(07/12/23) Blog 341 – LogoFail firmware attack has capability to affect every PC on planet
A new threat has emerged which has the potential to impact every PC in use today.
The attack (dubbed LogoFAIL by the researchers at Binarly who identified it) executes malicious firmware early in the boot-up sequence of vulnerable devices.
A full write up of the issue can be read via the Binarly research blog
As its name suggests, LogoFAIL involves logos, specifically those of the hardware seller that are displayed on the device screen early in the boot process, while the Unified Extensible Firmware Interface (UEFI) is running.

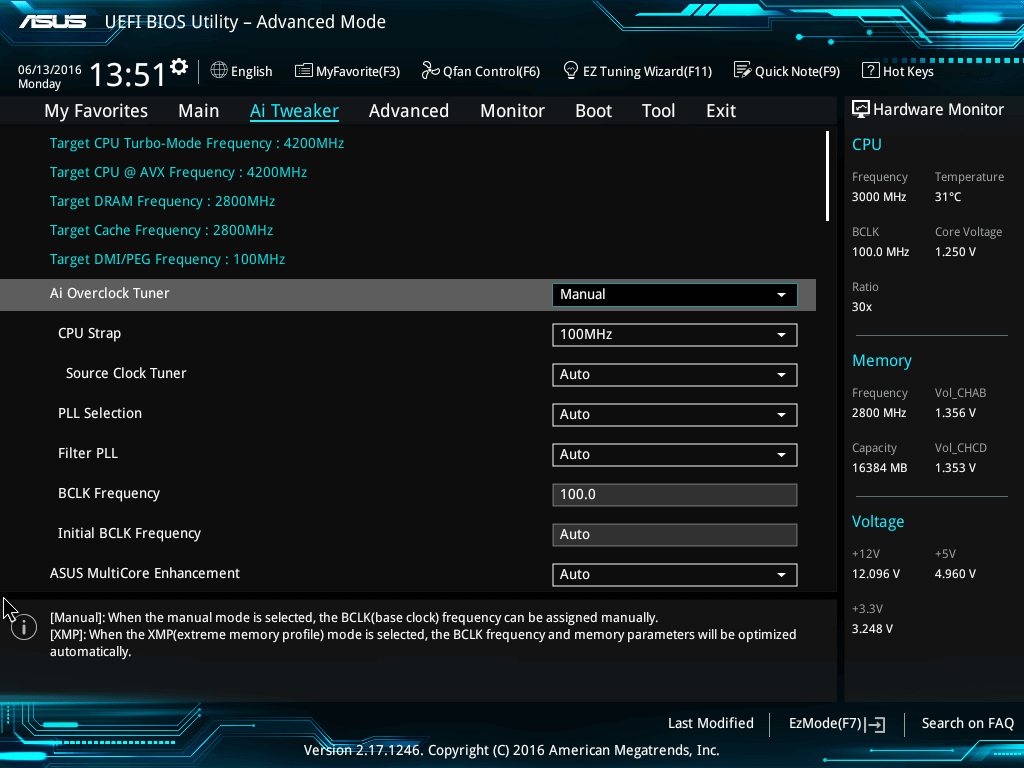
Image parsers in UEFIs from all three major Independent BIOS Vendors (IBVs) – AMI, Insyde, and Pheonix – have been identified as having a dozen critical vulnerabilities that have gone unnoticed until now. A coordinated mass disclosure of these vulnerabilities was released on Wednesday (6th December)
By replacing the legitimate logo images with identical-looking ones that have been specially crafted to exploit these bugs, LogoFAIL makes it possible to execute malicious code at the most sensitive stage of the boot process – Driver Execution Environmen (DXE).
Difficult to detect
In many cases, LogoFAIL can be remotely executed in post-exploitation situations using techniques that can’t be spotted by traditional endpoint security products. Because the exploits run during the earliest stages of the boot process, they are able to bypass a host of defenses, including the industry-wide Secure Boot and other similar protections from other companies that are devised to prevent bootkit infections.
Once arbitrary code execution is achieved during the DXE phase threat actors have full control over the memory and the disk storage of the target device, which means control over the the operating system that will be booted.
LogoFAIL can deliver a second-stage payload that drops an executable binary onto the hard drive before the main operating system has started, thus compromising the system before any security defences have been loaded.
