passwords – something that most people simply struggle with.
So what can we do to make things easier? Well, below are 3 things that are easy to do.
- Use a password manager
- Use a token-based system
- Use federated identity
Password managers
In it’s most simple guise, a password manager is a notebook, such as this one

(amazon link).
You might think that it’s bad advice to write passwords down, but it really isn’t. As long as you store your written passwords safely, then there is NOTHING wrong with recording passwords in the written form – but NOT like in the image below…

If your house is burgled, then I highly doubt a criminal would go looking for a book of passwords when there are much more interesting things to steal, such as your x-box, jewelry, iPhone, iPad, wallet, etc.
If you prefer a more digital form of password manager, then there are numerous options for you.
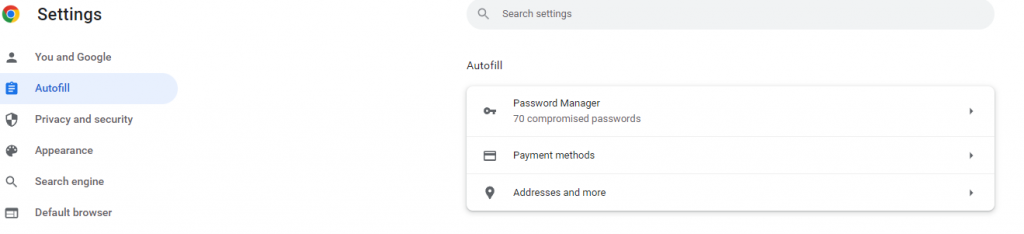
Modern browsers such as Microsoft Edge, or Google Chrome offer the ability to save website passwords in a secure part of the application. Many years ago, it was not advised to store passwords in your browser, but this is not the case with modern offerings. Google Chrome will even inform you if any of your stored passwords have been identified in any data breaches, giving you opportunity to reset your passwords on those sites where that password has ben used.
If you prefer not to trust your browser, then a dedicated password manager utility is the way to go. There are a wide range of password managers available from publishers such as Keeper, LastPass, DashLane, ZoHo, BitWarden, NordPass, 1Password, and others.
Choosing which one to use is a personal opinion, but things to think about are cost, cross-platform use, offline use, and digital legacy (i.e. the ability for a trusted individual to gain access if you are unable to do so).
Personally, I use KeePass which is a free, open-source utility available here but you should research which one suits your needs best.
Tokens
The use of a token in association with a password is becoming more and more commonplace, as more systems more towards a 2FA, or MFA approach (2-FActor, or Multi-FActor).
As mentioned before, if a criminal manages to recover one of your passwords, then have access to your account, by adding a 3rd or even 4th factor to the equation, it makes it much harder for anyone to get unauthorised access to your accounts.
The principles behind MFA are quite simple. Your accounts should be secured with a combination of the following things:
- Something you know – e.g. username / password
- Something you have – e.g. a token, a mobile device, a card reader, etc.
- Something you are – e.g. Your fingerprint, your iris pattern, your palm-print, etc.
If you have a mobile banking app, you might have noticed that occasionally when you make an online purchase, the website displays a message for you to approve the payment via your banking app?
In this case, the website sends a request for the payment to the bank, the bank sends your app (something you have) a token which you need to verify by logging into the app with either your password (something you know), or maybe your fingerprint (something you are). Once you approve the transaction, the app signs the token and sends it back to the merchant for them to finalise the transaction.
This is an example of multi-factor authentication with a one-time token sent to a device only you have access to. Providing a very high level of security around the activity.
Other examples of this include using the Google authenticator app, or the CISCO Duo authenticator app for example.
