(25/05/23) Blog 145 – Vulnerability discovered in oAuth module
A critical vulnerability has been discovered in a widely used module used to implement the security authentication technology oAuth.
The vulnerability is being tracked as CVE-2023-28131 and is related to the Expo framework.
If exploited, the vulnerability can allow malicious actors the ability to gain complete control of a victims account leading to identity theft and fraud. In some instances, the vulnerability can also allow threat actors to perform actions under the guise of an affected victim on platforms such as Google, Facebook, Twitter and others.
What is oAuth?
OAuth (Open Authorisation) is an open standard framework that allows secure authorisation and delegated access to resources on the web. It provides a way for users to grant limited access to their protected resources (such as social media accounts, online services, or APIs) to third-party applications without revealing their credentials or passwords. OAuth is widely used by various websites and applications to enable users to log in or share information with other platforms.
How does it work?
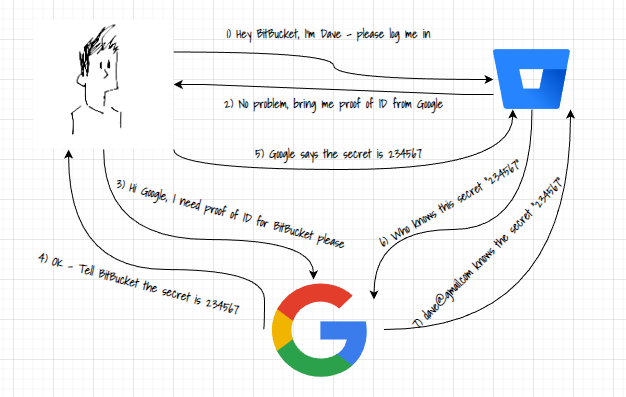
The core concept of OAuth revolves around the idea of granting access to resources through the use of tokens. The process typically involves three entities:
- The resource owner (the user)
- The client application (a third-party app)
- The resource server (the service hosting the protected resources)
The authorization process occurs as follows:
- When a user wants to access a resource using oAuth, they click the option to use the oAuth process.
- The resource asks for a secret from the users preferred oAuth service provider and is automatically re-directed to the service providers page
- The request is passed to the service providers oAuth service
- The service provider generates a unique secret token for the resource
- The data is passed back to the user and then automatically passed to the resource provider
- The resource provider checks the secret token with the oAuth service provider
- The oAuth service provider validates the identity of the owner of the token and passes data to the resource provider
By using OAuth, users can maintain control over their resources and authorise access on a per-application basis without sharing their login credentials. OAuth has become the industry standard for authentication and authorisation, providing a secure and standardised approach for enabling third-party integration and access to protected resources.
It allows for seamless integration between various platforms while maintaining user privacy and security.
Where does Expo come in to it?
Expo is a framework for developers building web apps that allows them to implement all the code necessary for oAuth to work with multiple oAuth service providers.
Note that the vulnerability here is NOT in oAuth, or any of the oAuth providers, or many apps which use the Expo framework. The vulnerability is in the Expo AuthSession Proxy component of the Expo framework and how it handles the data flowing back and forth between the app and the resource provider.
The vulnerability here is that once the oAuth service has generated the secret token, a malicious attacker can alter the web redirect so that the token generated is sent to a domain owned by the attacker.
The attacker then can present to token to the resource as if it came from the victim and thus gain access to an authorised session.
A full, technical breakdown of how this attack can play out is detailed at salt.security for those interested.
Who is affected?
Salt have not disclosed the names of any affected apps / sites, but state that during their research, they identified 34 companies and over 1,700 apps using the affected module.
As soon as the issue was discovered, Salt informed Expo and within hours the code was updated to removed the issue.
Work was conducted on the code base to re-write how the system manages data flow and two weeks after the vulnerability was discovered, Expo depreciated the code completely and informed developers not to use it.
This update however, does not stop existing apps using the outdated, and insecure version of the code, so developers are being urged to update their apps.