The following video demonstrates a proof-of-concept exploit created by the researchers at Binarly.
The infected device is a Gen 2 Lenovo ThinkCentre M70s running an 11th-Gen Intel Core with a UEFI released in June 2023. The system runs standard firmware defenses, including Secure Boot and Intel Boot Guard.
There are two ways to exploit LogoFAIL. A remote attacks would work by first exploiting an unpatched vulnerability in a browser or other app and use administrative controls gained to replace the legitimate logo image which is processed early in the boot process with an identical-looking one that exploits one of the parser vulnerabilities recently announced. The other way is to gain brief physical access to a vulnerable device while it’s unlocked and replace the legitimate image file with a malicious one.
The malicious image needs to be placed into the EFI System Partition (ESP) which is a region of the devices hard drive that stores the boot loaders, kernel images, device drivers, system utilities, and other data files needed before the main OS loads.
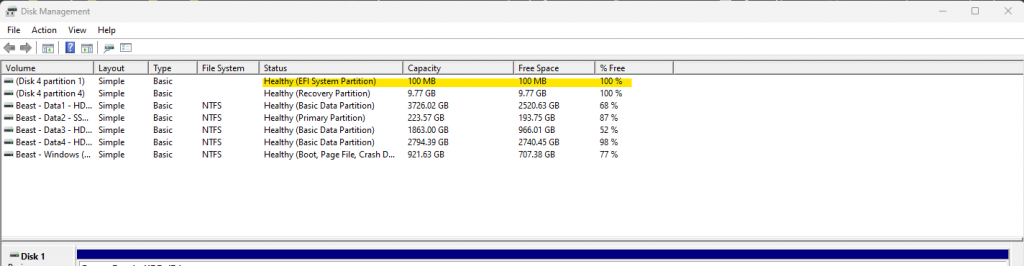
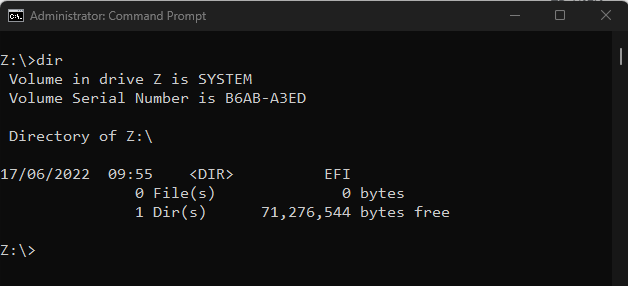
Accessing the EFI partition
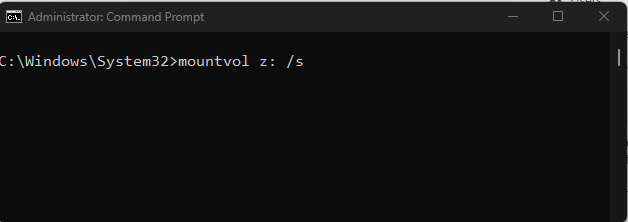
On a windows device, the EFI partition can be accessed by mounting the partition as an accessible drive. To do this launch the CMD prompt with administrative privileges and then use the mountvol command to mount the partition to a drive letter. The /s command is used to indicate the EFI partition is to be mounted.
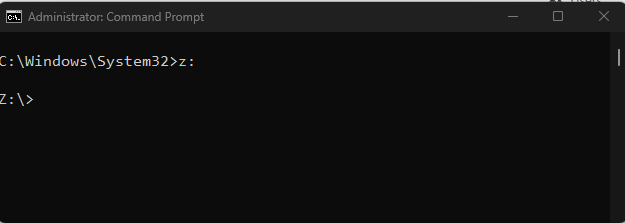
Once mounted, the drive can be chosen in the usual manner.
Difficult to detect & prevent
When UEFI-based system firmware is configured to use secure protections like Intel Boot Guard correctly with a non-modifiable logo, it’s not possible to place a malicious image into the ESP.
In many cases it is still possible to run software tools available from the IBVs which flashes the firmware direct from the operating system.
To pass security checks, these tools install the same cryptographically signed UEFI firmware already in use, but they include the malicious logo image which doesn’t require a valid digital signature.
In many cases, the IBV tools provided are digitally signed, making it less likely that endpoint protections will intervene to stop them from altering the firmware.