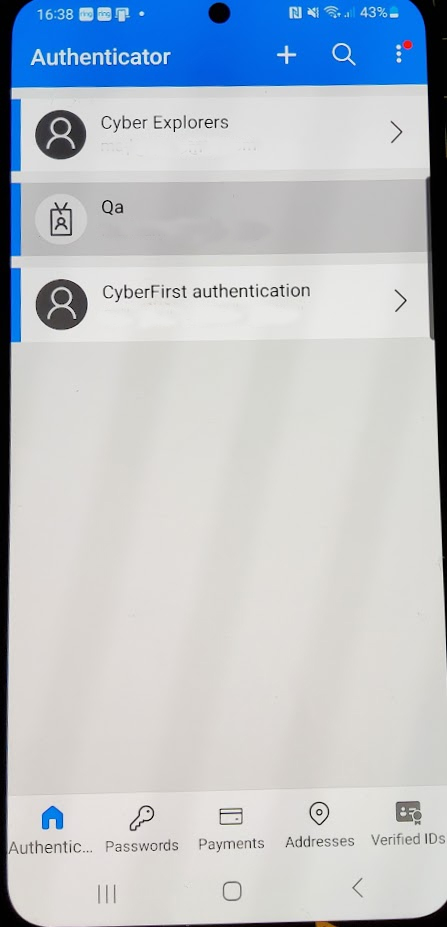
Once you have registered your chosen app with a service, every time you need to log in or perform a sensitive activity, you will be asked to verify the activity with the token sent to the app.
Federated identity
Another great option for securing accounts is to never create one in the 1st place, but to have a trusted 3rd party vouch for your trustworthiness
Let’s say you want to create 20 accounts on 20 different websites. That’s 20 different sets of credentials you have to remember, but also 20 different opportunities for hackers to get your credentials.
Now let’s say each one of those 20 websites give you the option to verify your identity via a well-known service such as Google, or Facebook.
By clicking one of the options (let’s use Google here), you are directed to the Google login page with a unique token from website 1. At this point you provide your Google credentials to prove to Google you are who you say you are.
Google now adds a signature to the token from website 1 saying that they trust you – as such, website 1 now also trusts you and you are given access.
You repeat this process with the other 19 websites.
This means you never give any of the 20 websites any password data, which means that there is no data to be stolen by would-be hackers. So long as your Google account stays secure, all your online accounts stay secure. You only need remember 1 password and 20 websites become accessible to you and only you.
There are lots of options available to users when it comes to protecting accounts – none of them offers a panacea to ultimate security, and hackers will continue to try to trick you into giving them access, be it by phishing you to click a link that grants them access, or by tricking you into sending them the security token from your bank.
The image below are some texts I received just before Christmas when some criminals tried to access my bank account. They were quite persistent and when I ignored their numerous attempts to contact me via my mobile number, they started phoning my landline. After 2 days of calls they finally gave up and moved onto their next potential victim.
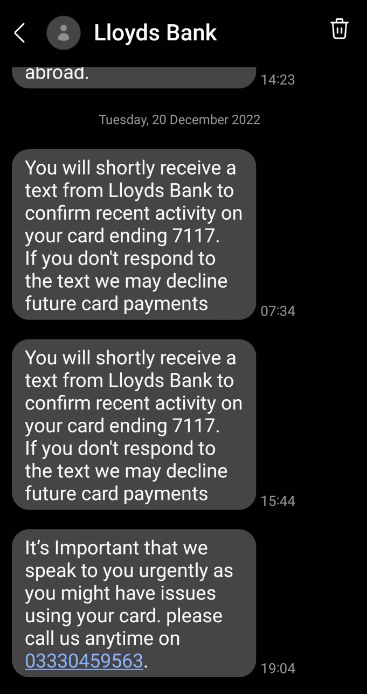
I wasn’t fooled, but I did contact my bank so that they were aware of the activity and they would monitor my account for a few weeks or so for unusual transactions.
So long as you are careful with who you share data with, and follow the password rules outlines at the beginning of this blog, you should be able to stay 1 step ahead of the criminals
Thanks for reading all the way to the bottom of this blog – I hope it was informative, and helps you stay safe… See you in the next post!












